nginx和keeplive实现负载均衡高可用
一、 Keeplive服务介绍
Keeplive期初是专门为LVS设计的,专门用来监控LVS集群系统中各个服务节点的状态,后来又加入VRRP的功能,因此除了配合LVS服务以外,也可以作为其他服务(nginx,haroxy)的高可用软件,VRRP是Virtual Router Redundancy Protocol(虚拟路由冗余协议)的缩写,VRRP出现的目的就是为了解决静态路由出现的单点故障问题,它能够保证网络的不间断,稳定的运行。所以keepalive一方面具有LVS cluster nodes healthchecks功能,另一方面也具有LVS directors failover
1.1 Keepalived的用途
Keepalive服务的两大用途:healthcheck和failover
ha failover功能:实现LB Master主机和Backup主机之间故障转移和自动切换
这是针对有两个负载均衡器Direator同时工作而采取的故障转移措施,当主负载均衡器失效或者出现故障时,备份的负载均衡器(BACKUP)将自动接管主负载均衡器的所有工作(vip资源以及相关服务):一旦主负载均衡器故障恢复,MASTER又会接管回它原来的工作,二备份复杂均衡器(BACKUP)会释放master是小事它接管的工作,此时两者将恢复到最初各自的角色
1.2 LVS cluster nodes healthchecks功能
在keeplive.conf配置记忆可以实现LVS的功能
keeplive可以对LVS下面的集群节点进行健康检查
rs healthcheck功能:负载均衡定期检查RS的可用性决定是否给其分发请求
当虚拟的服务器中的某一个甚至是几个真实的服务器同时出现故障无法提供服务时,负载均衡器会自动将失效的RS服务器从转发队列中清除出去,从而保证用户的访问不收影响;当故障的RS服务器被修复后,系统又自动的将他们加入转发队列,分发请求提供正常服务。
工作原理
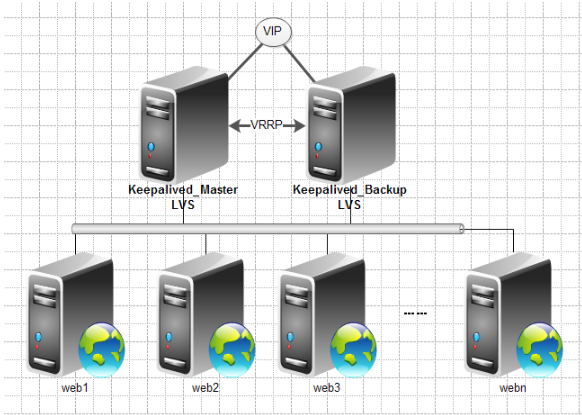
1.3 keepalive故障切换转换原理
Keepalived高可用对之间是通过 VRRP进行通信的, VRRP是遑过竞选机制来确定主备的,主的优先级高于备,因此,工作时主会优先获得所有的资源,备节点处于等待状态,当主挂了的时候,备节点就会接管主节点的资源,然后顶替主节点对外提供服务。
在 Keepalived服务对之间,只有作为主的服务器会一直发送 VRRP广播包,告诉备它还活着,此时备不会枪占主,当主不可用时,即备监听不到主发送的广播包时,就会启动相关服务接管资源,保证业务的连续性.接管速度最快可以小于1秒。
1.4 VRRP协议的简单介绍
1) VRRP,全称 Virtual Router Redundancy Protocol,中文名为虚拟路由冗余协议,VRRP的出现是为了解决静态路由的单点故障。
2) VRRP是通过一种竟选协议机制来将路由任务交给某台 VRRP路由器的。
3) VRRP用 IP多播的方式(默认多播地址(224.0_0.18))实现高可用对之间通信。
4) 工作时主节点发包,备节点接包,当备节点接收不到主节点发的数据包的时候,就启动接管程序接管主节点的开源。备节点可以有多个,通过优先级竞选,但一般 Keepalived系统运维工作中都是一对。
5) VRRP使用了加密协议加密数据,但Keepalived官方目前还是推荐用明文的方式配置认证类型和密码
二、配置Keepalived实现高可用
2.1 安装keepalive
[root@lb01 ~]# cd /usr/local/src/
[root@lb01 src]# wget https://www.keepalived.org/software/keepalived-2.0.15.tar.gz
[root@lb01 src]# tar -xf keepalived-2.0.15.tar.gz
[root@lb01 src]# cd keepalived-2.0.15
[root@lb01 keepalived-2.0.15]# ./configure
Linker flags : -pie
Extra Lib : -lm -lcrypto -lssl
Use IPVS Framework : Yes
IPVS use libnl : No
IPVS syncd attributes : No
IPVS bit stats : No
HTTP_GET regex support : No
fwmark socket support : Yes
Use VRRP Framework : Yes
Use VRRP VMAC : Yes
Use VRRP authentication : Yes
With ip rules/routes : Yes
With track_process : Yes
With linkbeat : Yes
Use BFD Framework : No
SNMP vrrp support : No
SNMP checker support : No
SNMP RFCv2 support : No
SNMP RFCv3 support : No
DBUS support : No
SHA1 support : No
Use JSON output : No
libnl version : None
Use IPv4 devconf : No
Use iptables : Yes
Use libiptc : No
Use libipset : No
Use nftables : No
init type : systemd
Strict config checks : No
Build genhash : Yes
Build documentation : No
[root@lb01 keepalived-2.0.15]# make
[root@lb01 keepalived-2.0.15]# make install
lb02相同操作
