ingress controller 和ingress使用实例
ingress controller安装
k8s集群版本:1.15+
官方文档:
https://kubernetes.github.io/ingress-nginx/
创建基础配置
kubectl apply -f https://raw.githubusercontent.com/kubernetes/ingress-nginx/master/deploy/static/mandatory.yaml
Using NodePort:
kubectl apply -f https://raw.githubusercontent.com/kubernetes/ingress-nginx/master/deploy/static/provider/baremetal/service-nodeport.yaml
以上执行完成后,查看ingress-controller已经运行起来了
[root@k8s-master ~]# kubectl get pods -n ingress-nginx
NAME READY STATUS RESTARTS AGE
nginx-ingress-controller-689498bc7c-tvhv5 1/1 Running 3 16d
[root@k8s-master ~]#
查看service信息,nodeport端口31380,31390
[root@k8s-master ~]# kubectl get svc -n ingress-nginx
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
ingress-nginx NodePort 10.108.101.78 <none> 80:31380/TCP,443:31390/TCP 14d
[root@k8s-master ~]#
至此ingress-controller安装完成
What is Ingress?
internet
|
[ Ingress ]
--|-----|--
[ Services ]
ingress使用
本次通过安装kubernetes的dashboard来演示ingress的使用
dashboard的安装
kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/v1.10.1/src/deploy/recommended/kubernetes-dashboard.yaml
[root@k8s-master jtdeploy]# cat kubernetes-dashboard.yaml
# Copyright 2017 The Kubernetes Authors.
#
# Licensed under the Apache License, Version 2.0 (the "License");
# you may not use this file except in compliance with the License.
# You may obtain a copy of the License at
#
# http://www.apache.org/licenses/LICENSE-2.0
#
# Unless required by applicable law or agreed to in writing, software
# distributed under the License is distributed on an "AS IS" BASIS,
# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
# See the License for the specific language governing permissions and
# limitations under the License. # ------------------- Dashboard Secret ------------------- # apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-certs
namespace: kube-system
type: Opaque ---
# ------------------- Dashboard Service Account ------------------- # apiVersion: v1
kind: ServiceAccount
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kube-system ---
# ------------------- Dashboard Role & Role Binding ------------------- # kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: kubernetes-dashboard-minimal
namespace: kube-system
rules:
# Allow Dashboard to create 'kubernetes-dashboard-key-holder' secret.
- apiGroups: [""]
resources: ["secrets"]
verbs: ["create"]
# Allow Dashboard to create 'kubernetes-dashboard-settings' config map.
- apiGroups: [""]
resources: ["configmaps"]
verbs: ["create"]
# Allow Dashboard to get, update and delete Dashboard exclusive secrets.
- apiGroups: [""]
resources: ["secrets"]
resourceNames: ["kubernetes-dashboard-key-holder", "kubernetes-dashboard-certs"]
verbs: ["get", "update", "delete"]
# Allow Dashboard to get and update 'kubernetes-dashboard-settings' config map.
- apiGroups: [""]
resources: ["configmaps"]
resourceNames: ["kubernetes-dashboard-settings"]
verbs: ["get", "update"]
# Allow Dashboard to get metrics from heapster.
- apiGroups: [""]
resources: ["services"]
resourceNames: ["heapster"]
verbs: ["proxy"]
- apiGroups: [""]
resources: ["services/proxy"]
resourceNames: ["heapster", "http:heapster:", "https:heapster:"]
verbs: ["get"] ---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: kubernetes-dashboard-minimal
namespace: kube-system
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: kubernetes-dashboard-minimal
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard
namespace: kube-system ---
# ------------------- Dashboard Deployment ------------------- # kind: Deployment
apiVersion: apps/v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kube-system
spec:
replicas: 1
revisionHistoryLimit: 10
selector:
matchLabels:
k8s-app: kubernetes-dashboard
template:
metadata:
labels:
k8s-app: kubernetes-dashboard
spec:
containers:
- name: kubernetes-dashboard
image: k8s.gcr.io/kubernetes-dashboard-amd64:v1.10.1
ports:
- containerPort: 9090
protocol: TCP
args:
