CDH构建大数据平台-配置集群的Kerberos认证安全
CDH构建大数据平台-配置集群的Kerberos认证安全
作者:尹正杰
版权声明:原创作品,谢绝转载!否则将追究法律责任。
当平台用户使用量少的时候我们可能不会在一集群安全功能的缺失,因为用户少,团队规模小,相对容易把控,开发人员直接也彼此了解。这时候只需要做好团队内部或是企业通过一些列行政管理手段就能管理好集群的安全问题。但是别忘了我们的平台定位可是作为一个单一的大数据来支持企业内部所有应用的。正所谓人上一百,形形色色。当平台用户达到一定数量之后其素质难免会参差不齐,大数据平台面对的也不再是一个小团队了。这时候考团队自觉或是单纯地通过规章制度都很难再起到有效的作用。作为一个企业级平台,安全问题不容小觑。详情请参考:构建企业级平台安全方案。
一.Kerberos基础
1>.为什么需要Kerberos
Hadoop集群默认采用基于操作系统账号的Simple 认证,基本没有安全性保证,用户只需在客户端的操作系统上建立一个 同名账号,即可伪装成任何用户访问集群。
2>.什么是Kerberos
Kerberos是一个网络认证的框架协议,它的命名灵感来自于希腊神话中一只三头犬守护兽,寓意其拥有强大的保护能力。Kerberos协议通过强大密钥系统为Server(服务端)和Client(客户端)应用程序之间提供强大的通信加密和认证服务。在使用Kerberos协议认证的集群中,Client不会直接和他的Server服务进行通信认证,而是通过KDC(key Distribution Center)这样一个独立的服务来完成互相之间的认证。同时Kerberos 还能将服务之间的全部通信进行加密以保证其隐私于完整性。 Kerberos由麻省理工学院创建,作为解决这些网络安全问题的解决方案。Kerberos协议使用强加密技术,以便客户端可以通过不安全的网络连接向服务器(反之亦然)证明其身份。在客户端和服务器使用Kerberos证明其身份后,他们还可以加密所有通信,以确保在业务开展时的隐私和数据完整性。详情请参考:https://web.mit.edu/kerberos/。
3>.Kerberos核心概念(相关术语)
Kerberos协议中有一些重要的概念,了解这些概念有助于我们理解Kerberos的认证过程。 >.KDC(Key Distribution Centor):
KDC用于验证各个模块,是统一认证服务。换句话说就是,可信任的认证来源,密钥分发中心。
除了以文件形式存储的数据库之外,KDC还包含两个重要的组件:认证服务(AS)和先前讨论过的TGS。AS和TGS一起处理受Kerberos保护的Hadoop集群的所有认证和访问请求。Kerberos数据库存储主体和领域信息。
>.Kerberos KDC Server:
KDC所在的服务器,即KDC服务的提供者。存储与用户,主机和服务相关的所有主体信息,包括它们的领域信息。
>.Kerberos Client
任何一个需要通过KDC认证的机器(或模块)。比如客户端,需要做Kerberos 认证的机器。 >.Principal
用于验证一个用户或者一个Service的唯一标识,相当于一个账号,需要为其设置密码。
当用户想要对Kerberos支持的集群进行身份验证时,管理服务生成票据。该票据包含用户名(通常与用户主体相同),服务主体,客户端的IP地址和时间戳等信息。票据具有一个可配置的最长生命周期和一个会话密钥。用户还可以在特定时间内对票据续期。
>.Keytab文件
包含一个或多个Principal以及其密码的文件,可用于用户登录。一个包含一个或多个Principal及其密码的 文件,可以代替输入密码进行验证。
keytab文件是一个安全文件,其中包含领域所有服务主体的密码。每个Hadoop服务都要求在所有主机上放置一个keytab文件。当kerberos需要更新服务TGT时,它会查找keytab文件。
>.Relam(域)
由KDC以及多个Kerberos Client组成的网络,即认证的域。
域是认证用户的基本管理域,用于建立管理服务器对用户,主机和服务进行身份验证的边界。每个hadoop用户被分配到一个特定的郁。通常用大写字母指定一个域,例如YINZHENGJIE.COM。可以有多个KDC,因此在单个网络中可以有多个域。
主体是指定域的一部分用户,宿主或服务。用户主体和服务主体通常是比较常见的。UPN表示普通用户。SPN是运行Hadoop服务或后台进程所必须的登陆名,包括HDFS和YARN等Hadoop服务。
>.KDC Admin Account
KDC中拥有管理权限的用户(例如添加,修改,删除Principal)。即KDC管理员帐户,有权添加其他Principal >.Authentication Sever(简称AS,即认证服务)
用于初始化认证,并生成Ticket Granting Ticket(TGT)。
一旦用户成功地向AS进行了身份验证,则AS向安全集群中的其他服务认证和客户端授予TGT。这些票据是用于客户端向服务器进行省份验证,有一定时效的加密信息。然后,主体使用TGT来请求认证和访问Hadoop服务。 >.Ticket Granting Server(TGS)
在TGT的基础上生成Service Ticket。一般情况下AS和TGS都在KDC的Server上。
票据验证服务器验证客户端传递的TGT,然后给客户端服务授予票据,以便它们可以访问hadoop服务。服务票据使验证后的主体能够使用集群中的服务。
4>.Kerberos的认证流程
Kerberos协议主要由Key分发中心(即KDC,全称“Key Distribution Centor”),服务提供者(Server)和用户(User)三部分组成,它的认证过程如下图所示:
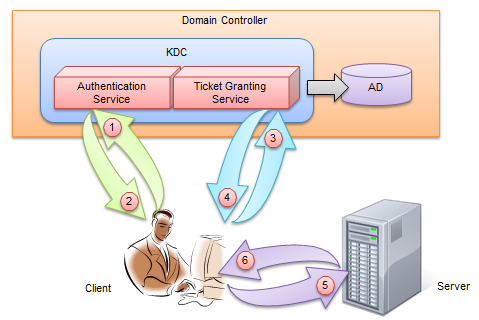
第 步:
client(一个User或者一个Service)会用Pricipal到Authentication Sever(AS)去认证,希望获取访问server的权限。 第 步:
kerberos得到了这个消息,首先得判断client是否是可信赖的,也就是白名单黑名单的说法。这就是AS服务完成的工作,通过在AD中存储黑名单和白名单来区分client。验证成功后,AS返回TGT给client。 第 步:
这时只有AS和这个Principal的使用者可以识别该TGT。在拿到加密的TGT之后,client(User或者Service)会使用Principal的Key来解密TGT。并使用解密后的TGT继续向kerberos请求,希望获取访问server的权限。 第 步:
kerberos又一次得到了这个消息,这时候通过client(User或者Service)消息中的TGT(注意:此时的TGT是第三步中解密后的TGT,并不是第二步的TGT哟!),判断出了client拥有了这个权限,给了client访问server的权限Server Ticket。 第 ~ 步:
client得到希望访问的Server Ticket后,终于可以成功访问该Server。需要注意的是,得到的这个Server Ticket只是针对这台Server,其他server需要继续向TGS申请(因为每台服务器都有自己的Server Ticket哟!)。在Kerberos认证的集群中,只有拿着这个Service Ticket才可以访问真正的Server从而实现自己的业务逻辑。
5>.Kerberos的优点
分析整个Kerberos的认证过程之后,我们来总结一下Kerberos都有哪些优点: >.较高的Performance
虽然我们一再地说Kerberos是一个涉及到3方的认证过程:Client、Server、KDC。但是一旦Client获得用过访问某个Server的Ticket,该Server就能根据这个Ticket实现对Client的验证,而无须KDC的再次参与。和传统的基于Windows NT .0的每个完全依赖Trusted Third Party的NTLM比较,具有较大的性能提升。 >.实现了双向验证(Mutual Authentication)
传统的NTLM认证基于这样一个前提:Client访问的远程的Service是可信的、无需对于进行验证,所以NTLM不曾提供双向验证的功能。这显然有点理想主义,为此Kerberos弥补了这个不足:Client在访问Server的资源之前,可以要求对Server的身份执行认证。 >.对Delegation的支持
Impersonation和Delegation是一个分布式环境中两个重要的功能。Impersonation允许Server在本地使用Logon 的Account执行某些操作,Delegation需用Server将logon的Account带入到另过一个Context执行相应的操作。NTLM仅对Impersonation提供支持,而Kerberos通过一种双向的、可传递的(Mutual 、Transitive)信任模式实现了对Delegation的支持。 >.互操作性(Interoperability)
Kerberos最初由MIT首创,现在已经成为一行被广泛接受的标准。所以对于不同的平台可以进行广泛的互操作。
感兴趣的小伙伴,如果搭建Kerberos?感兴趣的小伙伴可以参考我的笔记:使用FreeIPA安装Kerberos和LDAP。
二.基于yum的方式搭建Kerberos服务器
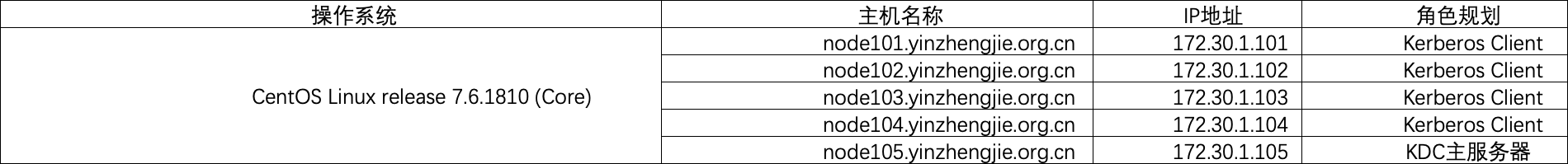
1>.规划kdc服务器
2>. 安装Kerberos服务器和客户端
[root@node105 ~]# yum -y install krb5-server krb5-libs krb5-workstation
Loaded plugins: fastestmirror, priorities
Determining fastest mirrors
* base: mirrors.aliyun.com
* extras: mirrors.huaweicloud.com
* updates: mirrors.nwsuaf.edu.cn
base | 3.6 kB ::
cloudera-manager | 2.9 kB ::
extras | 3.4 kB ::
updates | 3.4 kB ::
(/): extras//x86_64/primary_db | kB ::
(/): updates//x86_64/primary_db | 2.5 MB ::
Package krb5-libs-1.15.-.el7_6.x86_64 already installed and latest version
Resolving Dependencies
--> Running transaction check
---> Package krb5-server.x86_64 :1.15.-.el7_6 will be installed
updates//x86_64/filelists_db | 2.2 MB ::
--> Processing Dependency: libverto-module-base for package: krb5-server-1.15.-.el7_6.x86_64
--> Processing Dependency: /usr/share/dict/words for package: krb5-server-1.15.-.el7_6.x86_64
extras//x86_64/filelists_db | kB ::
---> Package krb5-workstation.x86_64 :1.15.-.el7_6 will be installed
--> Running transaction check
---> Package libverto-libevent.x86_64 :0.2.-.el7 will be installed
--> Processing Dependency: libevent-2.0.so.()(64bit) for package: libverto-libevent-0.2.-.el7.x86_64
---> Package words.noarch :3.0-.el7 will be installed
--> Running transaction check
---> Package libevent.x86_64 :2.0.-.el7 will be installed
--> Finished Dependency Resolution Dependencies Resolved ==============================================================================================================================================================================================
