k8s nginx ingress配置TLS
在没有配置任何nginx下,k8s的nginx默认只支持TLS1.2,不支持TLS1.0和TLS1.1
默认的 nginx-config(部分可能叫 nginx-configuration)的配置如下:
apiVersion: v1
data:
allow-backend-server-header: 'true'
enable-underscores-in-headers: 'true'
generate-request-id: 'true'
http-redirect-code: ''
ignore-invalid-headers: 'true'
max-worker-connections: ''
proxy-body-size: 20m
proxy-connect-timeout: ''
reuse-port: 'true'
server-tokens: 'false'
ssl-redirect: 'false'
worker-cpu-affinity: auto
kind: ConfigMap
metadata:
annotations:
kubectl.kubernetes.io/last-applied-configuration: >
{"apiVersion":"v1","data":{"allow-backend-server-header":"true","enable-underscores-in-headers":"true","generate-request-id":"true","ignore-invalid-headers":"true","max-worker-connections":"","proxy-body-size":"20m","proxy-connect-timeout":"","reuse-port":"true","server-tokens":"false","ssl-redirect":"false","worker-cpu-affinity":"auto"},"kind":"ConfigMap","metadata":{"annotations":{},"labels":{"app":"ingress-nginx"},"name":"nginx-configuration","namespace":"kube-system"}}
labels:
app: ingress-nginx
name: nginx-configuration
namespace: kube-system
selfLink: /api/v1/namespaces/kube-system/configmaps/nginx-configuration
看了下官方的文档,如果需要支持TLS1.0和TLS1.1需要改下 nginx-config 同时重启下容器即可
To provide the most secure baseline configuration possible,
nginx-ingress defaults to using TLS 1.2 only and a secure set of TLS ciphers.
The default configuration, though secure, does not support some older browsers and operating systems. For instance, TLS 1.1+ is only enabled by default from Android 5.0 on. At the time of writing, May , approximately % of Android devices are not compatible with nginx-ingress's default configuration. To change this default behavior, use a ConfigMap. A sample ConfigMap fragment to allow these older clients to connect could look something like the following:
kind: ConfigMap
apiVersion: v1
metadata:
name: nginx-config
data:
ssl-ciphers: "ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:AES:CAMELLIA:DES-CBC3-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!aECDH:!EDH-DSS-DES-CBC3-SHA:!EDH-RSA-DES-CBC3-SHA:!KRB5-DES-CBC3-SHA"
ssl-protocols: "TLSv1 TLSv1.1 TLSv1.2"
为了避免影响到之前的配置,切勿直接复制这个yaml配置替换你的配置!!!
在你原有的配置上加上 ssl-ciphers 和 ssl-protocols 配置即可
apiVersion: v1
data:
allow-backend-server-header: 'true'
enable-underscores-in-headers: 'true'
generate-request-id: 'true'
http-redirect-code: ''
ignore-invalid-headers: 'true'
max-worker-connections: ''
proxy-body-size: 20m
proxy-connect-timeout: ''
reuse-port: 'true'
server-tokens: 'false'
ssl-ciphers: >-
ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:AES:CAMELLIA:DES-CBC3-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!aECDH:!EDH-DSS-DES-CBC3-SHA:!EDH-RSA-DES-CBC3-SHA:!KRB5-DES-CBC3-SHA
ssl-protocols: TLSv1 TLSv1. TLSv1.