- --enable-skip-login
# Uncomment the following line to manually specify Kubernetes API server Host
# If not specified, Dashboard will attempt to auto discover the API server and connect
# to it. Uncomment only if the default does not work.
# - --apiserver-host=http://my-address:port
volumeMounts:
- name: kubernetes-dashboard-certs
mountPath: /certs
# Create on-disk volume to store exec logs
- mountPath: /tmp
name: tmp-volume
livenessProbe:
httpGet:
scheme: HTTP
path: /
port: 9090
initialDelaySeconds: 30
timeoutSeconds: 30
volumes:
- name: kubernetes-dashboard-certs
secret:
secretName: kubernetes-dashboard-certs
- name: tmp-volume
emptyDir: {}
serviceAccountName: kubernetes-dashboard
# Comment the following tolerations if Dashboard must not be deployed on master
tolerations:
- key: node-role.kubernetes.io/master
effect: NoSchedule
---
apiVersion: rbac.authorization.k8s.io/v1beta1
kind: ClusterRoleBinding
metadata:
name: kubernetes-dashboard
labels:
k8s-app: kubernetes-dashboard
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard
namespace: kube-system ---
# ------------------- Dashboard Service ------------------- # kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kube-system
spec:
type: NodePort
ports:
- port: 9090
targetPort: 9090
selector:
k8s-app: kubernetes-dashboard
[root@k8s-master jtdeploy]#
配置文件修改原模板containerPort 端口
args:
- --enable-skip-login 表示不认证
使用以上配置文件即可创建
查看pods
[root@k8s-master jtdeploy]# kubectl get pods -n kube-system
NAME READY STATUS RESTARTS AGE
calico-node-2srnw 2/2 Running 8 20d
calico-node-ppnjh 2/2 Running 8 20d
coredns-86c58d9df4-ptth2 1/1 Running 4 20d
coredns-86c58d9df4-wxldx 1/1 Running 4 20d
etcd-k8s-master 1/1 Running 4 20d
kube-apiserver-k8s-master 1/1 Running 4 20d
kube-controller-manager-k8s-master 1/1 Running 4 20d
kube-proxy-4kwj6 1/1 Running 4 20d
kube-proxy-hfmqn 1/1 Running 4 20d
kube-scheduler-k8s-master 1/1 Running 4 20d
kubernetes-dashboard-784b868d9d-hc77v 1/1 Running 3 16d
tiller-deploy-dbb85cb99-srbch 1/1 Running 4 20d
[root@k8s-master jtdeploy]#
查看svc
[root@k8s-master jtdeploy]# kubectl get svc -n kube-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
calico-typha ClusterIP 10.105.54.12 <none> 5473/TCP 20d
kube-dns ClusterIP 10.96.0.10 <none> 53/UDP,53/TCP 20d
kubernetes-dashboard ClusterIP 10.106.65.78 <none> 9090/TCP 16d
tiller-deploy ClusterIP 10.97.33.192 <none> 44134/TCP 20d
[root@k8s-master jtdeploy]#
这里没有使用nodeport ,所有使用ingress来配置外网访问.