Package Arch Version Repository Size
==============================================================================================================================================================================================
Installing:
krb5-server x86_64 1.15.-.el7_6 updates 1.0 M
krb5-workstation x86_64 1.15.-.el7_6 updates k
Installing for dependencies:
libevent x86_64 2.0.-.el7 base k
libverto-libevent x86_64 0.2.-.el7 base 8.9 k
words noarch 3.0-.el7 base 1.4 M Transaction Summary
==============================================================================================================================================================================================
Install Packages (+ Dependent packages) Total download size: 3.4 M
Installed size: 9.3 M
Downloading packages:
(/): libevent-2.0.-.el7.x86_64.rpm | kB ::
(/): libverto-libevent-0.2.-.el7.x86_64.rpm | 8.9 kB ::
(/): krb5-workstation-1.15.-.el7_6.x86_64.rpm | kB ::
(/): words-3.0-.el7.noarch.rpm | 1.4 MB ::
(/): krb5-server-1.15.-.el7_6.x86_64.rpm | 1.0 MB ::
----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
Total 1.1 MB/s | 3.4 MB ::
Running transaction check
Running transaction test
Transaction test succeeded
Running transaction
Installing : words-3.0-.el7.noarch /
Installing : libevent-2.0.-.el7.x86_64 /
Installing : libverto-libevent-0.2.-.el7.x86_64 /
Installing : krb5-server-1.15.-.el7_6.x86_64 /
Installing : krb5-workstation-1.15.-.el7_6.x86_64 /
Verifying : krb5-workstation-1.15.-.el7_6.x86_64 /
Verifying : libverto-libevent-0.2.-.el7.x86_64 /
Verifying : libevent-2.0.-.el7.x86_64 /
Verifying : krb5-server-1.15.-.el7_6.x86_64 /
Verifying : words-3.0-.el7.noarch / Installed:
krb5-server.x86_64 :1.15.-.el7_6 krb5-workstation.x86_64 :1.15.-.el7_6 Dependency Installed:
libevent.x86_64 :2.0.-.el7 libverto-libevent.x86_64 :0.2.-.el7 words.noarch :3.0-.el7 Complete!
[root@node105 ~]#
[root@node105 ~]# yum -y install krb5-server krb5-libs krb5-workstation
3>.修改kdc.conf
[root@node105 ~]# cat /var/kerberos/krb5kdc/kdc.conf
[kdcdefaults]
kdc_ports =
kdc_tcp_ports = [realms]
YINZHENGJIE.ORG.CN = {
master_key_type = aes256-cts #我们可以启动aes256加密算法,需要JDK打上JCE补丁。我们之前已经打过补丁了,实际上是可以启动的。
max_renewable_life= 7d 0h 0m 0s #我们这里为租约持续约期的最长时间。以下几个参数大多数都是指定路径,我们默认即可,不需要修改!
acl_file = /var/kerberos/krb5kdc/kadm5.acl
dict_file = /usr/share/dict/words
admin_keytab = /var/kerberos/krb5kdc/kadm5.keytab
supported_enctypes = aes256-cts:normal aes128-cts:normal des3-hmac-sha1:normal arcfour-hmac:normal camellia256-cts:normal camellia128-cts:normal des-hmac-sha1:normal des-cbc-md5:normal des-cbc-crc:normal
}
[root@node105 ~]#
[root@node105 ~]#
4>.修改krb5.conf
[root@node105 ~]# cat /etc/krb5.conf
# Configuration snippets may be placed in this directory as well
includedir /etc/krb5.conf.d/ [logging]
default = FILE:/var/log/krb5libs.log
kdc = FILE:/var/log/krb5kdc.log
admin_server = FILE:/var/log/kadmind.log [libdefaults]
dns_lookup_realm = false
ticket_lifetime = 24h
renew_lifetime = 7d
forwardable = true
rdns = false
pkinit_anchors = /etc/pki/tls/certs/ca-bundle.crt
default_realm = YINZHENGJIE.ORG.CN [realms]
YINZHENGJIE.ORG.CN = {
kdc = node105.yinzhengjie.org.cn
admin_server = node105.yinzhengjie.org.cn
} [domain_realm]
.yinzhengjie.org.cn = YINZHENGJIE.ORG.CN
yinzhengjie.org.cn = YINZHENGJIE.ORG.CN
[root@node105 ~]#
[root@node105 ~]#
5>.初始化Kerberos数据库
[root@node105 ~]# kdb5_util create -s
Loading random data
Initializing database '/var/kerberos/krb5kdc/principal' for realm 'YINZHENGJIE.ORG.CN',
master key name 'K/M@YINZHENGJIE.ORG.CN'
You will be prompted for the database Master Password.
It is important that you NOT FORGET this password.
Enter KDC database master key: #这里需要给KDC设置一个初始密码,注意,该密码我们一定要记住,他是用来管理KDC服务器的哟!
Re-enter KDC database master key to verify:
[root@node105 ~]#
6>.创建管理员用户和普通用户
创建过程中都需要设置密码。然后为user用户生成keytab文件,便于后续免密登录,不指定路径的话默认放在当前工作目录,我们指定到“/etc/ security/”下。
[root@node105 ~]#
[root@node105 ~]# kadmin.local #本地登陆KDC服务器
Authenticating as principal root/admin@YINZHENGJIE.ORG.CN with password.
kadmin.local:
kadmin.local:
kadmin.local: addprinc admin/admin #咱们这里创建一个管理员用户
WARNING: no policy specified for admin/admin@YINZHENGJIE.ORG.CN; defaulting to no policy
Enter password for principal "admin/admin@YINZHENGJIE.ORG.CN":
Re-enter password for principal "admin/admin@YINZHENGJIE.ORG.CN":
Principal "admin/admin@YINZHENGJIE.ORG.CN" created.
kadmin.local:
kadmin.local:
kadmin.local: addprinc jason #创建一个普通用户jason
WARNING: no policy specified for jason@YINZHENGJIE.ORG.CN; defaulting to no policy
Enter password for principal "jason@YINZHENGJIE.ORG.CN":
Re-enter password for principal "jason@YINZHENGJIE.ORG.CN":
Principal "jason@YINZHENGJIE.ORG.CN" created.
kadmin.local:
kadmin.local:
kadmin.local: addprinc yinzhengjie #创建一个普通用户yinzhengjie
WARNING: no policy specified for yinzhengjie@YINZHENGJIE.ORG.CN; defaulting to no policy
Enter password for principal "yinzhengjie@YINZHENGJIE.ORG.CN":
Re-enter password for principal "yinzhengjie@YINZHENGJIE.ORG.CN":
Principal "yinzhengjie@YINZHENGJIE.ORG.CN" created.
kadmin.local:
kadmin.local:
kadmin.local: xst -k /etc/security/jason.keytab jason #为jason用户生成keytab文件
Entry for principal jason with kvno , encryption type aes256-cts-hmac-sha1- added to keytab WRFILE:/etc/security/jason.keytab.
Entry for principal jason with kvno , encryption type aes128-cts-hmac-sha1- added to keytab WRFILE:/etc/security/jason.keytab.