[root@lb02 ~]# cd /usr/local/src/
[root@lb02 src]# wget https://www.keepalived.org/software/keepalived-2.0.15.tar.gz
[root@lb02 src]# tar -xf keepalived-2.0..tar.gz
[root@lb02 src]# cd keepalived-2.0.
[root@lb02 keepalived-2.0.]# ./configure
[root@lb02 keepalived-2.0.]# make
[root@lb02 keepalived-2.0.]# make install
[root@lb01 keepalived-2.0.15]# vim /usr/lib/systemd/system/keepalived.service
[Unit]
Description=LVS and VRRP High Availability Monitor
After=syslog.target network-online.target
[Service]
Type=forking
PIDFile=/var/run/keepalived.pid
KillMode=process
EnvironmentFile=-/etc/sysconfig/keepalived
ExecStart=/usr/sbin/keepalived $KEEPALIVED_OPTIONS
ExecReload=/bin/kill -HUP $MAINPID
[Install]
WantedBy=multi-user.target
2.2 配置文件
[root@lb01 keepalived-2.0.15]# vim /etc/keepalived/keepalived.conf
! Configuration File for keepalived #!注释
global_defs { #全局变量
notification_email {
283365585@qq.com #收件人
} #邮件发件人
notification_email_from Alexandre.Cassen@firewall.loc
smtp_server 192.168.200.1 #邮件服务器地址
smtp_connect_timeout 30 #超时时间
router_id LVS_01
vrrp_skip_check_adv_addr
vrrp_strict
vrrp_garp_interval
vrrp_gna_interval
}
vrrp_instance VI_1 { #keepalive或者vrrp的一个实例
state MASTER #状态
interface ens33 #通信端口
virtual_router_id 51 #实例ID
priority #优先级
advert_int 1 #心跳的间隔
authentication { #服务器之间通过密码验证
auth_type PASS
auth_pass
}
virtual_ipaddress {
10.0.0.131 #VIP
}
}
2.3 启动看效果
[root@lb01 keepalived]# systemctl start keepalived
[root@lb01 keepalived]# ps -ef|grep keep
[root@lb01 keepalived]# ip addr
: lo: <LOOPBACK,UP,LOWER_UP> mtu qdisc noqueue state UNKNOWN qlen
link/loopback ::::: brd :::::
inet 127.0.0.1/ scope host lo
valid_lft forever preferred_lft forever
inet6 ::/ scope host
valid_lft forever preferred_lft forever
: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu qdisc pfifo_fast state UP qlen
link/ether :0c:::2e: brd ff:ff:ff:ff:ff:ff
inet 172.25.254.131/ brd 172.25.254.255 scope global dynamic ens33
valid_lft 1085sec preferred_lft 1085sec
inet 10.0.0.131/24 scope global ens33
valid_lft forever preferred_lft forever
inet6 fe80:::96e2:b57b:be1d/ scope link
valid_lft forever preferred_lft forever
: ens34: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu qdisc pfifo_fast state UP qlen
link/ether :0c:::2e: brd ff:ff:ff:ff:ff:ff
2.4 keepalive的VIP实现形式
[root@lb01 keepalived]# ifconfig ens33:0 10.0.0.18 up
[root@lb01 keepalived]# ip addr add 10.0.0.19 dev ens33
[root@lb01 keepalived]# ip addr
inet 172.25.254.131/ brd 172.25.254.255 scope global dynamic ens33
valid_lft 1583sec preferred_lft 1583sec
inet 10.0.0.131/ scope global ens33
valid_lft forever preferred_lft forever
