Flask实战第42天:注册页面对接短信接口及接口加密
我们来看下之前写的 sms_captcha函数
@bp.route('/sms_captcha/')
def sms_captcha():
params = {'code':'abcd'}
result = send_sms('手机号码', json.dumps(params))
if result:
return '发送成功'
else:
return '发送失败'
因此我们的短信接口是http://127.0.0.1:5000/c/sms_captcha,当我完善代码后,手机号码从前端传过来的参数如下:
@bp.route('/sms_captcha/')
def sms_captcha():
telephhone = request.args.get('telephone')
params = {'code':'abcd'}
result = send_sms(telephhone, json.dumps(params))
if result:
return '发送成功'
else:
return '发送失败'
这样,当前端只需要访问这个接口,传递个手机号码过来,就可以发送短信了。当恶意者通过爬虫技术访问这个接口,就可以实现恶意发送短信,对公司造成损失,因此设计这个接口时,我们就对它加密。加密规则如下:
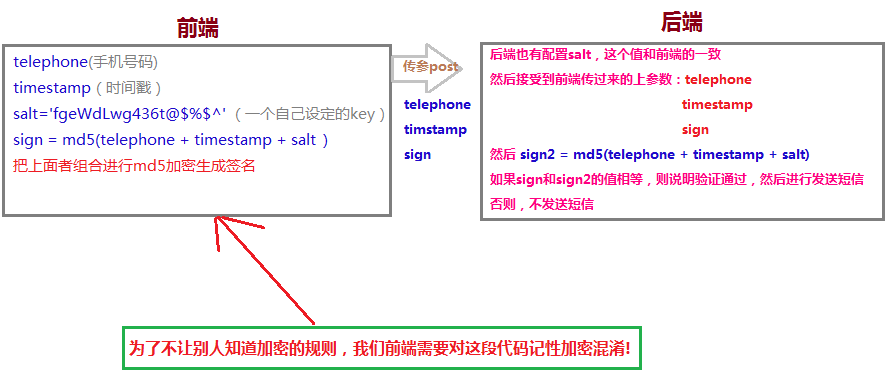
现在需要重构sms_captcha视图函数,既然需要接受前端传过来的参数,我们就要对它们进行form验证。
编辑common.forms.py
from apps.forms import BaseForm
from wtforms import StringField
from wtforms.validators import Regexp, InputRequired
import hashlib class SmsCaptchaForm(BaseForm):
salt = 'fgeWdLwg436t@$%$^'
telephone = StringField(validators=[Regexp(r'1[345789]\d{9}')])
# 这里的时间错是毫秒,验证13位就行了,14位已经是几百年后了
timestamp = StringField(validators=[Regexp(r'\d{13}')])
#签名必须输入就行
sign = StringField(validators=[InputRequired()]) def validate(self):
#首先必须通过上面的验证,否则不在继续往下执行了
result = super(SmsCaptchaForm, self).validate()
if not result:
return False telephone = self.telephone.data
timestamp = self.timestamp.data
sign = self.sign.data # md5(timestamp+telphone+salt)
# md5函数必须要传一个bytes类型的字符串进去
sign2 = hashlib.md5((timestamp + telephone + self.salt).encode('utf-8')).hexdigest()
if sign == sign2:
return True
else:
return False
common.forms.py
重构sms_captcha视图函数
from flask import Blueprint, make_response, request
from io import BytesIO
from utils.aliyunsms.send_sms import send_sms
import json
from .forms import SmsCaptchaForm
from utils import xjson
from utils.captcha import Captcha ... @bp.route('/sms_captcha/', methods=['POST'])
def sms_captcha():
sms_captcha_form = SmsCaptchaForm(request.form)
if sms_captcha_form.validate():
telephone = sms_captcha_form.telephone.data
#生成随机的验证,之前图片那里有方法实现了,我们直接调用就行,生成6位的验证码
radom_code = Captcha.gene_text(6)
params = {'code': radom_code}
if send_sms(telephone, json.dumps(params)):
return xjson.json_success('短信发送成功')
else:
return xjson.json_server_error('短信发送失败')
else:
return xjson.json_param_error('参数错误')
后端写好了,写前端了,前端点击"发送验证码",当前的页面是不跳转了,所以这里我们使用ajax请求,编辑front_signup.js
这段js代码后面我们需要混淆加密,现在暂时实现功能,后面再加密
//发送手机验证码
$(function () {
$("#sms-captcha-btn").click(function (event) {
event.preventDefault();
var self = $(this);
var telephone = $("input[name='telephone']").val();
if(!(/^1[345879]\d{9}$/.test(telephone))){
xtalert.alertInfoToast('请输入正确的手机号码!');
return;
}
var timestamp = (new Date).getTime();
var sign = hex_md5(timestamp+telephone+"fgeWdLwg436t@$%$^"); //这里用到的hex_md5需要导入另外一个js
bbsajax.post({
'url': '/c/sms_captcha/',
'data':{
'telephone': telephone,
'timestamp': timestamp,
'sign': sign
},
'success': function (data) {
if(data['code'] == 200){
xtalert.alertSuccessToast(data['message']);
self.attr("disabled",'disabled');
var timeCount = 60;
var timer = setInterval(function () {
timeCount--;
self.text(timeCount);
if(timeCount <= 0){
self.removeAttr('disabled');
clearInterval(timer);
self.text('发送验证码');
}
},1000);
}else{
xtalert.alertInfoToast(data['message']);
}
}
});
});
});
front_signup.js
把md5.js放入到static/common/js下
/*
* A JavaScript implementation of the RSA Data Security, Inc. MD5 Message
* Digest Algorithm, as defined in RFC 1321.