Entry for principal jason with kvno , encryption type des3-cbc-sha1 added to keytab WRFILE:/etc/security/jason.keytab.
Entry for principal jason with kvno , encryption type arcfour-hmac added to keytab WRFILE:/etc/security/jason.keytab.
Entry for principal jason with kvno , encryption type camellia256-cts-cmac added to keytab WRFILE:/etc/security/jason.keytab.
Entry for principal jason with kvno , encryption type camellia128-cts-cmac added to keytab WRFILE:/etc/security/jason.keytab.
Entry for principal jason with kvno , encryption type des-hmac-sha1 added to keytab WRFILE:/etc/security/jason.keytab.
Entry for principal jason with kvno , encryption type des-cbc-md5 added to keytab WRFILE:/etc/security/jason.keytab.
kadmin.local:
kadmin.local: xst -k /etc/security/yinzhengjie.keytab yinzhengjie #为yinzhengjie用户生成keytab文件
Entry for principal yinzhengjie with kvno , encryption type aes256-cts-hmac-sha1- added to keytab WRFILE:/etc/security/yinzhengjie.keytab.
Entry for principal yinzhengjie with kvno , encryption type aes128-cts-hmac-sha1- added to keytab WRFILE:/etc/security/yinzhengjie.keytab.
Entry for principal yinzhengjie with kvno , encryption type des3-cbc-sha1 added to keytab WRFILE:/etc/security/yinzhengjie.keytab.
Entry for principal yinzhengjie with kvno , encryption type arcfour-hmac added to keytab WRFILE:/etc/security/yinzhengjie.keytab.
Entry for principal yinzhengjie with kvno , encryption type camellia256-cts-cmac added to keytab WRFILE:/etc/security/yinzhengjie.keytab.
Entry for principal yinzhengjie with kvno , encryption type camellia128-cts-cmac added to keytab WRFILE:/etc/security/yinzhengjie.keytab.
Entry for principal yinzhengjie with kvno , encryption type des-hmac-sha1 added to keytab WRFILE:/etc/security/yinzhengjie.keytab.
Entry for principal yinzhengjie with kvno , encryption type des-cbc-md5 added to keytab WRFILE:/etc/security/yinzhengjie.keytab.
kadmin.local:
kadmin.local: quit
[root@node105 ~]#
[root@node105 ~]#
[root@node105 ~]# ll /etc/security/*.keytab
-rw------- 1 root root 554 Mar 8 11:42 /etc/security/jason.keytab
-rw------- 1 root root 602 Mar 8 11:43 /etc/security/yinzhengjie.keytab
[root@node105 ~]#
7>.设置ACL权限
[root@node105 ~]# cat /var/kerberos/krb5kdc/kadm5.acl
*/admin@YINZHENGJIE.ORG.CN *
[root@node105 ~]#
8>.启动Kerberos服务,并设为开机启动
[root@node105 ~]#
[root@node105 ~]# systemctl start krb5kdc
[root@node105 ~]#
[root@node105 ~]# systemctl start kadmin
[root@node105 ~]#
[root@node105 ~]# systemctl enable krb5kdc
Created symlink from /etc/systemd/system/multi-user.target.wants/krb5kdc.service to /usr/lib/systemd/system/krb5kdc.service.
[root@node105 ~]#
[root@node105 ~]# systemctl enable kadmin
Created symlink from /etc/systemd/system/multi-user.target.wants/kadmin.service to /usr/lib/systemd/system/kadmin.service.
[root@node105 ~]#
[root@node105 ~]#
9>.测试kerberos是否服务正常
[root@node105 ~]#
[root@node105 ~]# kinit -kt /etc/security/yinzhengjie.keytab yinzhengjie
[root@node105 ~]#
[root@node105 ~]# klist
Ticket cache: FILE:/tmp/krb5cc_0
Default principal: yinzhengjie@YINZHENGJIE.ORG.CN Valid starting Expires Service principal
// :: // :: krbtgt/YINZHENGJIE.ORG.CN@YINZHENGJIE.ORG.CN
renew until // ::
[root@node105 ~]#
[root@node105 ~]#
10>.在node[101-104].yinzhengjie.org.cn这4个节点上安装kerberos client
[root@node101 ~]# yum -y install krb5-libs krb5-workstation
Loaded plugins: fastestmirror
Determining fastest mirrors
* base: mirrors.aliyun.com
* extras: mirrors.aliyun.com
* updates: mirrors.aliyun.com
base | 3.6 kB ::
cloudera-manager | 2.9 kB ::
extras | 3.4 kB ::
mysql-connectors-community | 2.5 kB ::
mysql-tools-community | 2.5 kB ::
mysql80-community | 2.5 kB ::
updates | 3.4 kB ::
zabbix | 2.9 kB ::
zabbix-non-supported | B ::
(/): zabbix/x86_64/primary_db | kB ::
(/): updates//x86_64/primary_db | 2.5 MB ::
Package krb5-libs-1.15.-.el7_6.x86_64 already installed and latest version
Resolving Dependencies
--> Running transaction check
---> Package krb5-workstation.x86_64 :1.15.-.el7_6 will be installed
--> Finished Dependency Resolution Dependencies Resolved =====================================================================================================================================================================
Package Arch Version Repository Size
=====================================================================================================================================================================
Installing:
krb5-workstation x86_64 1.15.-.el7_6 updates k Transaction Summary
=====================================================================================================================================================================
Install Package Total download size: k
Installed size: 2.5 M
Downloading packages:
krb5-workstation-1.15.-.el7_6.x86_64.rpm | kB ::
Running transaction check
Running transaction test
Transaction test succeeded
Running transaction
Installing : krb5-workstation-1.15.-.el7_6.x86_64 /
Verifying : krb5-workstation-1.15.-.el7_6.x86_64 / Installed:
krb5-workstation.x86_64 :1.15.-.el7_6 Complete!
[root@node101 ~]#
[root@node101 ~]# yum -y install krb5-libs krb5-workstation
[root@node102 ~]# yum -y install krb5-libs krb5-workstation
Loaded plugins: fastestmirror
Determining fastest mirrors
* base: mirrors.huaweicloud.com
* extras: mirror.jdcloud.com
* updates: ap.stykers.moe
base | 3.6 kB ::
cloudera-manager | 2.9 kB ::
extras | 3.4 kB ::
updates | 3.4 kB ::
zabbix | 2.9 kB ::
zabbix-non-supported | B ::
(/): zabbix/x86_64/primary_db | kB ::
(/): updates//x86_64/primary_db | 2.5 MB ::
Package krb5-libs-1.15.-.el7_6.x86_64 already installed and latest version
Resolving Dependencies
--> Running transaction check
---> Package krb5-workstation.x86_64 :1.15.-.el7_6 will be installed
--> Finished Dependency Resolution Dependencies Resolved =====================================================================================================================================================================
Package Arch Version Repository Size
=====================================================================================================================================================================
Installing:
krb5-workstation x86_64 1.15.-.el7_6 updates k Transaction Summary
=====================================================================================================================================================================
Install Package Total download size: k
Installed size: 2.5 M
Downloading packages:
krb5-workstation-1.15.-.el7_6.x86_64.rpm | kB ::
Running transaction check
Running transaction test
Transaction test succeeded
Running transaction
Installing : krb5-workstation-1.15.-.el7_6.x86_64 /
Verifying : krb5-workstation-1.15.-.el7_6.x86_64 / Installed:
krb5-workstation.x86_64 :1.15.-.el7_6 Complete!
[root@node102 ~]#
[root@node102 ~]# yum -y install krb5-libs krb5-workstation
[root@node103 ~]# yum -y install krb5-libs krb5-workstation
Loaded plugins: fastestmirror
Determining fastest mirrors
* base: mirrors.aliyun.com
* extras: mirrors.aliyun.com
* updates: mirrors.aliyun.com
base | 3.6 kB ::
cloudera-manager | 2.9 kB ::
extras | 3.4 kB ::
updates | 3.4 kB ::
zabbix | 2.9 kB ::
zabbix-non-supported | B ::
(/): zabbix/x86_64/primary_db | kB ::
(/): updates//x86_64/primary_db | 2.5 MB ::
Package krb5-libs-1.15.-.el7_6.x86_64 already installed and latest version
Resolving Dependencies
--> Running transaction check
---> Package krb5-workstation.x86_64 :1.15.-.el7_6 will be installed
--> Finished Dependency Resolution Dependencies Resolved =====================================================================================================================================================================
Package Arch Version Repository Size
=====================================================================================================================================================================
Installing:
krb5-workstation x86_64 1.15.-.el7_6 updates k Transaction Summary
=====================================================================================================================================================================
Install Package Total download size: k
Installed size: 2.5 M
Downloading packages:
krb5-workstation-1.15.-.el7_6.x86_64.rpm | kB ::
Running transaction check
Running transaction test
Transaction test succeeded
Running transaction
Installing : krb5-workstation-1.15.-.el7_6.x86_64 /
Verifying : krb5-workstation-1.15.-.el7_6.x86_64 / Installed:
krb5-workstation.x86_64 :1.15.-.el7_6 Complete!
