Implementing Azure AD Single Sign-Out in ASP.NET Core(转载)
Let's start with a scenario. Bob the user has logged in to your ASP.NET Core application through Azure AD authentication. Bob then also opens their email through Office 365 in the same browser window. They decide to leave work for today, and sign out from Office 365.
Without single sign-out, Bob has to also sign out from your Core application for them to be fully signed out.
With single sign-out, Bob doesn't have to separately sign out from your application. It's already been done for them.
Defining the remote sign-out path
First you will need to define the RemoteSignoutPath in the OpenIdConnectOptions. Here is the full configuration for OpenId Connect authentication that we will use:
.AddOpenIdConnect(o =>
{
o.ClientId = Configuration["Authentication:ClientId"];
o.Authority = Configuration["Authentication:Authority"];
o.CallbackPath = "/aad-callback"; o.RemoteSignOutPath = "/aad-signout";
});
Since the URL was defined as /aad-signout and the app runs at https://mycoolapp.com, we will define the sign-out URL to Azure AD as https://mycoolapp.com/aad-signout. Here is how that looks:
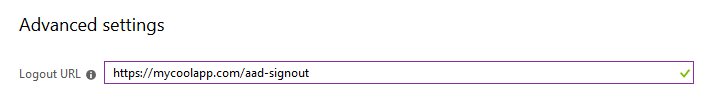
Now one final thing is that due to how single sign-out works, we must remove the SameSite attribute from the authentication cookie:
.AddCookie(o =>
{
o.Cookie.SameSite = Microsoft.AspNetCore.Http.SameSiteMode.None;
})
This security feature must currently be removed to use single sign-out. I will explain why in a bit.
And we are done. If you try a scenario like in the start, you'll notice your authentication cookie will vanish.
The complete authentication configuration just for reference:
services
.AddAuthentication(o =>
{
o.DefaultScheme = CookieAuthenticationDefaults.AuthenticationScheme;
o.DefaultForbidScheme = CookieAuthenticationDefaults.AuthenticationScheme;
o.DefaultChallengeScheme = OpenIdConnectDefaults.AuthenticationScheme;
})
.AddCookie(o =>
{
o.Cookie.SameSite = Microsoft.AspNetCore.Http.SameSiteMode.None;
})
.AddOpenIdConnect(o =>
{
o.ClientId = Configuration["Authentication:ClientId"];
o.Authority = Configuration["Authentication:Authority"];
o.CallbackPath = "/aad-callback"; o.RemoteSignOutPath = "/aad-signout";
});
How it works
So, that was quite easy. The way it works is actually quite simple. Azure AD knows the user is logged in to your app, and it has a sign-out URL defined. AAD opens a hidden iframe and sets its URL to your sign-out URL.
Now this did not work for me at first due to the SameSite property that is set by default now in ASP.NET Core. The authentication cookie gets SameSite=lax by default, which means that it is passed only in GET requests that are top-level, when coming from another origin. So it will not be attached to requests from iframes or AJAX that are initiated by other sites.
Thus it must be disabled for this to work, since it works via an iframe that is hosted in another origin.
You can also use your app's normal signout URL in AAD (which you link to from a Sign Out link in your app), however it must then support GET requests. Based on my observations, it made AAD do the sign-out slightly faster as it was able to detect the iframe arriving in AAD's URL. Since the origin is the same, it is allowed access to the iframe URL and it knows the app signout is done. Otherwise it seems to wait some fixed time period.
This is known as front-channel global sign-out. There is also a back-channel global sign-out protocol specification, which AAD does not implement.
If you block framing through use of X-Frame-Options or Content-Security-Policy, it will also prevent this from working. You will have to allow https://login.microsoftonline.com to frame your app.
Front-channel sign-out
This is the method used by Azure AD. Hidden iframe that gets set to your sign-out URL. Sign-out endpoint receives the GET request and handles sign-out as it normally would.
Pros:
- Easy to implement
- Can use existing signout URL with no modifications to app
Cons:
- Sort of a cross-request forgery
- Requires turning off SameSite mode for the auth cookie (if using cookies)
- Must allow AAD to frame your site (add login.microsoftonline.com as allowed frame-ancestor)
I would highly recommend having a CSP that blocks framing from other origins than AAD (plus others that you need to allow).
Back-channel sign-out
This is the other method for single sign-out defined in OpenId Connect specifications. It is not implemented by Azure AD. I have asked the Azure AD team about this and they did say they will look into it :)
This method works by having the identity provider send a request from its back-end to your back-end (i.e. using a back-channel). A signed token similar to an Id token is attached to the request so your back-end can know which user is signing out. It is up to your app to implement session invalidation then.
Pros:
- More secure, can implement strict controls for cookies and framing
- The call is authenticated, not based on a cookie, but a token signed by AAD
Cons:
- Harder to implement
- Even harder to implement correctly in a distributed application
You need to clear session state for the user when you get the request. Or you may need to mark the user's session as expired. And then check if the session is expired on every request.
I can definitely see the motivation for both of these flows. Front-channel is easy to implement, even existing apps can utilize it. Back-channel allows for a more secure approach for those apps willing to pay the cost of implementing it. I do wish AAD would implement the back-channel version too.
Summary
Overall, implementing OpenId Connect single sign-out has been made supremely easy in ASP.NET Core. Well, at least the front-channel version. Since Azure AD only supports front-channel single sign-out, it does require you to reduce some security controls such as removing the SameSite property from the authentication cookie. That protects from Cross-Site Request Forgery attacks, and honestly I'd like to keep that there. But since AAD needs to do an authenticated cross-site request, there is really no choice.