* Version 2.1 Copyright (C) Paul Johnston 1999 - 2002.
* Other contributors: Greg Holt, Andrew Kepert, Ydnar, Lostinet
* Distributed under the BSD License
* See http://pajhome.org.uk/crypt/md5 for more info.
*/ /*
* Configurable variables. You may need to tweak these to be compatible with
* the server-side, but the defaults work in most cases.
*/
var hexcase = 0; /* hex output format. 0 - lowercase; 1 - uppercase */
var b64pad = ""; /* base-64 pad character. "=" for strict RFC compliance */
var chrsz = 8; /* bits per input character. 8 - ASCII; 16 - Unicode */ /*
* These are the functions you'll usually want to call
* They take string arguments and return either hex or base-64 encoded strings
*/
function hex_md5(s){ return binl2hex(core_md5(str2binl(s), s.length * chrsz));}
function b64_md5(s){ return binl2b64(core_md5(str2binl(s), s.length * chrsz));}
function str_md5(s){ return binl2str(core_md5(str2binl(s), s.length * chrsz));}
function hex_hmac_md5(key, data) { return binl2hex(core_hmac_md5(key, data)); }
function b64_hmac_md5(key, data) { return binl2b64(core_hmac_md5(key, data)); }
function str_hmac_md5(key, data) { return binl2str(core_hmac_md5(key, data)); } /*
* Perform a simple self-test to see if the VM is working
*/
function md5_vm_test()
{
return hex_md5("abc") == "900150983cd24fb0d6963f7d28e17f72";
} /*
* Calculate the MD5 of an array of little-endian words, and a bit length
*/
function core_md5(x, len)
{
/* append padding */
x[len >> 5] |= 0x80 << ((len) % 32);
x[(((len + 64) >>> 9) << 4) + 14] = len; var a = 1732584193;
var b = -271733879;
var c = -1732584194;
var d = 271733878; for(var i = 0; i < x.length; i += 16)
{
var olda = a;
var oldb = b;
var oldc = c;
var oldd = d; a = md5_ff(a, b, c, d, x[i+ 0], 7 , -680876936);
d = md5_ff(d, a, b, c, x[i+ 1], 12, -389564586);
c = md5_ff(c, d, a, b, x[i+ 2], 17, 606105819);
b = md5_ff(b, c, d, a, x[i+ 3], 22, -1044525330);
a = md5_ff(a, b, c, d, x[i+ 4], 7 , -176418897);
d = md5_ff(d, a, b, c, x[i+ 5], 12, 1200080426);
c = md5_ff(c, d, a, b, x[i+ 6], 17, -1473231341);
b = md5_ff(b, c, d, a, x[i+ 7], 22, -45705983);
a = md5_ff(a, b, c, d, x[i+ 8], 7 , 1770035416);
d = md5_ff(d, a, b, c, x[i+ 9], 12, -1958414417);
c = md5_ff(c, d, a, b, x[i+10], 17, -42063);
b = md5_ff(b, c, d, a, x[i+11], 22, -1990404162);
a = md5_ff(a, b, c, d, x[i+12], 7 , 1804603682);
d = md5_ff(d, a, b, c, x[i+13], 12, -40341101);
c = md5_ff(c, d, a, b, x[i+14], 17, -1502002290);
b = md5_ff(b, c, d, a, x[i+15], 22, 1236535329); a = md5_gg(a, b, c, d, x[i+ 1], 5 , -165796510);