[root@node103 ~]#
[root@node103 ~]# yum -y install krb5-libs krb5-workstation
[root@node104 ~]#
[root@node104 ~]# yum -y install krb5-libs krb5-workstation
Loaded plugins: fastestmirror
Determining fastest mirrors
* base: mirrors.shu.edu.cn
* extras: mirror.jdcloud.com
* updates: mirrors.shu.edu.cn
base | 3.6 kB ::
cloudera-manager | 2.9 kB ::
extras | 3.4 kB ::
updates | 3.4 kB ::
zabbix | 2.9 kB ::
zabbix-non-supported | B ::
(/): zabbix/x86_64/primary_db | kB ::
(/): updates//x86_64/primary_db | 2.5 MB ::
Package krb5-libs-1.15.-.el7_6.x86_64 already installed and latest version
Resolving Dependencies
--> Running transaction check
---> Package krb5-workstation.x86_64 :1.15.-.el7_6 will be installed
--> Finished Dependency Resolution Dependencies Resolved =====================================================================================================================================================================
Package Arch Version Repository Size
=====================================================================================================================================================================
Installing:
krb5-workstation x86_64 1.15.-.el7_6 updates k Transaction Summary
=====================================================================================================================================================================
Install Package Total download size: k
Installed size: 2.5 M
Downloading packages:
krb5-workstation-1.15.-.el7_6.x86_64.rpm | kB ::
Running transaction check
Running transaction test
