hdu3360National Treasures (最大匹配,拆点法)
National Treasures
Time Limit: 2000/1000 MS (Java/Others) Memory Limit: 32768/32768 K (Java/Others)
Total Submission(s): 1038 Accepted Submission(s): 364
additional guards to stay in the great hall and keep an eye on the ancient artifacts. The museum would like to hire the minimum number of additional guards so that the great hall is secured.
The great hall is represented as a two dimensional grid of R × C cells. Some cells are already occupied with the museum’s guards. All remaining cells are occupied by artifacts of different types (statues, sculptures, . . . etc.) which can be replaced by new
hired guards. For each artifact, few other cells in the hall are identified as critical points of the artifact depending on the artifact value, type of vault it is kept inside, and few other factors. In other words, if this artifact is going to stay in the
hall then all of its critical points must have guards standing on them. A guard standing in a critical position of multiple artifacts can keep an eye on them all. A guard, however,
can not stand in a cell which contains an artifact (instead, you may remove the artifact to allow the guard to stay there). Also you can not remove an artifact and leave the space free (you can only replace an artifact with a new hired guard).
Surveying all the artifacts in the great hall you figured out that the critical points of any artifact (marked by a
 ) are always a subset of the 12 neighboring cells as shown in the grid below.
) are always a subset of the 12 neighboring cells as shown in the grid below.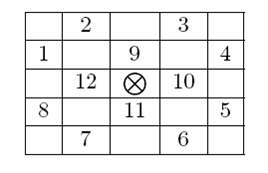
Accordingly, the type of an artifact can be specified as a non-negative integer where the i-th bit is 1 only if critical point number i from the picture above is a critical point of that artifact. For example an artifact of type 595 (in binary 1001010011) can
be pictured as shown in the figure below. Note that bits are numbered from right to left (the right-most bit is bit number 1.) If a critical point of an artifact lies outside the hall grid then it is considered secure.
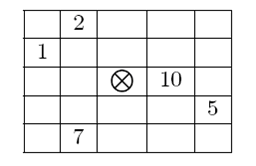
You are given the layout of the great hall and are asked to find the minimum number of additional guards to hire such that all remaining artifacts are secured.
The first line specifies two integers (1<= R,C <= 50) which are the dimensions of the museum hall. The next R lines contain C integers separated by one or more spaces. The j-th integer of the i-th row is -1 if cell (i, j) already contains one of the museum’s
guards, otherwise it contains an integer (0 <= T <= 212) representing the type of the artifact in that cell.
The last line of the input file has two zeros.
k. G
Where k is the test case number (starting at one,) and G is the minimum number of additional guards to hire such that all remaining artifacts are secured.
1 3
512 -1 2048
2 3
512 2560 2048
512 2560 2048
0 0
1. 0
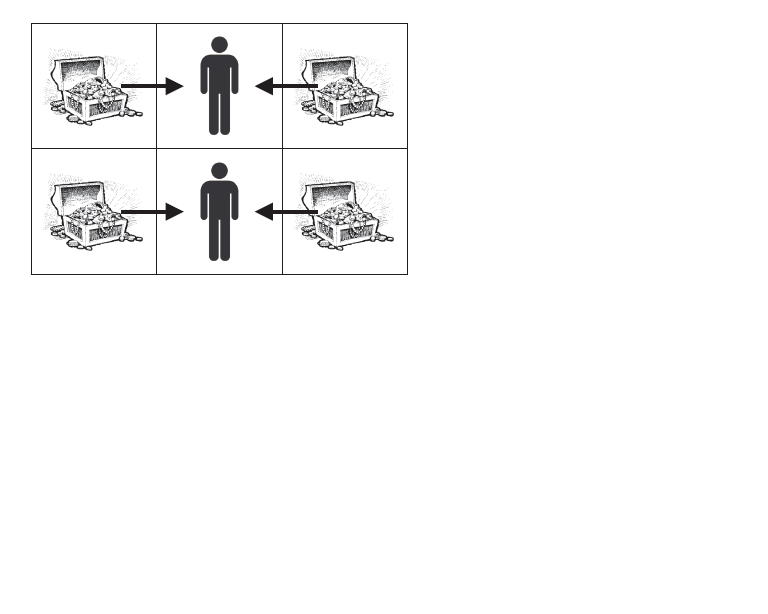
2. 2HintThe picture below shows the solution of the second test case where the two artifacts in the middle are replaced by guards.
#include<stdio.h>
#include<vector>
#include<iostream>
using namespace std;
int match[2505],vist[2505];
vector<int>map[2505];
int find(int i)
{
for(int j=0;j<map[i].size();j++)
if(!vist[map[i][j]])
{
vist[map[i][j]]=1;
if(match[map[i][j]]==-1||find(match[map[i][j]]))
{
match[map[i][j]]=i; return 1;
}
}
return 0;
}
int main()
{
int dir[12][2]={-1,-2,-2,-1,-2,1,-1,2,1,2,2,1,2,-1,1,-2,-1,0,0,1,1,0,0,-1};
int n,m,mp[55][55],b_w[55][55],bn,wn,k=0;
while(scanf("%d%d",&n,&m)>0&&n+m!=0)
{
for(int i=0;i<n*m;i++)
{
map[i].clear(),match[i]=-1;
} for(int i=0;i<n;i++)
for(int j=0;j<m;j++)
scanf("%d",&mp[i][j]);
for(int i=0;i<n;i++)
for(int j=0;j<m;j++)
if(mp[i][j]!=-1)
{
int ti,tj;
for(int e=0;e<12;e++)
if(mp[i][j]&(1<<e))
{
ti=i+dir[e][0]; tj=j+dir[e][1];
if(ti>=0&&ti<n&&tj>=0&&tj<m&&mp[ti][tj]!=-1)
{
map[ti*m+tj].push_back(i*m+j);
map[i*m+j].push_back(ti*m+tj);
}
}
}
int ans=0;
for(int i=0;i<n*m;i++)
{
for(int j=0;j<n*m;j++)
vist[j]=0;
ans+=find(i);
}
printf("%d. %d\n",++k,ans/2);
}
}
hdu3360National Treasures (最大匹配,拆点法)的更多相关文章
- UVA 1658 海军上将(拆点法+最小费用限制流)
海军上将 紫书P375 这题我觉得有2个难点: 一是拆点,要有足够的想法才能把这题用网络流建模,并且知道如何拆点. 二是最小费用限制流,最小费用最大流我们都会,但如果限制流必须为一个值呢?比如这题限制 ...