haproxy安装
root@xuliang-PC:~/haproxy# cat docker-compose.yml
version: "2"
services:
haproxy:
image: haproxy:1.8
ports:
- 80:31380
- 443:31390
- 8181:8181
restart: always
volumes:
- /root/haproxy/haproxy.cfg:/usr/local/etc/haproxy/haproxy.cfg
network_mode: host
# networks:
# # - haproxy_lb
#
# #networks:
# # haproxy_lb:
# # driver: bridge root@xuliang-PC:~/haproxy#
haproxy配置文件
root@xuliang-PC:~/haproxy# cat haproxy.cfg
global
stats timeout 30s
maxconn 1000 defaults
mode tcp
option dontlognull
retries 3 timeout http-request 30s
timeout queue 1m
timeout connect 30s
timeout client 1m
timeout server 1m
timeout http-keep-alive 30s
timeout check 30s option redispatch
option srvtcpka
option clitcpka ## HTTP
frontend http_front
bind *:80
default_backend http_backend backend http_backend
server k8s-master 192.168.100.101:31380 check
server k8s-node1 192.168.1.102:31380 check
#server k8s-node3 192.168.1.103:31380 check ## HTTPS
frontend https_front
bind *:443
default_backend https_backend backend https_backend
server k8s-master 192.168.100.101:31390 check
server k8s-node1 192.168.100.102:31390 check
#server k8s-node4 192.168.1.103:31390 check # HAProxy stats
listen stats
bind *:8181
mode http
stats enable
stats uri /
stats realm Haproxy\ Statistics
stats auth haproxy:haproxy
root@xuliang-PC:~/haproxy#
在本机添加hosts,有域名的可以配置域名解析
root@xuliang-PC:~/haproxy# cat /etc/hosts
192.168.100.29 myapp.test.com
root@xuliang-PC:~/haproxy#
测试解析
root@xuliang-PC:~/haproxy# ping myapp.test.com
PING myapp.test.com (192.168.100.29) 56(84) bytes of data.
64 bytes from myapp.test.com (192.168.100.29): icmp_seq=1 ttl=64 time=0.024 ms
64 bytes from myapp.test.com (192.168.100.29): icmp_seq=2 ttl=64 time=0.024 ms
64 bytes from myapp.test.com (192.168.100.29): icmp_seq=3 ttl=64 time=0.028 ms
^C