Transaction test succeeded
Running transaction
Installing : krb5-workstation-1.15.-.el7_6.x86_64 /
Verifying : krb5-workstation-1.15.-.el7_6.x86_64 / Installed:
krb5-workstation.x86_64 :1.15.-.el7_6 Complete!
[root@node104 ~]#
[root@node104 ~]# yum -y install krb5-libs krb5-workstation
11>.将node101.yinzhengjie.org.cn的KDC服务器中krb5.conf配置文件拷贝到集群到node[101-104].yinzhengjie.org.cn这4个节点上
[root@node105 ~]# scp /etc/krb5.conf root@node101.yinzhengjie.org.cn:/etc/krb5.conf
The authenticity of host 'node101.yinzhengjie.org.cn (172.30.1.101)' can't be established.
ECDSA key fingerprint is SHA256:8R1Js16byvwxauh59uGbvhYv0xiV23wKz0zqqPUVMZ0.
ECDSA key fingerprint is MD5:::f7:a7:::f9:::9b:5c:6d::f2:5a:f2.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added 'node101.yinzhengjie.org.cn,172.30.1.101' (ECDSA) to the list of known hosts.
root@node101.yinzhengjie.org.cn's password:
krb5.conf % .0KB/s :
[root@node105 ~]#
[root@node105 ~]# scp /etc/krb5.conf root@node101.yinzhengjie.org.cn:/etc/krb5.conf
[root@node105 ~]#
[root@node105 ~]# scp /etc/krb5.conf root@node102.yinzhengjie.org.cn:/etc/krb5.conf
The authenticity of host 'node102.yinzhengjie.org.cn (172.30.1.102)' can't be established.
ECDSA key fingerprint is SHA256:j9+Xbv//tjagB4nYMZgFLY+d4gdUyoW5fm6ZRaK+wcw.
ECDSA key fingerprint is MD5:b8::2d:d1:de:dd::9f:db::2f:2e::8e::ff.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added 'node102.yinzhengjie.org.cn,172.30.1.102' (ECDSA) to the list of known hosts.
root@node102.yinzhengjie.org.cn's password:
krb5.conf % .2KB/s :
[root@node105 ~]#