- UVa 1658 (拆点法 最小费用流) Admiral
题意: 给出一个有向带权图,求从起点到终点的两条不相交路径使得权值和最小. 分析: 第一次听到“拆点法”这个名词. 把除起点和终点以外的点拆成两个点i和i',然后在这两点之间连一条容量为1,费用为0的 ...
- poj3422 拆点法x->x'建立两条边+最小费用最大流
/** 题目:poj3422 拆点法+最小费用最大流 链接:http://poj.org/problem?id=3422 题意:给定n*n的矩阵,含有元素值,初始sum=0.每次从最左上角开始出发,每 ...
- Acme Corporation UVA - 11613 拆点法+最大费用最大流(费用取相反数)+费用有正负
/** 题目:Acme Corporation UVA - 11613 拆点法+最大费用最大流(费用取相反数)+费用有正负 链接:https://vjudge.net/problem/UVA-1161 ...
- Risk UVA - 12264 拆点法+最大流+二分 最少流量的节点流量尽量多。
/** 题目:Risk UVA - 12264 链接:https://vjudge.net/problem/UVA-12264 题意:给n个点的无权无向图(n<=100),每个点有一个非负数ai ...
- UVA1349 Optimal Bus Route Design 拆点法+最小费用最佳匹配
/** 题目:UVA1349 Optimal Bus Route Design 链接:https://vjudge.net/problem/UVA-1349 题意:lrj入门经典P375 给n个点(n ...
- UVA1658 Admiral 拆点法解决结点容量(路径不能有公共点,容量为1的时候) 最小费用最大流
/** 题目:UVA1658 Admiral 链接:https://vjudge.net/problem/UVA-1658 题意:lrj入门经典P375 求从s到t的两条不相交(除了s和t外,没有公共 ...
- 紫书 习题 11-4 UVa 1660 (网络流拆点法)
这道题改了两天-- 因为这道题和节点有关, 所以就用拆点法解决节点的容量问题. 节点拆成两个点, 连一条弧容量为1, 表示只能经过一次. 然后图中的弧容量无限. 然后求最小割, 即最大流, 即为答案. ...
- UVa1658 Admiral(拆点法+最小费用流)
题目链接:http://acm.hust.edu.cn/vjudge/problem/viewProblem.action?id=51253 [思路] 固定流量的最小费用流. 拆点,将u拆分成u1和u ...
随机推荐
- android sdk 镜象网站
因为一些原因.Google相关非常多服务都无法訪问,所以在非常多时候我们SDK也无法升级,当然通过技术手段肯定能够解决,可是比較麻烦,并且下载速度也不怎么样. 这里笔者介绍一个国内的Android镜像 ...
- Linux系统捕获数据包流程
Linux系统捕获数据包流程 为了提高数据包的捕获效率,瓶颈问题是一个需要非常关注的焦点.减少在捕获数据包过程中的瓶颈,就能够提高数据包捕获的整体性能.下面本文将以Linux操作系统为平台,分析捕获数 ...
- Pairs Forming LCM
题目: B - Pairs Forming LCM Time Limit:2000MS Memory Limit:32768KB Description Find the result of ...
- JavaScript--数据结构之栈
4.1栈是一种高效的数据结构,是一种特殊的列表.栈内元素只能通过列表的一端访问,也就称为栈顶.后入的先出的操作.Last in First out.所以他的访问每次是访问到栈顶的元素,要想访问其余的元 ...
- jmeter实现分布式压测步骤
环境说明:安装与控制机相同版本的jdk与jmeter 1.修改控制机中的jmeter.properties文件 将<remote_hosts=127.0.0.1>改为<remote_ ...
- vim学习2
进入插入模式: 在插入模式下删除: 寄存器
- 如何优雅的写UI——(1)MFC六大核心机制-程序初始化
很多做软件开发的人都有一种对事情刨根问底的精神,例如我们一直在用的MFC,很方便,不用学太多原理性的知识就可以做出各种窗口程序,但喜欢钻研的朋友肯定想知道,到底微软帮我们做了些什么,让我们在它的框架下 ...
- 如何从mysql数据库中取到随机的记录
如何从mysql数据库中取到随机的记录 一.总结 一句话总结:用随机函数newID(),select top N * from table_name order by newid() ----N是一个 ...
- 98.TCP通信传输文件
客户端 #define _CRT_SECURE_NO_WARNINGS #include<stdio.h> #include <stdlib.h> #include <s ...
- 1.1 Introduction中 Topics and Logs官网剖析(博主推荐)
不多说,直接上干货! 一切来源于官网 http://kafka.apache.org/documentation/ Topics and Logs 话题和日志 (Topic和Log) Let's fi ...