ssl-redirect: 'false'
worker-cpu-affinity: auto
kind: ConfigMap
metadata:
annotations:
kubectl.kubernetes.io/last-applied-configuration: >
{"apiVersion":"v1","data":{"allow-backend-server-header":"true","enable-underscores-in-headers":"true","generate-request-id":"true","ignore-invalid-headers":"true","max-worker-connections":"","proxy-body-size":"20m","proxy-connect-timeout":"","reuse-port":"true","server-tokens":"false","ssl-redirect":"false","worker-cpu-affinity":"auto"},"kind":"ConfigMap","metadata":{"annotations":{},"labels":{"app":"ingress-nginx"},"name":"nginx-configuration","namespace":"kube-system"}}
labels:
app: ingress-nginx
name: nginx-configuration
namespace: kube-system
selfLink: /api/v1/namespaces/kube-system/configmaps/nginx-configuration
加上配置之后呢,需要重启下容器 nginx-ingress
验证,能正常相应即可:
$ curl -v --tlsv1. https://test.com
$ curl -v --tlsv1. https://test.com
$ curl -v --tlsv1. https://test.com
下图是成功访问的响应:
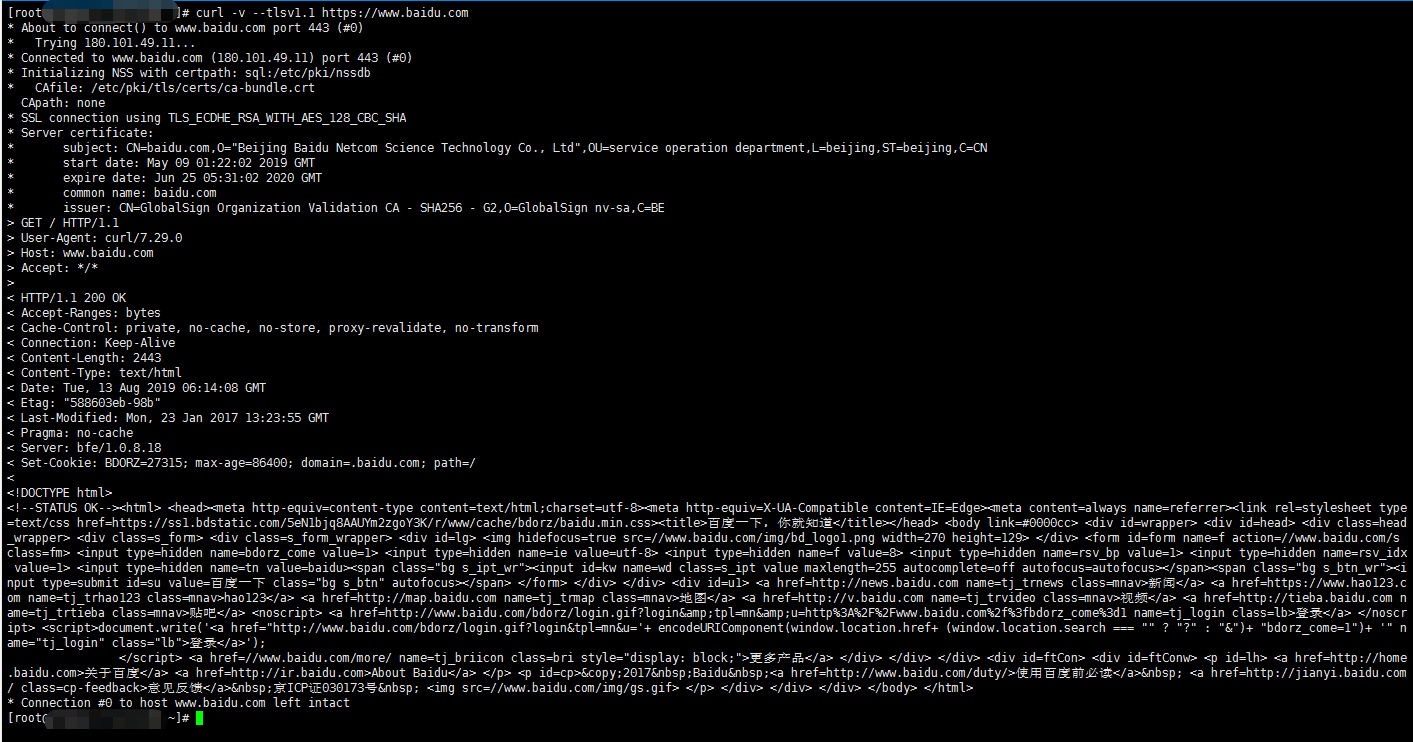
下图是错误的响应:

参考文档:https://kubernetes.github.io/ingress-nginx/user-guide/tls/#legacy-tls
k8s nginx ingress配置TLS的更多相关文章
- Kubernetes 部署 Nginx Ingress Controller 之 nginxinc/kubernetes-ingress
更新:这里用的是 nginxinc/kubernetes-ingress ,还有个 kubernetes/ingress-nginx ,它们的区别见 Differences Between nginx ...