[root@node105 ~]# scp /etc/krb5.conf root@node102.yinzhengjie.org.cn:/etc/krb5.conf
[root@node105 ~]#
[root@node105 ~]# scp /etc/krb5.conf root@node103.yinzhengjie.org.cn:/etc/krb5.conf
The authenticity of host 'node103.yinzhengjie.org.cn (172.30.1.103)' can't be established.
ECDSA key fingerprint is SHA256:VXfIuFeaED1V3Er0vzHWVZLw8Ks9tF0ym2VKR0ayIqM.
ECDSA key fingerprint is MD5:ac:::1d:8d::d4:7a:0b:::6d::7f:5d:e0.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added 'node103.yinzhengjie.org.cn,172.30.1.103' (ECDSA) to the list of known hosts.
root@node103.yinzhengjie.org.cn's password:
krb5.conf % .3KB/s :
[root@node105 ~]#
[root@node105 ~]# scp /etc/krb5.conf root@node103.yinzhengjie.org.cn:/etc/krb5.conf
[root@node105 ~]#
[root@node105 ~]# scp /etc/krb5.conf root@node104.yinzhengjie.org.cn:/etc/krb5.conf
The authenticity of host 'node104.yinzhengjie.org.cn (172.30.1.104)' can't be established.
ECDSA key fingerprint is SHA256:/SRWAQkeBXH2OkEd35YTfmAKpmVzhsdFE7fyWWaKZ1U.
ECDSA key fingerprint is MD5::e5:8a:a2:ce:af::::::b1:8b:6c::d3.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added 'node104.yinzhengjie.org.cn,172.30.1.104' (ECDSA) to the list of known hosts.
root@node104.yinzhengjie.org.cn's password:
krb5.conf % .6KB/s :
[root@node105 ~]#
[root@node105 ~]# scp /etc/krb5.conf root@node104.yinzhengjie.org.cn:/etc/krb5.conf
Kerberos 错误消息请参考:https://docs.oracle.com/cd/E24847_01/html/819-7061/trouble-2.html。
三.Cloudera Manager平台上Kerberos的配置(在做此操作之前,请检查服务器时期是否正常)
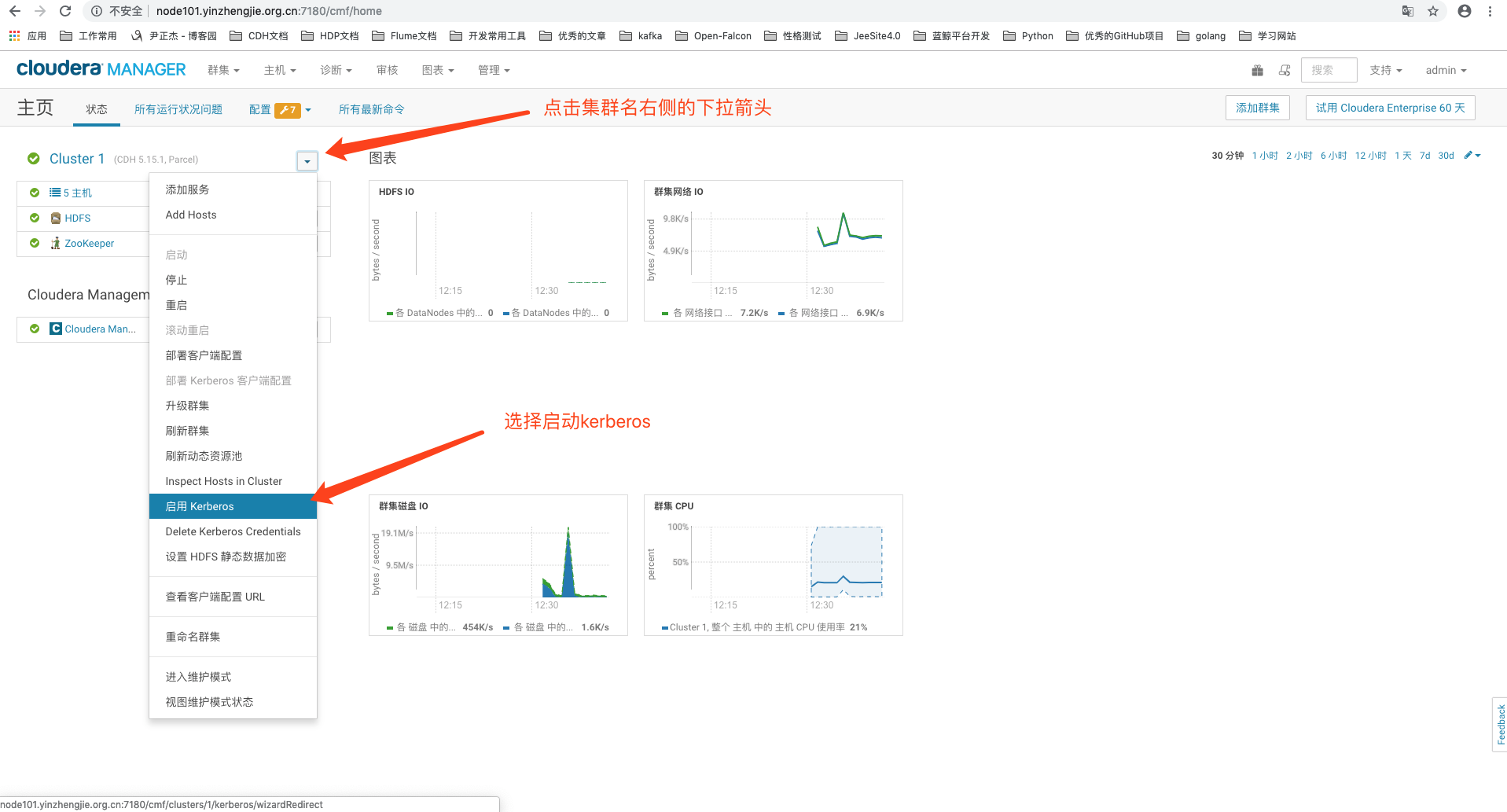
1>.启用keberos