inet 10.0.0.18/ brd 10.255.255.255 scope global ens33:
valid_lft forever preferred_lft forever
inet 10.0.0.19/ scope global ens33
valid_lft forever preferred_lft forever
inet6 fe80:::96e2:b57b:be1d/ scope link
valid_lft forever preferred_lft forever
[root@lb01 keepalived]# ip addr del 10.0.0.19 dev ens33
[root@lb01 keepalived]# ifconfig ens33:0 10.0.0.18 down
[root@lb01 keepalived]# scp /etc/keepalived/keepalived.conf 172.25.254.133:/etc/keepalived/
[root@lb02 ~]# vim /etc/keepalived/keepalived.conf
! Configuration File for keepalived
global_defs {
notification_email {
@qq.com
}
notification_email_from Alexandre.Cassen@firewall.loc
smtp_server 192.168.200.1
smtp_connect_timeout
router_id LVS_02
vrrp_skip_check_adv_addr
vrrp_strict
vrrp_garp_interval
vrrp_gna_interval
}
vrrp_instance VI_1 {
state BACKUP
interface ens33
virtual_router_id
priority
advert_int
authentication {
auth_type PASS
auth_pass
}
virtual_ipaddress {
10.0.0.131/
}
}
[root@lb02 ~]# systemctl start keepalived
[root@lb02 ~]# ps -ef |grep keep
配置成功
2.5 检测keepalibve效果
关闭MASTER的keepalive服务
[root@lb01 keepalived]# systemctl stop keepalived
[root@lb01 keepalived]# ip addr|grep 10.0.0.131
查看BACKUP端,是否有10.0.0.131
[root@lb02 ~]# ip addr|grep 10.0.0.131

[root@lb01 keepalived]# systemctl start keepalived

成功
三、 结合nginx实现高可用
3.1 配置
[root@lb01 keepalived]# cd /usr/local/nginx/conf/
[root@lb01 conf]# vim nginx.conf
worker_processes ;
events {
worker_connections ;
}
http {
include mime.types;
default_type application/octet-stream;
sendfile on;
keepalive_timeout ;
upstream web_pools {
server 172.25.254.134: weight=;
server 172.25.254.135: weight=;
# server 172.25.254.158: weight= backup; }
server {
listen ;
server_name www.lbtest.com;
location / {
# root html;
# index index.html index.htm;
proxy_set_header Host $host;
proxy_pass http://web_pools;
}
}
}
[root@lb01 conf]# scp nginx.conf 172.25.254.133:/usr/local/nginx/conf/
[root@lb01 conf]# nginx -s reload
[root@lb01 conf]# curl 172.25.254.134
172.25.254.134
[root@lb01 conf]# curl 172.25.254.135
172.25.254.135
[root@lb01 conf]# nginx -s reload
[root@lb02 ~]# curl 172.25.254.134
172.25.254.134
[root@lb02 ~]# curl 172.25.254.135
172.25.254.135
在获取到VIP后,不在同一网段,为了方便测试,把VIP设置为172.25.254.254
[root@lb01 ~]# ip addr|grep 172.25.254.254

3.2 发现不能访问的问题
访问测试,发现不能访问,也不能ping通
[root@lb01 conf]# curl 172.25.254.254
curl: () Failed connect to 172.25.254.254:; Connection timed out
[root@lb01 conf]# ping 172.25.254.254
packets transmitted, received, % packet loss, time 999ms
解决
[root@lb01 conf]# vim /etc/keepalived/keepalived.conf