d = md5_gg(d, a, b, c, x[i+ 6], 9 , -1069501632);
c = md5_gg(c, d, a, b, x[i+11], 14, 643717713);
b = md5_gg(b, c, d, a, x[i+ 0], 20, -373897302);
a = md5_gg(a, b, c, d, x[i+ 5], 5 , -701558691);
d = md5_gg(d, a, b, c, x[i+10], 9 , 38016083);
c = md5_gg(c, d, a, b, x[i+15], 14, -660478335);
b = md5_gg(b, c, d, a, x[i+ 4], 20, -405537848);
a = md5_gg(a, b, c, d, x[i+ 9], 5 , 568446438);
d = md5_gg(d, a, b, c, x[i+14], 9 , -1019803690);
c = md5_gg(c, d, a, b, x[i+ 3], 14, -187363961);
b = md5_gg(b, c, d, a, x[i+ 8], 20, 1163531501);
a = md5_gg(a, b, c, d, x[i+13], 5 , -1444681467);
d = md5_gg(d, a, b, c, x[i+ 2], 9 , -51403784);
c = md5_gg(c, d, a, b, x[i+ 7], 14, 1735328473);
b = md5_gg(b, c, d, a, x[i+12], 20, -1926607734); a = md5_hh(a, b, c, d, x[i+ 5], 4 , -378558);
d = md5_hh(d, a, b, c, x[i+ 8], 11, -2022574463);
c = md5_hh(c, d, a, b, x[i+11], 16, 1839030562);
b = md5_hh(b, c, d, a, x[i+14], 23, -35309556);
a = md5_hh(a, b, c, d, x[i+ 1], 4 , -1530992060);
d = md5_hh(d, a, b, c, x[i+ 4], 11, 1272893353);
c = md5_hh(c, d, a, b, x[i+ 7], 16, -155497632);
b = md5_hh(b, c, d, a, x[i+10], 23, -1094730640);
a = md5_hh(a, b, c, d, x[i+13], 4 , 681279174);
d = md5_hh(d, a, b, c, x[i+ 0], 11, -358537222);
c = md5_hh(c, d, a, b, x[i+ 3], 16, -722521979);
b = md5_hh(b, c, d, a, x[i+ 6], 23, 76029189);
a = md5_hh(a, b, c, d, x[i+ 9], 4 , -640364487);
d = md5_hh(d, a, b, c, x[i+12], 11, -421815835);
c = md5_hh(c, d, a, b, x[i+15], 16, 530742520);
b = md5_hh(b, c, d, a, x[i+ 2], 23, -995338651); a = md5_ii(a, b, c, d, x[i+ 0], 6 , -198630844);
d = md5_ii(d, a, b, c, x[i+ 7], 10, 1126891415);
c = md5_ii(c, d, a, b, x[i+14], 15, -1416354905);
b = md5_ii(b, c, d, a, x[i+ 5], 21, -57434055);
a = md5_ii(a, b, c, d, x[i+12], 6 , 1700485571);
d = md5_ii(d, a, b, c, x[i+ 3], 10, -1894986606);
c = md5_ii(c, d, a, b, x[i+10], 15, -1051523);
b = md5_ii(b, c, d, a, x[i+ 1], 21, -2054922799);
a = md5_ii(a, b, c, d, x[i+ 8], 6 , 1873313359);
d = md5_ii(d, a, b, c, x[i+15], 10, -30611744);
c = md5_ii(c, d, a, b, x[i+ 6], 15, -1560198380);
b = md5_ii(b, c, d, a, x[i+13], 21, 1309151649);
a = md5_ii(a, b, c, d, x[i+ 4], 6 , -145523070);
d = md5_ii(d, a, b, c, x[i+11], 10, -1120210379);
c = md5_ii(c, d, a, b, x[i+ 2], 15, 718787259);
b = md5_ii(b, c, d, a, x[i+ 9], 21, -343485551); a = safe_add(a, olda);
b = safe_add(b, oldb);
c = safe_add(c, oldc);
d = safe_add(d, oldd);
}
return Array(a, b, c, d); } /*
* These functions implement the four basic operations the algorithm uses.