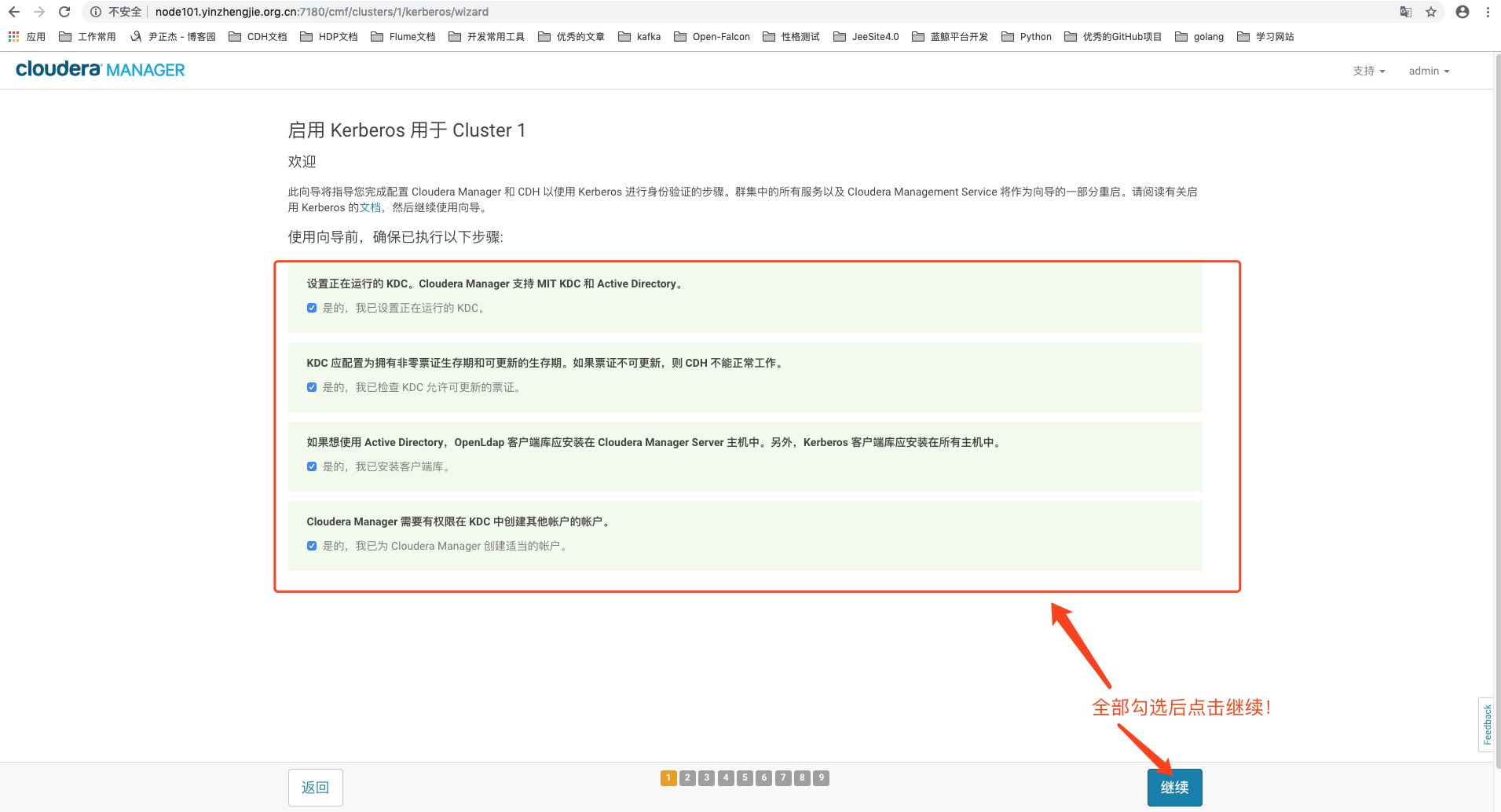
2>.确认四个要求都满足,打上对勾并点击继续按钮
3>.填写Kerberos的加密类型,RAELMS名称及服务地址
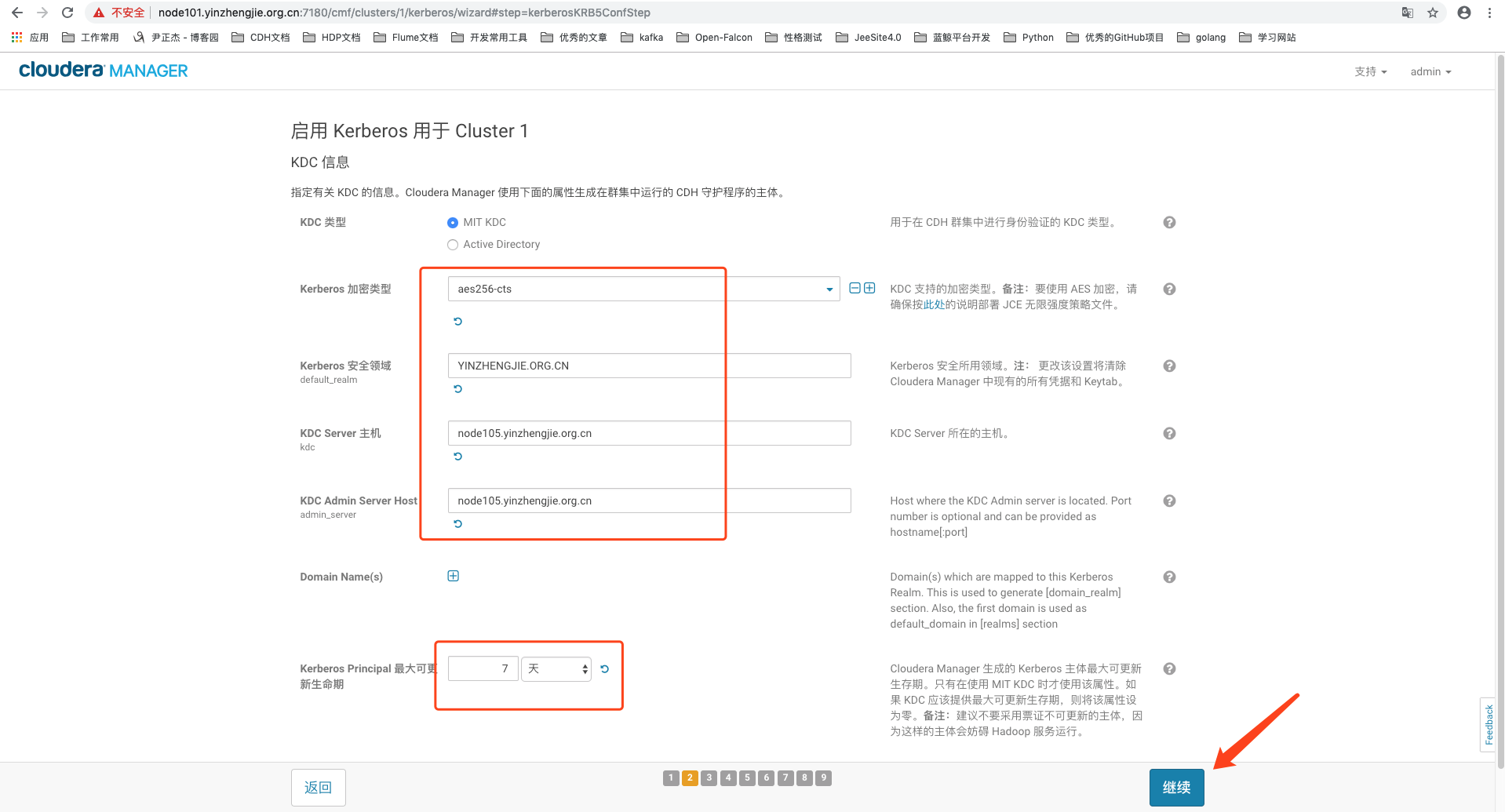
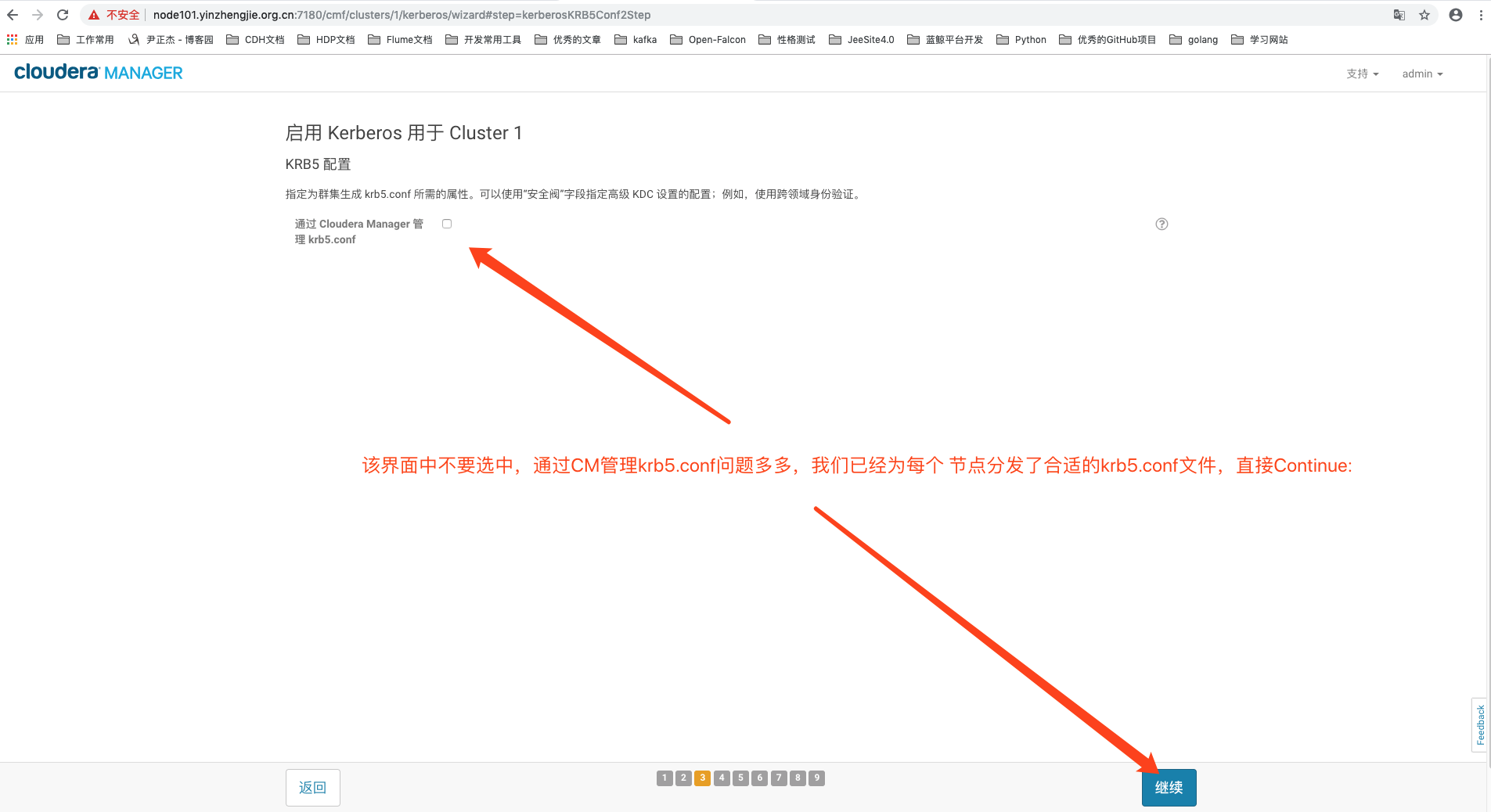
4>.不启用CM管理krb5.conf配置文件,因为我们之前已经手动分发了合适的krb5.conf
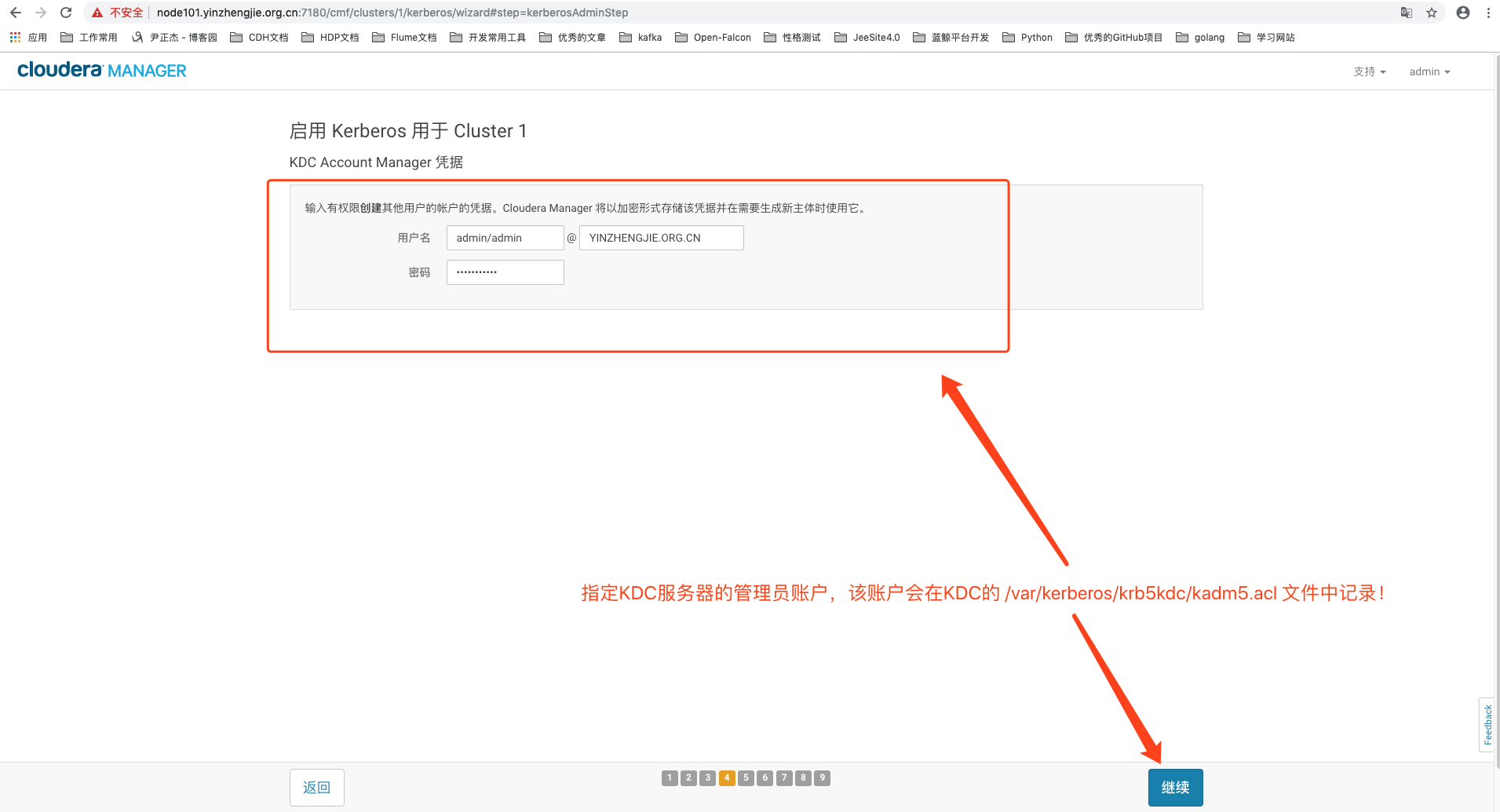
5>.设置admin的账号(默认在KDC服务器中的 :/var/kerberos/krb5kdc/kadm5.acl 中指定)
6>.如下图所示,等待启用Kerberos完成
7>.配置Principals
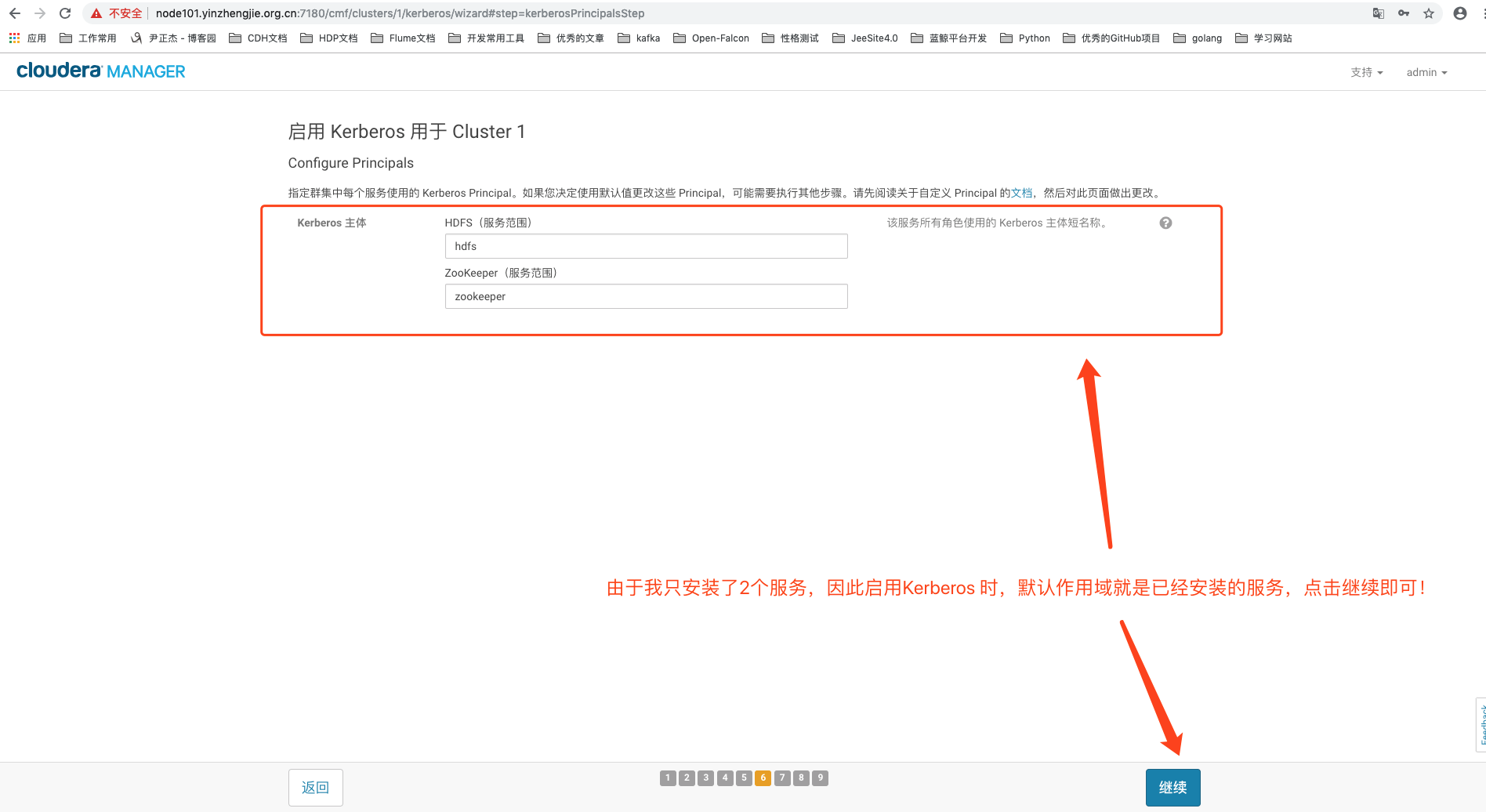
8>.勾选重启集群的选项

9>.如下图所示,等待集群重启完成
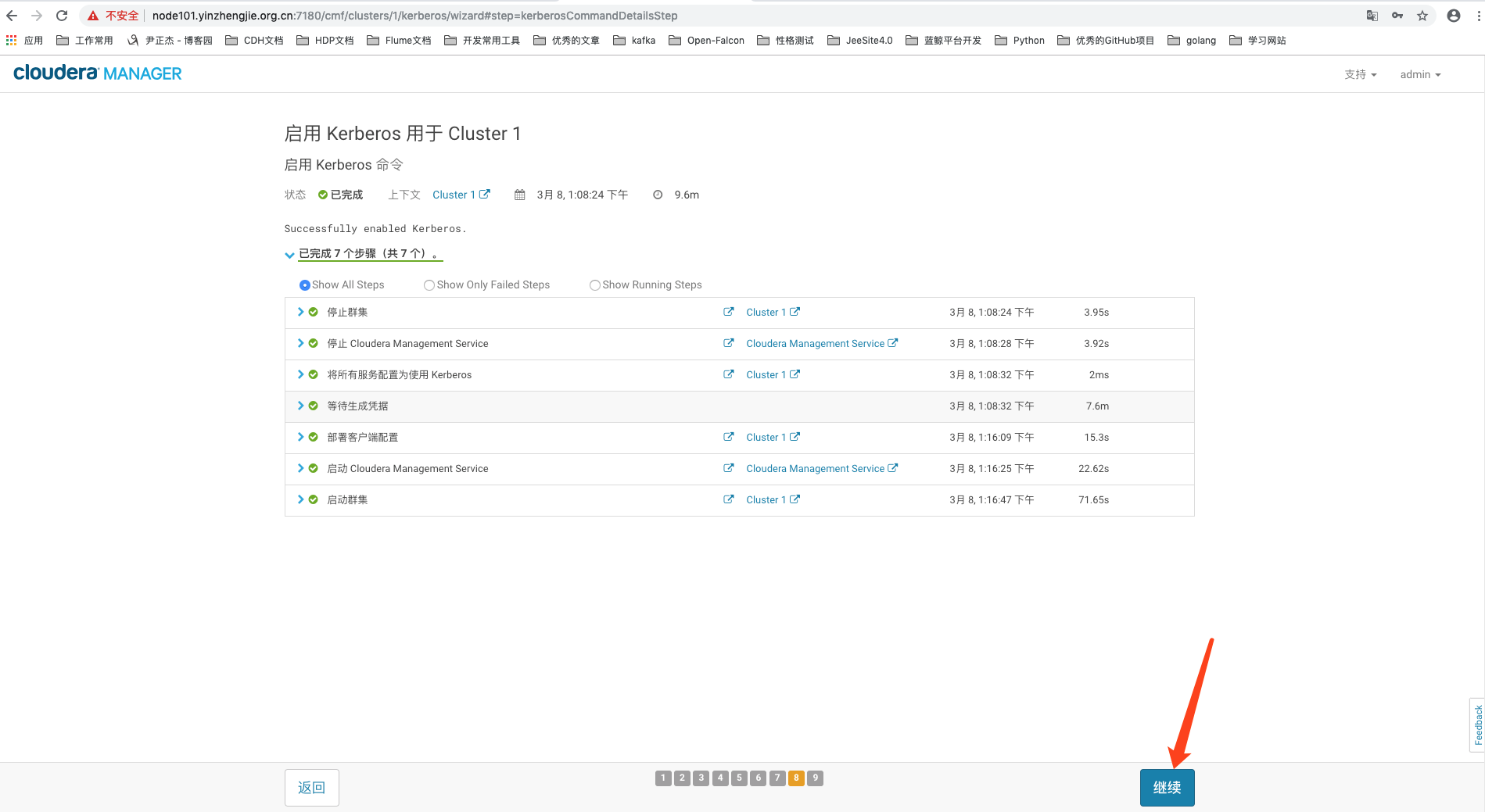
10>.Kerberos启动成功
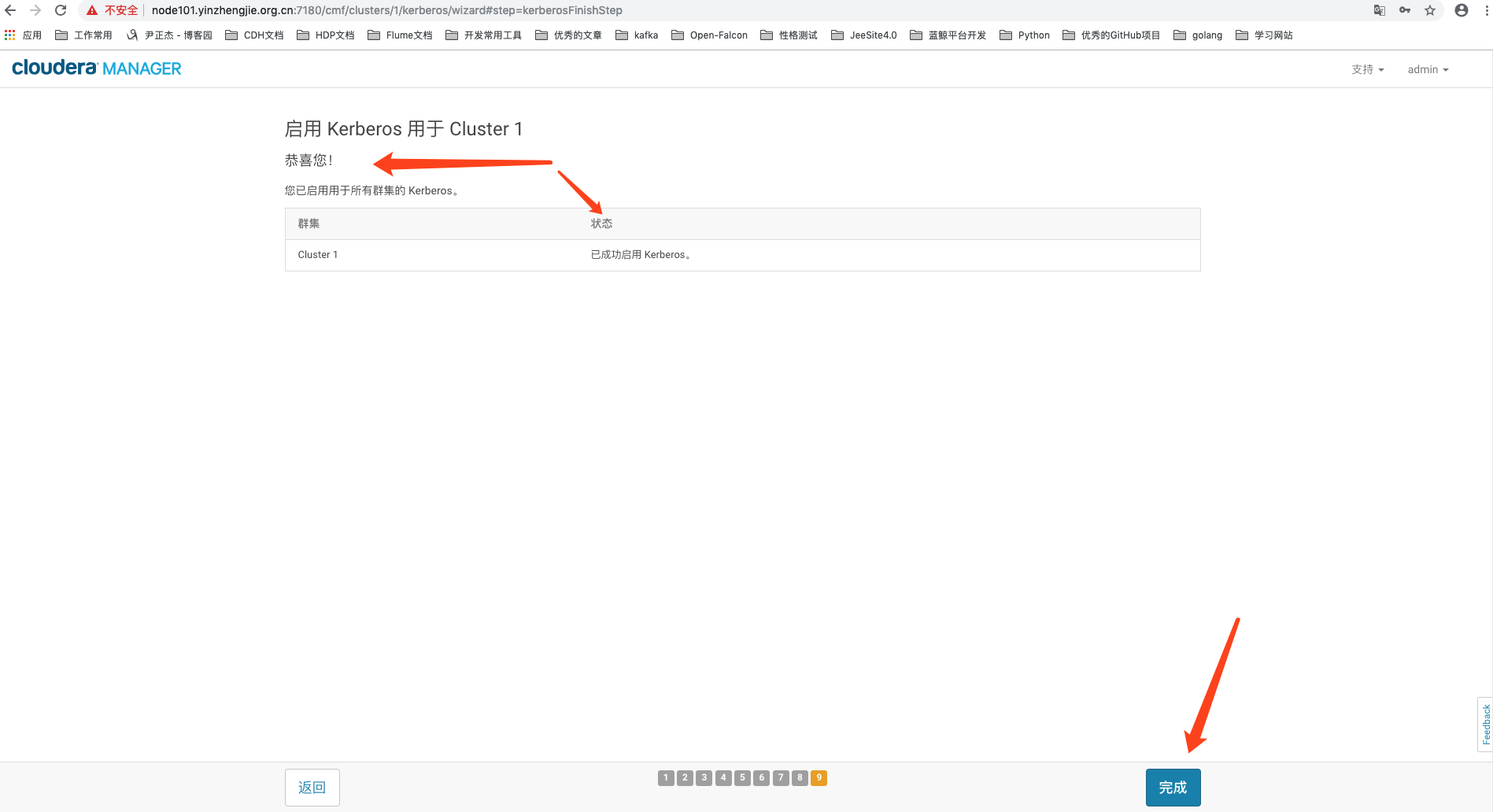
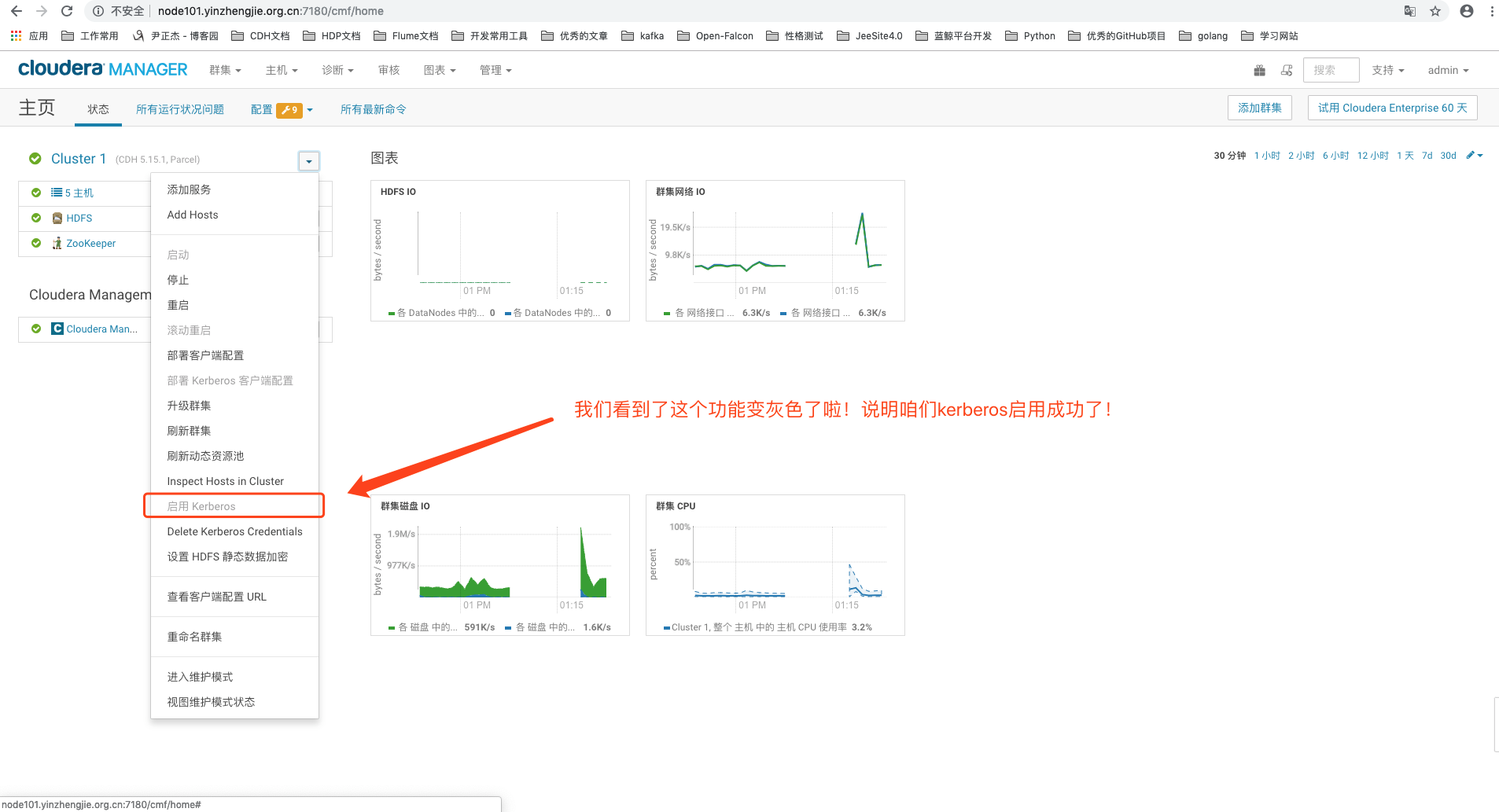
11>.Kerberos启动成功
CDH构建大数据平台-配置集群的Kerberos认证安全的更多相关文章
- 大数据 -- Cloudera Manager(简称CM)+CDH构建大数据平台
一.Cloudera Manager介绍 Cloudera Manager(简称CM)是Cloudera公司开发的一款大数据集群安装部署利器,这款利器具有集群自动化安装.中心化管理.集群监控.报警等功 ...
- CDH构建大数据平台-使用自建的镜像地址安装Cloudera Manager
CDH构建大数据平台-使用自建的镜像地址安装Cloudera Manager 作者:尹正杰 版权声明:原创作品,谢绝转载!否则将追究法律责任. 一.搭建CM私有仓库 详情请参考我的笔记: http ...
- CDH构建大数据平台-Kerberos高可用部署【完结篇】
CDH构建大数据平台-Kerberos高可用部署[完结篇] 作者:尹正杰 版权声明:原创作品,谢绝转载!否则将追究法律责任. 一.安装Kerberos相关的软件包并同步配置文件 1>.实验环境 ...
- 大数据平台Hadoop集群搭建
一.概念 Hadoop是由java语言编写的,在分布式服务器集群上存储海量数据并运行分布式分析应用的开源框架,其核心部件是HDFS与MapReduce.HDFS是一个分布式文件系统,类似mogilef ...
- 大数据测试之hadoop集群配置和测试
大数据测试之hadoop集群配置和测试 一.准备(所有节点都需要做):系统:Ubuntu12.04java版本:JDK1.7SSH(ubuntu自带)三台在同一ip段的机器,设置为静态IP机器分配 ...
- 大数据高可用集群环境安装与配置(07)——安装HBase高可用集群
1. 下载安装包 登录官网获取HBase安装包下载地址 https://hbase.apache.org/downloads.html 2. 执行命令下载并安装 cd /usr/local/src/ ...
- 大数据中Hadoop集群搭建与配置
前提环境是之前搭建的4台Linux虚拟机,详情参见 Linux集群搭建 该环境对应4台服务器,192.168.1.60.61.62.63,其中60为主机,其余为从机 软件版本选择: Java:JDK1 ...