- 微信小程序Nginx环境配置
环境配置概述 主要内容: SSL免费证书申请步骤 Nginx HTTPS 配置 TLS 1.2 升级过程 微信小程序要求使用 https 发送请求,那么Web服务器就要配置成支持 https,需要先申 ...
- Nginx Ingress 高并发实践
概述 Nginx Ingress Controller 基于 Nginx 实现了 Kubernetes Ingress API,Nginx 是公认的高性能网关,但如果不对其进行一些参数调优,就不能充分 ...
- [转帖]在 k8s 中通过 Ingress 配置域名访问
在 k8s 中通过 Ingress 配置域名访问 https://juejin.im/post/5db8da4b6fb9a0204520b310 在上篇文章中我们已经使用 k8s 部署了第一个应用,此 ...
- 见异思迁:K8s 部署 Nginx Ingress Controller 之 kubernetes/ingress-nginx
前天才发现,区区一个 nginx ingress controller 竟然2个不同的实现.一个叫 kubernetes/ingress-nginx ,是由 kubernetes 社区维护的,对应的容 ...
- k8s的ingress使用
ingress 可以配置一个入口来提供k8s上service从外部来访问的url.负载平衡流量.终止SSL和提供基于名称的虚拟主机. 配置ingress的yaml: 要求域名解析无误 要求servic ...
- Kubernetes 使用 ingress 配置 https 集群(十五)
目录 一.背景 1.1 需求 1.2 Ingress 1.3 环境介绍 二.安装部署 2.1.创建后端 Pod 应用 2.2 创建后端 Pod Service 2.3.创建 ingress 资源 2. ...
- 11. Ingress及Ingress Controller(主nginx ingress controller)
11. Ingress,Ingress Controller拥有七层代理调度能力 什么是Ingress: Ingress是授权入站连接到达集群服务的规则集合 Ingress是一个Kubernetes资 ...
- k8s系列---ingress资源和ingress-controller
https://www.cnblogs.com/zhangeamon/p/7007076.html http://blog.itpub.net/28916011/viewspace-2214747/ ...
随机推荐
- 【转】一文搞懂C语言回调函数
转:https://segmentfault.com/a/1190000008293902?utm_source=tag-newest 什么是回调函数 我们先来看看百度百科是如何定义回调函数的: 回调 ...
- lsattr 查看文件扩展属性
1. 命令功能 lsattr查看 是否有chattr设置的权限. 2. 使用范例 [root@localhost data]# lsattr resolv.conf -----a-------e- r ...
- windows 2003 系统管理员debug
- [php代码审计] Window api函数 FindFirstFile 在php中的问题
include文件夹中文件: 内容: <?php echo __FILE__; ?> index.php: 演示如下: “<<”替换多个任意字符: “>”替换单个字符:
- 将ubuntu系统迁移到ssd固态
朋友送了一个固态硬盘给我,因此将原机械硬盘上的系统迁移到固态硬盘上. 原机械硬盘(dev/sdb)装有win10和ubuntu双系统.分区情况如下: sda1:ESP分区 sda2:资料 sda3:资 ...
- finalize理论基础
参考: https://blog.csdn.net/aitangyong/article/details/39450341 https://www.infoq.cn/article/jvm-sourc ...
- flask之创建项目
一:安装flask workon flask_project 进入虚拟后安装flask pip install flask==0.10.1 安装指定的版本 进入虚拟环境的目录,查看创建的所有的虚拟环境 ...
- RMQ Topic
原创转载请注明出处:https://www.cnblogs.com/agilestyle/p/11794927.html RMQ Topic Project Directory Maven Depen ...
- 【leetcode】403. Frog Jump
题目如下: 解题思路:我的做法是建立一个字典dic,key为stone,value是一个set,里面存的是从前面的所有stone跳跃到当前stone的unit集合.例如stones=[0,1,2,3] ...
- 第四周作业—N42-虚怀若谷
一.统计出/etc/passwd文件中其默认shell为非/sbin/nologin的用户个数,并将用户都显示出来 [root@centos7 ~]# grep -v "/sbin/nolo ...