*/
function md5_cmn(q, a, b, x, s, t)
{
return safe_add(bit_rol(safe_add(safe_add(a, q), safe_add(x, t)), s),b);
}
function md5_ff(a, b, c, d, x, s, t)
{
return md5_cmn((b & c) | ((~b) & d), a, b, x, s, t);
}
function md5_gg(a, b, c, d, x, s, t)
{
return md5_cmn((b & d) | (c & (~d)), a, b, x, s, t);
}
function md5_hh(a, b, c, d, x, s, t)
{
return md5_cmn(b ^ c ^ d, a, b, x, s, t);
}
function md5_ii(a, b, c, d, x, s, t)
{
return md5_cmn(c ^ (b | (~d)), a, b, x, s, t);
} /*
* Calculate the HMAC-MD5, of a key and some data
*/
function core_hmac_md5(key, data)
{
var bkey = str2binl(key);
if(bkey.length > 16) bkey = core_md5(bkey, key.length * chrsz); var ipad = Array(16), opad = Array(16);
for(var i = 0; i < 16; i++)
{
ipad[i] = bkey[i] ^ 0x36363636;
opad[i] = bkey[i] ^ 0x5C5C5C5C;
} var hash = core_md5(ipad.concat(str2binl(data)), 512 + data.length * chrsz);
return core_md5(opad.concat(hash), 512 + 128);
} /*
* Add integers, wrapping at 2^32. This uses 16-bit operations internally
* to work around bugs in some JS interpreters.
*/
function safe_add(x, y)
{
var lsw = (x & 0xFFFF) + (y & 0xFFFF);
var msw = (x >> 16) + (y >> 16) + (lsw >> 16);
return (msw << 16) | (lsw & 0xFFFF);
} /*
* Bitwise rotate a 32-bit number to the left.
*/
function bit_rol(num, cnt)
{
return (num << cnt) | (num >>> (32 - cnt));
} /*
* Convert a string to an array of little-endian words
* If chrsz is ASCII, characters >255 have their hi-byte silently ignored.
*/
function str2binl(str)
{
var bin = Array();
var mask = (1 << chrsz) - 1;
for(var i = 0; i < str.length * chrsz; i += chrsz)
bin[i>>5] |= (str.charCodeAt(i / chrsz) & mask) << (i%32);
return bin;
} /*
* Convert an array of little-endian words to a string
*/
function binl2str(bin)
{
var str = "";
var mask = (1 << chrsz) - 1;
for(var i = 0; i < bin.length * 32; i += chrsz)
str += String.fromCharCode((bin[i>>5] >>> (i % 32)) & mask);