# vrrp_strict # 注释掉vrrp_strict
[root@lb01 conf]# systemctl restart keepalived
3.3 测试
[root@lb01 conf]# curl 172.25.254.254
172.25.254.135
[root@lb01 conf]# curl 172.25.254.254
172.25.254.134
[root@lb01 conf]# curl 172.25.254.254
172.25.254.135
[root@lb01 conf]# curl 172.25.254.254
172.25.254.134
关闭MASTER测试
[root@lb01 conf]# systemctl stop keepalived #这时VIP已经在BACKUP上,但是可以正常访问
[root@lb01 conf]# curl 172.25.254.254
172.25.254.135
[root@lb01 conf]# curl 172.25.254.254
172.25.254.134
[root@lb01 conf]# curl 172.25.254.254
172.25.254.135
[root@lb01 conf]# curl 172.25.254.254
172.25.254.134
[root@lb01 conf]# curl 172.25.254.254
172.25.254.135
使用主机,域名访问
172.25.254.254 www.lbtest.com #写hosts



正常访问
四、keepalived的其他特性
4.1 监控自动迁移脚本
keepalived解决的是主机级别的冗余,当nginx宕掉的时候,keepalive并不会迁移,这时VIP依然在该主机上,客户就不能访问到网站
使用脚本监控,当nginx挂掉,自动停掉keepalive,是VIP漂移,是业务不受影响
[root@lb01 conf]# mkdir /script
[root@lb01 conf]# vim /script/monitor.sh
#!/bin/bash
while true
do
if [ `ps -ef |grep nginx|grep -v grep |wc -l` -lt ]
then
systemctl stop keepalived
fi
sleep
done
[root@lb01 conf]# cd /script/
[root@lb01 script]# chmod +x monitor.sh
[root@lb01 script]# /script/monitor.sh &
关掉nginx
[root@lb01 script]# nginx -s stop
VIP漂移到BACKUP上
[root@lb02 ~]# ip addr|grep 254.254
inet 172.25.254.254/ scope global secondary ens33
访问:
[root@lb01 script]# curl 172.25.254.254
172.25.254.134
[root@lb01 script]# curl 172.25.254.254
172.25.254.135
[root@lb01 script]# curl 172.25.254.254
172.25.254.134
[root@lb01 script]# curl 172.25.254.254
172.25.254.135
4.2 keepalive高可用脑裂脚本
[root@lb01 script]# ps -ef |grep monitor
root : pts/ :: /bin/bash /script/monitor.sh
[root@lb01 script]# kill -
[]+ Killed /script/monitor.sh
[root@lb01 script]# ps -ef |grep monitor
root : pts/ :: grep --color=auto monitor
[root@lb01 script]# systemctl restart keepalived
[root@lb02 ~]# mkdir /script
检测脑裂脚本,实现形式,当BACKUP可以ping通主,但是VIP依然在BACKUP,则认定为脑裂
[root@lb02 script]# vim check_split_brain.sh
#!/bin/bash
while true
do
ping -c -W 172.25.254.131 &>/dev/null
if [ $? -eq -a `ip addr|grep 172.25.254.254|wc -l` -eq ]
then
echo "ha is split brain warning"
else
echo "ha is OK"
fi
sleep
done
[root@lb02 ~]# sh /script/check_split_brain.sh
ha is OK
ha is OK
[root@lb02 ~]# systemctl start firewalld
ha is split brain warning
ha is split brain warning
[root@lb02 ~]# ip addr |grep 172.25.254.254
inet 172.25.254.254/ scope global secondary ens33
[root@lb01 ~]# ip addr |grep 172.25.254.254
inet 172.25.254.254/ scope global secondary ens33
[root@node4 ~]# systemctl stop firewalld
ha is OK
ha is OK
4.3 修改日志文件路径
配置文件默认在/var/log/messages
[root@lb01 ~]# tail -f /var/log/messages