--- myapp.test.com ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2032ms
rtt min/avg/max/mdev = 0.024/0.025/0.028/0.004 ms
root@xuliang-PC:~/haproxy#
配置ingress
[root@k8s-master ~]# cat ingress-dashboard.yaml
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: ingress-dashboard
namespace: kube-system
annotations:
kubernetes.io/ingress.class: "nginx"
spec:
rules:
- host: myapp.test.com
http:
paths:
- path: /
backend:
serviceName: kubernetes-dashboard
servicePort: 9090 ---
apiVersion: v1
kind: Service
metadata:
name: ingress-nginx
namespace: ingress-nginx
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
spec:
type: NodePort
ports:
- name: http
port: 80
targetPort: 80
protocol: TCP
nodePort: 31380
- name: https
port: 443
targetPort: 443
protocol: TCP
nodePort: 31390
selector:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx --- [root@k8s-master ~]#
此处注意一定要配置:
annotations:
kubernetes.io/ingress.class: "nginx"
查看ingress
[root@k8s-master dashboard]# kubectl get ingress -n kube-system
NAME HOSTS ADDRESS PORTS AGE
ingress-dashboard myapp.test.com 10.108.73.126 80 147m
[root@k8s-master dashboard]#
至此可以通过域名访问
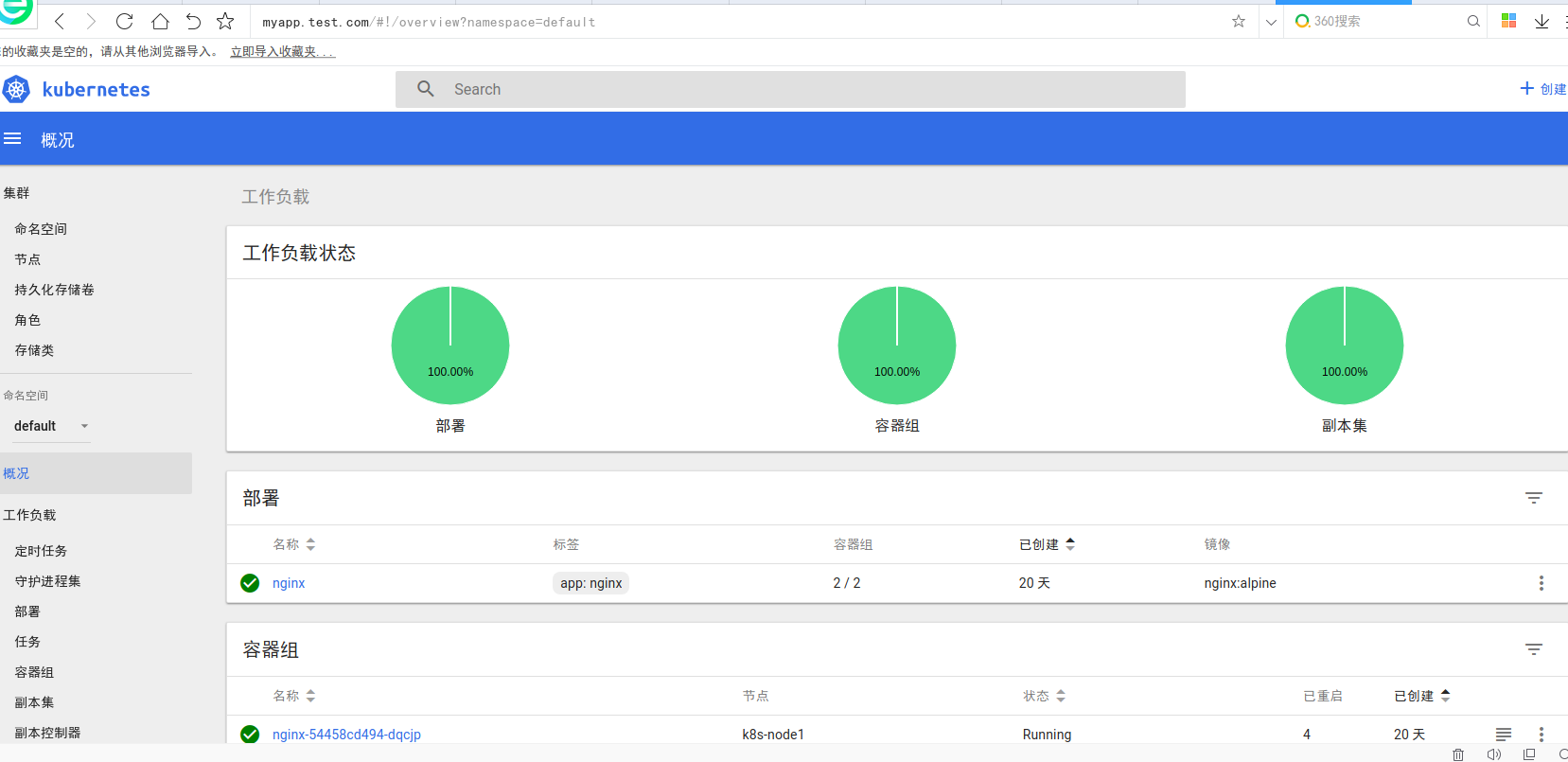
ingress controller 和ingress使用实例的更多相关文章
- Kubernetes 学习11 kubernetes ingress及ingress controller
一.上集回顾 1.Service 3种模型:userspace,iptables,ipvs 2.Service类型 ClusterIP,NodePort NodePort:client -> N ...
- 实操教程丨如何在K8S集群中部署Traefik Ingress Controller
注:本文使用的Traefik为1.x的版本 在生产环境中,我们常常需要控制来自互联网的外部进入集群中,而这恰巧是Ingress的职责. Ingress的主要目的是将HTTP和HTTPS从集群外部暴露给 ...
- Kubernetes Ingress Controller的使用及高可用落地
Kubernetes Ingress Controller的使用及高可用落地 看懂本文要具备一下知识点: Service实现原理和会应用 知道反向代理原理,了解nginx和apache的vhost概念 ...
- Kubernetes 服务入口管理与 Nginx Ingress Controller
Kubernetes 具有强大的副本,动态扩容等特性,每一次 Pod 的变化 IP 地址都会发生变化,所以 Kubernetes 引进了 Service 的概念.Kubernetes 中使用 Serv ...