- 大数据高可用集群环境安装与配置(06)——安装Hadoop高可用集群
下载Hadoop安装包 登录 https://mirrors.tuna.tsinghua.edu.cn/apache/hadoop/common/ 镜像站,找到我们要安装的版本,点击进去复制下载链接 ...
- 大数据中HBase集群搭建与配置
hbase是分布式列式存储数据库,前提条件是需要搭建hadoop集群,需要Zookeeper集群提供znode锁机制,hadoop集群已经搭建,参考 Hadoop集群搭建 ,该文主要介绍Zookeep ...
随机推荐
- 如何将Chrome本地安装的扩展应用导出到本地
有时由于种种原因,我们不能直接使用Chrome web store进行Chrome扩展应用的安装,这时可以让一位已经安装了某Chrome扩展应用的朋友将他的应用导出到本地成为.crx文件,然后发给你, ...
- shell取消键盘回显
使用下面这个命令取消回显 stty -echo 使用下面这个命令打开回显 stty echo
- APP中的第三方“支付”功能测试建议
目前市场上APP中带有支付功能的产品有非常多,那么APP中带有第三方支付功能的产品在这一模块该如何测试才尽可能的确保测试完整性. 正常流程: 正常使用支付宝.微信.银行卡(目前使用最多的第三方支付方式 ...
- Java字节码文件结构剖析
今天起开启JVM的新的知识学习篇章----Java的字节码,那学习Java字节码有啥用呢?我们知道Java是跨平台的一门语言,编写一次到处运行,而支撑着这个特性的根基为两点:JVM和.class字节码 ...
- BCB 中 Application->CreateForm 和 New 的一个区别
Application->Create 和 NEW 的一个区别 最近写windows服务的时候,恰巧碰到一个问题.我建立了一个DataModal,然后在Datamodal的OnCreate 事件 ...
- MySQL-进阶7-子查询 - select后/where后/from后/ []where后/having后] / exists后面 的相关子查询
/*SQL-进阶7-子查询 含义:出现在其他语句中的select 语句,称为子查询或内查询 外部的查询语句,称为主查询 或者 外查询 分类1:按子查询出现的位置———— select 后面:仅仅支持标 ...
- nginx 重发机制导致的重复扣款问题
问题: nginx 重发机制导制重复提交(客户还款,被扣俩笔款,前端调用一次,后端执行2次) proxy_next_upstream 语法: proxy_next_upstream error ...
- oracle 12c 安装补丁报错
环境: centos 7.5 oracle 12.2.0.1 报错: 执行一下报错: 更新dba_registry_sqlpatch $ORACLE_HOME/OPatch/datapatch -ve ...
- K3CLOUD 常用数据表
二.K3 Cloud 开发插件<K3 Cloud 常用数据表整理>一.数据库查询常用表 按 Ctrl+C 复制代码 按 Ctrl+C 复制代码 通过表T_META_OBJECTTYPE的F ...
- easyui-filebox上传文件或图片时选择相同文件无法触发change事件的问题
其实很简单,当选择完一个文件之后,会将文件名存放在input中的value值中,当下一次onChange之后,比对玩发现,value值没有发生变化,所以不能触发. 所以,只需要下次将value值清空就 ...