Apr :: node2 Keepalived_vrrp[]: Sending gratuitous ARP on ens33 for 172.25.254.254
Apr :: node2 Keepalived_vrrp[]: Sending gratuitous ARP on ens33 for 172.25.254.254
Apr :: node2 Keepalived_vrrp[]: Sending gratuitous ARP on ens33 for 172.25.254.254
Apr :: node2 Keepalived_vrrp[]: VRRP_Instance(VI_1) Received advert with lower priority , ours , forcing new election
Apr :: node2 Keepalived_vrrp[]: Sending gratuitous ARP on ens33 for 172.25.254.254
Apr :: node2 Keepalived_vrrp[]: VRRP_Instance(VI_1) Sending/queueing gratuitous ARPs on ens33 for 172.25.254.254
修改日志文件位置
[root@lb01 ~]# vi /etc/sysconfig/keepalived
# Options for keepalived. See `keepalived --help' output and keepalived(8) and
# keepalived.conf() man pages for a list of all options. Here are the most
# common ones :
#
# --vrrp -P Only run with VRRP subsystem.
# --check -C Only run with Health-checker subsystem.
# --dont-release-vrrp -V Dont remove VRRP VIPs & VROUTEs on daemon stop.
# --dont-release-ipvs -I Dont remove IPVS topology on daemon stop.
# --dump-conf -d Dump the configuration data.
# --log-detail -D Detailed log messages.
# --log-facility -S - Set local syslog facility (default=LOG_DAEMON)
# KEEPALIVED_OPTIONS="-D -S 0 -d"
[root@lb01 ~]# vim /etc/rsyslog.conf
local0.* /var/log/keepalived.log
[root@lb01 ~]# systemctl restart rsyslog
[root@lb01 ~]# systemctl restart keepalived
[root@lb01 ~]# tail -f /var/log/keepalived.log
Apr :: node2 Keepalived_vrrp[]: Sending gratuitous ARP on ens33 for 172.25.254.254
Apr :: node2 Keepalived_vrrp[]: Sending gratuitous ARP on ens33 for 172.25.254.254
Apr :: node2 Keepalived_vrrp[]: Sending gratuitous ARP on ens33 for 172.25.254.254
Apr :: node2 Keepalived_vrrp[]: VRRP_Instance(VI_1) Received advert with lower priority , ours , forcing new election
Apr :: node2 Keepalived_vrrp[]: Sending gratuitous ARP on ens33 for 172.25.254.254
Apr :: node2 Keepalived_vrrp[]: VRRP_Instance(VI_1) Sending/queueing gratuitous ARPs on ens33 for 172.25.254.254
4.4 keepalived多实例
[root@lb01 ~]# vim /etc/keepalived/keepalived.conf
! Configuration File for keepalived
global_defs {
notification_email {
@qq.com
}
notification_email_from Alexandre.Cassen@firewall.loc
smtp_server 192.168.200.1
smtp_connect_timeout
router_id LVS_01
vrrp_skip_check_adv_addr
# vrrp_strict
vrrp_garp_interval
vrrp_gna_interval
}
vrrp_instance VI_1 {
state MASTER
interface ens33
virtual_router_id
priority
advert_int
authentication {
auth_type PASS
auth_pass
}
virtual_ipaddress {
172.25.254.254/
}
}
vrrp_instance VI_2 {
state BACKUP
interface ens33
virtual_router_id
priority
advert_int
authentication {
auth_type PASS
auth_pass
}