- Kubernetes学习之路(十五)之Ingress和Ingress Controller
目录 一.什么是Ingress? 1.Pod 漂移问题 2.端口管理问题 3.域名分配及动态更新问题 二.如何创建Ingress资源 三.Ingress资源类型 1.单Service资源型Ingres ...
- 11. Ingress及Ingress Controller(主nginx ingress controller)
11. Ingress,Ingress Controller拥有七层代理调度能力 什么是Ingress: Ingress是授权入站连接到达集群服务的规则集合 Ingress是一个Kubernetes资 ...
- traefik ingress Controller使用
Kubernetes Ingress Kubernetes Ingress是路由规则的集合,这些规则控制外部用户如何访问Kubernetes集群中运行的服务. 在Kubernetes中,有三种方式可以 ...
- 浅谈 k8s ingress controller 选型
大家好,先简单自我介绍下,我叫厉辉,来自腾讯云.业余时间比较喜欢开源,现在是Apache APISIX PPMC.今天我来简单给大家介绍下 K8S Ingress 控制器的选型经验,今天我讲的这些内容 ...
- 为 Rainbond Ingress Controller 设置负载均衡
Rainbond 作为一款云原生应用管理平台,天生带有引导南北向网络流量的分布式网关 rbd-gateway.rbd-gateway 组件,实际上是好雨科技团队开发的一种 Ingress Contro ...
随机推荐
- SpringBoot(七):SpringBoot中如何使用过滤器(Filter)?
方式一: 通过注解方式实现: 1.编写一个Servlet3的注解过滤器(和上一章Servlet相似) 贴代码: package com.example.springbootweb.filter; im ...
- 后端程序员之路 55、go redis
redigo有点像hiredis,只提供了最基本的连接和执行命令接口. 找到个不错的redis库: https://github.com/go-redis/redis func ExampleNewC ...
- nc替代ping
linux nc介绍: 语 法:nc [-hlnruz][-g<网关...>][-G<指向器数目>][-i<延迟秒数>][-o<输出文件>][-p< ...
- XXL-JOB v2.3.0 发布 | 易用性增强
转: XXL-JOB v2.3.0 发布 | 易用性增强 v2.3.0 Release Notes 1.[新增]调度过期策略:调度中心错过调度时间的补偿处理策略,包括:忽略.立即补偿触发一次等: 2. ...
- Linux ctrl+z挂起的进程恢复与杀死
Linux系统下,不小心按了ctrl+z命令后,退出了当前进程的执行界面,程序没有结束,只是被挂起了.通过ps命令可以查看进程信息,这里不做详细介绍,可通过jobs命令查看被挂起的进程号 #jobs ...
- 番外----python入门----pip相关
pip 是 Python 包管理工具,该工具提供了对Python 包的查找.下载.安装.卸载的功能. 但是,由于pip使用的pip仓库默认为:http://pypi.python.org/ 是国外的 ...
- 漏洞复现-CVE-2018-8715-Appweb
0x00 实验环境 攻击机:Win 10 0x01 影响版本 嵌入式HTTP Web服务器,<7.0.3版本 0x02 漏洞复现 (1)实验环境: 打开后出现此弹框登录界面: (2) ...
- Navicat 121版本激活工具
以下是工具的链接: https://github.com/DoubleLabyrinth/navicat-keygen/blob/windows/README_FOR_WINDOWS.zh-CN.md ...
- Jmeter +Jenkins +Ant 集成发送邮件报告
[TOC] 一.什么是接口测试? 接口测试是测试系统组件间接口的一种测试.接口测试主要用于检测外部系统与系统之间以及内部各个子系统之间的交互点.测试的重点是要检查数据的交换,传递和控制管理过程,以及系 ...
- 题解 CF746D 【Green and Black Tea】
# 题目分析这道题表面上看上去挺简单,其实仔细研究一下还是值得钻研的.我本人做这道题使用的任然是$ DFS01 $背包.不过呢,与往常背包不同的是,这次递归中需要加许多参数.就数据强度来看,栈问题不大 ...