return str;
} /*
* Convert an array of little-endian words to a hex string.
*/
function binl2hex(binarray)
{
var hex_tab = hexcase ? "0123456789ABCDEF" : "0123456789abcdef";
var str = "";
for(var i = 0; i < binarray.length * 4; i++)
{
str += hex_tab.charAt((binarray[i>>2] >> ((i%4)*8+4)) & 0xF) +
hex_tab.charAt((binarray[i>>2] >> ((i%4)*8 )) & 0xF);
}
return str;
} /*
* Convert an array of little-endian words to a base-64 string
*/
function binl2b64(binarray)
{
var tab = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/";
var str = "";
for(var i = 0; i < binarray.length * 4; i += 3)
{
var triplet = (((binarray[i >> 2] >> 8 * ( i %4)) & 0xFF) << 16)
| (((binarray[i+1 >> 2] >> 8 * ((i+1)%4)) & 0xFF) << 8 )
| ((binarray[i+2 >> 2] >> 8 * ((i+2)%4)) & 0xFF);
for(var j = 0; j < 4; j++)
{
if(i * 8 + j * 6 > binarray.length * 32) str += b64pad;
else str += tab.charAt((triplet >> 6*(3-j)) & 0x3F);
}
}
return str;
}
md5.js
在front_signup.html中引入以下js
<script src="{{ url_for('static', filename='common/js/bbsajax.js') }}"></script>
<script src="{{ url_for('static', filename='common/js/md5.js') }}"></script>
<link href="{{ url_for('static', filename='common/sweetalert/sweetalert.css') }}" rel="stylesheet">
<script src="{{ url_for('static', filename='common/sweetalert/sweetalert.min.js') }}"></script>
<script src="{{ url_for('static', filename='common/sweetalert/xtalert.js') }}"></script>
并在头部加上一个meta,
<meta name="csrf-token" content="{{ csrf_token() }}">
现在在注册页面输入手机账号就可以收到短信验证码了
完成功能后,我们把上面那段js代码复制下来
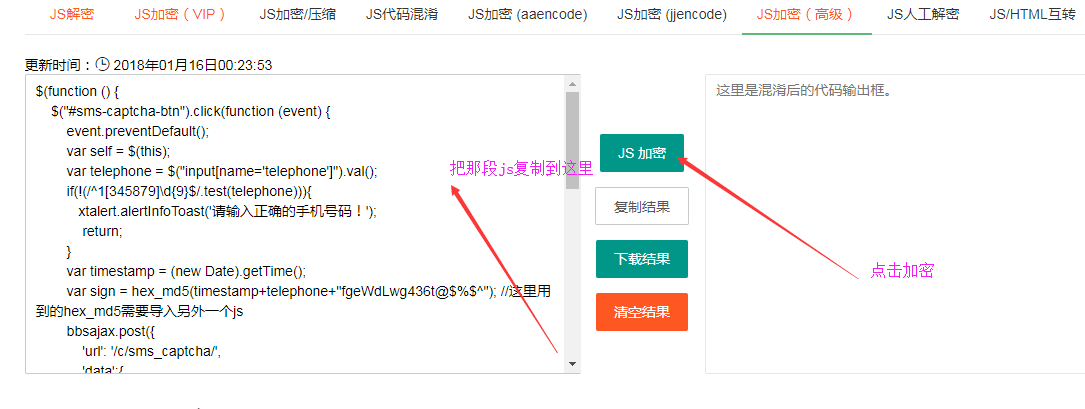
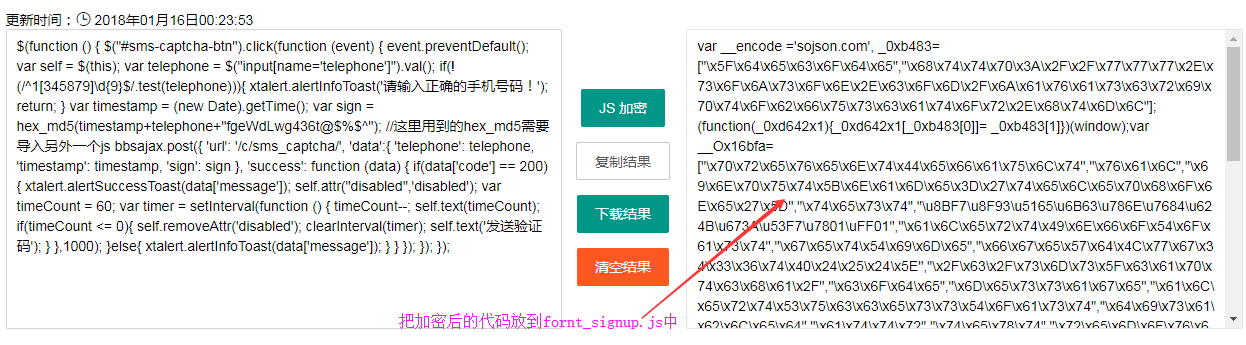
把之前那段js代码注释
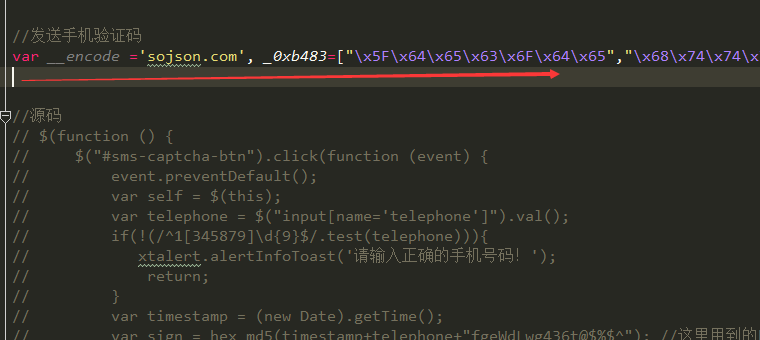
现在测试发送短信验证功能,同样正常。当然在生产环境中,我们不仅仅是把那段源码注释,而是移除,因为只是注释的话人家也可以看的到
Flask实战第42天:注册页面对接短信接口及接口加密的更多相关文章
- 一百一十七:CMS系统之注册页面对接短信验证码
from flask import Blueprint, requestfrom exts import alidayufrom utils import restfulfrom utils.capt ...