I think whether this feature is valuable enough to reduce the security controls in your app is a decision that the developers/architects will have to make on a case-by-case basis.
Implementing Azure AD Single Sign-Out in ASP.NET Core(转载)的更多相关文章
- 在 Azure WebApps 中运行64位 Asp.net Core 应用
作为微软下一代的开源的跨平台的开发框架, Asp.net core 正在吸引越来越多的开发者基于其构建现代 web 应用. 目前, Azure App Service 也实现了对 asp.net co ...
- Azure AD(二)调用受Microsoft 标识平台保护的 ASP.NET Core Web API 下
一,引言 上一节讲到如何在我们的项目中集成Azure AD 保护我们的API资源,以及在项目中集成Swagger,并且如何把Swagger作为一个客户端进行认证和授权去访问我们的WebApi资源的?本 ...
- [Windows Azure] Adding Sign-On to Your Web Application Using Windows Azure AD
Adding Sign-On to Your Web Application Using Windows Azure AD 14 out of 19 rated this helpful - Rate ...
- Azure 部署 Asp.NET Core Web App
在云计算大行其道的时代,当你在部署一个网站时,第一选择肯定是各式各样的云端服务.那么究竟使用什么样的云端服务才能够以最快捷的方式部署一个 ASP.NET Core 的网站呢?Azure 的 Web A ...
- 在 Azure 上部署 Asp.NET Core Web App
在云计算大行其道的时代,当你要部署一个网站时第一选择肯定是各式各样的云端服务.那么究竟使用什么样的云端服务才能够以最快捷的方式部署一个 ASP.NET Core的网站呢?Azure 的 Web App ...
- 微软Azure配置中心 App Configuration (一):轻松集成到Asp.Net Core
写在前面 在日常开发中,我这边比较熟悉的配置中心有,携程Apollo,阿里Nacos(配置中心,服务治理一体) 之前文章: Asp.Net Core与携程阿波罗(Apollo)的第一次亲密接触 总体来 ...
- asp.net core 系列之Response caching 之 Distributed caching(3)
这篇文章讲解分布式缓存,即 Distributed caching in ASP.NET Core Distributed caching in ASP.NET Core 分布式缓存是可以在多个应用服 ...
- 【译】ASP.NET Core updates in .NET 5 Preview 8
.NET 5 预览版 8 现在已经可以获取了,并且已经准备好接受评估.下面列出了本次发布的新特性: 使用 Microsoft.Identity.Web 进行 Azure Active Director ...
- 003.ASP.NET Core tutorials--【Asp.net core 教程】
ASP.NET Core tutorials Asp.net core 教程 2016-10-14 1 分钟阅读时长 本文内容 1.Building web applications 构建web应用 ...
随机推荐
- OEL7.6源码安装MYSQL5.7
首先官网下载安装包https://dev.mysql.com/downloads/mysql/5.7.html#downloads 然后上传解压至/usr/local目录 [root@localhos ...
- CENTOS安装xwindow
CentOS6安装图形界面 [root@centos6~]# yum -y install xorg* [root@centos6 ~]# yum -y groupinstall "X Wi ...
- Jenkins+GitLab+Ansible-playbook的环境安装(yum)
1.安装GitLab 1.1 配置gitlab的yum源 # 参考:https://packages.gitlab.com/gitlab/gitlab-ce/install#bash-rpm curl ...
- 性能测试基础---jmeter入门
·Jmeter入门 ·Jmeter的简介: ·Jmeter是一款基于纯JAVA语言开发的开源的性能测试工具. ·Jmeter的下载: ·最新版:http://jmeter.apache.org/dow ...
- 洛谷P2463 [SDOI2008]Sandy的卡片(后缀数组SA + 差分 + 二分答案)
题目链接:https://www.luogu.org/problem/P2463 [题意] 求出N个串中都出现的相同子串的最长长度,相同子串的定义如题:所有元素加上一个数变成另一个,则这两个串相同,可 ...
- Spring Boot 注入外部配置到应用内部
Spring Boot允许你外部化你的配置,这样你就可以在不同的环境中使用相同的应用程序代码,你可以使用properties文件.YAML文件.环境变量和命令行参数来外部化配置,属性值可以通过使用@V ...
- Python并发编程之进程通信
''' 进程间的通信 ''' """ multiprocessing模块支持进程间通信的两种主要形式:管道和队列 都是基于消息传递实现的, ""&qu ...
- 关于很狗的军训qwq
我该用哪种方式来证明我存在过 说起这个很狗的军训呀,,, 军训嘛 就不得不先说最基本的,,, 那就是很狗的衣服,,, 一套军装,+一个帽子+一双特别特别特别硌脚的胶鞋!!! 然后... 我胖了..q ...
- vultr的防火墙注意事项
如下图所示,你设置让任意IP的TCP,UDP,GRE,ESP,ICMP都允许访问,并不表示开放了任意协议和端口了. 下图只是表示开放了TCP,UDP,GRE,ESP,ICMP五个协议,比如ROS路由的 ...
- Spring Boot进阶系列三
Thymeleaf是官方推荐的显示引擎,这篇文章主要介绍怎么让spring boot整合Thymeleaf. 它是一个适用于Web和独立环境的现代服务器端Java模板引擎. Thymeleaf的主要 ...