virtual_ipaddress {
172.25.254.253/
}
}
[root@lb02 ~]# vim /etc/keepalived/keepalived.conf
! Configuration File for keepalived
global_defs {
notification_email {
@qq.com
}
notification_email_from Alexandre.Cassen@firewall.loc
smtp_server 192.168.200.1
smtp_connect_timeout
router_id LVS_02
vrrp_skip_check_adv_addr
# vrrp_strict
vrrp_garp_interval
vrrp_gna_interval
}
vrrp_instance VI_1 {
state BACKUP
interface ens33
virtual_router_id
priority
advert_int
authentication {
auth_type PASS
auth_pass
}
virtual_ipaddress {
172.25.254.254/
}
}
vrrp_instance VI_2 {
state MASTER
interface ens33
virtual_router_id
priority
advert_int
authentication {
auth_type PASS
auth_pass
}
virtual_ipaddress {
172.25.254.253/
}
}
检测
[root@lb01 ~]# systemctl restart keepalived
[root@lb02 ~]# systemctl restart keepalived
[root@lb01 ~]# ip addr
inet 172.25.254.131/ brd 172.25.254.255 scope global dynamic ens33
valid_lft 499sec preferred_lft 499sec
inet 172.25.254.254/ scope global secondary ens33
valid_lft forever preferred_lft forever
[root@lb02 ~]# ip addr
inet 172.25.254.133/ brd 172.25.254.255 scope global dynamic ens33
valid_lft 422sec preferred_lft 422sec
inet 172.25.254.253/ scope global secondary ens33
valid_lft forever preferred_lft forever
[root@lb02 ~]# systemctl stop keepalived
[root@lb02 ~]# ip addr|grep 172.25.
inet 172.25.254.133/ brd 172.25.254.255 scope global dynamic ens33
[root@lb01 ~]# ip addr |grep 172.25.
inet 172.25.254.131/ brd 172.25.254.255 scope global dynamic ens33
inet 172.25.254.254/ scope global secondary ens33
inet 172.25.254.253/ scope global secondary ens33
[root@lb02 ~]# systemctl start keepalived
[root@lb02 ~]# ip addr|grep 172.25.
inet 172.25.254.133/ brd 172.25.254.255 scope global dynamic ens33
inet 172.25.254.253/ scope global secondary ens33
[root@lb01 ~]# ip addr |grep 172.25.
inet 172.25.254.131/ brd 172.25.254.255 scope global dynamic ens33
inet 172.25.254.254/ scope global secondary ens33
参考:老男孩教育视频公开课https://www.bilibili.com/video/av25869969/?p=25
nginx和keeplive实现负载均衡高可用的更多相关文章
- linux系统下对网站实施负载均衡+高可用集群需要考虑的几点
随着linux系统的成熟和广泛普及,linux运维技术越来越受到企业的关注和追捧.在一些中小企业,尤其是牵涉到电子商务和电子广告类的网站,通常会要求作负载均衡和高可用的Linux集群方案. 那么如何实 ...
- Linux下"负载均衡+高可用"集群的考虑点 以及 高可用方案说明(Keepalive/Heartbeat)
当下Linux运维技术越来越受到企业的关注和追捧, 在某些企业, 尤其是牵涉到电子商务和电子广告类的网站,通常会要求作负载均衡和高可用的Linux集群方案.那么如何实施Llinux集群架构,才能既有效 ...
- Nginx+Keepalived负载均衡高可用
Nginx+Keepalived负载均衡高可用方案: Nginx 使用平台:unix.linux.windows. 功能: A.www web服务 http 80 b.负载均衡(方向代理proxy) ...
- JAVAEE——宜立方商城03:Nginx负载均衡高可用、Keepalived+Nginx实现主备
1 nginx负载均衡高可用 1.1 什么是负载均衡高可用 nginx作为负载均衡器,所有请求都到了nginx,可见nginx处于非常重点的位置,如果nginx服务器宕机后端web服务将无法提供服务, ...