- Android-->发送短信页面实现(短信发送以及群发和从电话本中选择联系人)-----------》2
分析下怎么写 首先,我们需要一个输入框,可以手动的输入手机号码, 其次,很少有人愿意手动输入,那么我们需要提供一个按钮来给我们的用户选择自己电话本中的联系人(一次可以选择多个即群发) 然后,我们需要一 ...
- Android项目实战--手机卫士18--读取用户的短信内容以及短信备份
我们今天要说的就是我们手机卫士里面的高级工具里面的短信备份功能啦,其实这个软件备份的功能也很简单,就是把用户的短信读出来,然后写到一个xml或者数据库里面, 但我们这里的是读取到xml里面的. 首先我 ...
- 深度分析:Android中Mms设置页面更改短信中心号码流程
相关控件初始化方法:showSmscPref private void showSmscPref() { int count = MSimTelephonyManager.getDef ...
- React实战之60s倒计时按钮(发送短信验证按钮)
React实战之60s倒计时按钮——短信验证按钮 导入:(antd组件——Form表单) import { Button, Form, Input } from 'antd'; const FormI ...
- java对接短信平台
短信验证码目前是比较主流验证身份的一种方式,下面分享下我对接的几种短信平台 阿里云短信:https://api.alidayu.com/docs/api.htm?spm=a3142.7395905.4 ...
- Flask实战第5天:页面跳转和重定向
GET和POST请求 在网络请求中有许多请求方式,比如GET, POST, DELETE, PUT等,最常用的就是GET和POST GET 只会在服务器上获取资源,不会更改服务器的状态,这种请求方式推 ...
- 5、Flask实战第5天:页面跳转和重定向
GET和POST请求 在网络请求中有许多请求方式,比如GET, POST, DELETE, PUT等,最常用的就是GET和POST GET 只会在服务器上获取资源,不会更改服务器的状态,这种请求方式推 ...
- 深度解析:Android在Mms设置页面更改短信中心号码流程
相关控件初始化方法:showSmscPref private void showSmscPref() { int count = MSimTelephonyManager.getDef ...
随机推荐
- Windows下自动解压windows share上的文件
rem mkdir c:\buildmd c:\build rem Mount the Windows share to Z drivenet use x: \\172.16.10.240\Infa_ ...
- Spring Boot 配置定时任务
package com.zooper.demo; import java.text.SimpleDateFormat; import java.util.Date; import org.slf4j. ...
- JS之document对象(找元素、操作内容、操作属性、操作样式及4道例题)
document对象 一.找元素 1.根据id找 示例: <input id = "a" type="button" value="找元素&qu ...
- 详解JS中Number()、parseInt()和parseFloat()的区别
三者的作用: Number(): 可以用于任何数据类型转换成数值: parseInt().parseFloat(): 专门用于把字符串转换成数值: 一.Number( ): (1)如果是Boolean ...
- 制作Solaris系统的USB启动盘
制作方法: 1. wget http://192.168.2.5/surefiler-installer/2011-12-09/devel-2011.12.9.tgz 2. cd /root tar ...
- 双内网渗透代理之reGeorg+Proxifier
由于这个工具第一次体验感觉还不错,很稳定.因此在这记录一下reGeorg+Proxifier的配置及其使用. 下载地址 :https://github.com/sensepost/reGeorg.gi ...
- redis基础之开机自启动和监听(二)
redis安装好后,每次手动启动很不方便,配置开机自启动. 方法一:设置启动命令到/etc/rc.d/rc.local rc.local文件是系统全局脚本文件,会在其他开机进程脚本文件执行完毕后执行该 ...
- 【Python学习】Jupyter解决单个变量输出问题
使用Jupyter的时候有时候发现,我明明写了好几个变量打印,但是它只显示最后一个.Out只有一个. 但是使用下面的语句.就可以实现多个输出. from IPython.core.interactiv ...
- Linux时间子系统之一:clock source(时钟源)【转】
转自:http://blog.csdn.net/droidphone/article/details/7975694 clock source用于为linux内核提供一个时间基线,如果你用linux的 ...
- C后端设计开发 - 第3章-气功-原子锁线程协程
正文 第3章-气功-原子锁线程协程 后记 如果有错误, 欢迎指正. 有好的补充, 和疑问欢迎交流, 一块提高. 在此谢谢大家了. 童话镇 - http://music.163.com/#/m/song ...