- Nginx负载均衡高可用
1. Nginx负载均衡高可用 首先介绍一下Keepalived,它是一个高性能的服务器高可用或热备解决方案,Keepalived主要来防止服务器单点故障的发生问题,可以通过其与Nginx的配合实 ...
- Keepalived+Nginx实现负载均衡高可用
一.负载均衡高可用 Nginx作为负载均衡器,所有请求都到了Nginx,可见Nginx处于非常重点的位置,如果Nginx服务器宕机后端web服务将无法提供服务,影响严重. 为了避免负载均衡服务器的宕机 ...
- Nginx+keepalived实现负载均衡高可用配置
1. 什么是负载均衡高可用 nginx作为负载均衡器,所有请求都到了nginx,可见nginx处于非常重点的位置,如果nginx服务器宕机后端web服务将无法提供服务,影响严重. 为了屏蔽负载均衡服务 ...
- Nginx负载均衡高可用---架构
1. Nginx负载均衡高可用 首先介绍一下Keepalived,它是一个高性能的服务器高可用或热备解决方案,Keepalived主要来防止服务器单点故障的发生问题,可以通过其与Nginx的配合实现w ...
- nginx负载均衡高可用部署和代理配置
nginx负载均衡高可用配置 服务器A:172.16.100.2 服务器B:172.16.100.3 首先先在两台服务器上分别安装好nginx和keepalived后,再进行下面的操作 配置keepa ...
随机推荐
- 可变形参 Day07
package com.sxt.kebianxingcan; /* * 可变形参 * 声明:数据类型...标识符 * 作用:将实参作为数组处理 * 规则:一个方法只能有一个可变形参并且作为最后一个形参 ...
- Python从文件中读取内容,包含中文和英文
读取文件内容使要和保存文件时的格式一致 以UTF-8格式保存文件,如: 读取: 在.py起始行写入:#-*- coding:utf-8 -*- filename = raw_input(u" ...
- idea使用积累
1.初试化配置参照http://m.blog.csdn.net/robertohuang/article/details/75042116,很详细. 2.idea中忽略.idea,.iml这两个文件 ...
- Transformer的PyTorch实现
Google 2017年的论文 Attention is all you need 阐释了什么叫做大道至简!该论文提出了Transformer模型,完全基于Attention mechanism,抛弃 ...
- Python的unittest拓展和HTMLReport SKIP报表扩展
C:\Python27\Lib中修改unittest内容 unittest 在init中添加Myskip代码: __all__ = ['TestResult', 'TestCase', 'TestSu ...
- 2018年NOIP普及组复赛题解
题目涉及算法: 标题统计:字符串入门题: 龙虎斗:数学题: 摆渡车:动态规划: 对称二叉树:搜索. 标题统计 题目链接:https://www.luogu.org/problem/P5015 这道题目 ...
- PHP 试题(1)
1.__FILE__表示什么意思?(5分)文件的完整路径和文件名.如果用在包含文件中,则返回包含文件名.自 PHP 4.0.2 起,__FILE__ 总是包含一个绝对路径,而在此之前的版本有时会包含一 ...
- Project Euler Problem 7-10001st prime
素数线性筛 MAXN = 110100 prime = [0 for i in range(210000)] for i in range(2,MAXN): if prime[i] == 0: pri ...
- GPU版TensorFlow怎么指定让CPU运行
由于某些原因GPU版的TensorFlow运行起来会出现一些问题,比如内存溢出等情况.此时我们可以用CPU和系统内存来运行我们的程序. 代码如下: import osos.environ[" ...
- spring boot与activiti集成实战 转
为什么80%的码农都做不了架构师?>>> 这是原作者的博客地址 http://wiselyman.iteye.com/blog/2285223 代码格式混乱,我修正了一下.项目源码在 ...
