Kali linux 2016.2(Rolling)中metasploit的主机探测
不多说,直接上干货!

1、活跃主机扫描



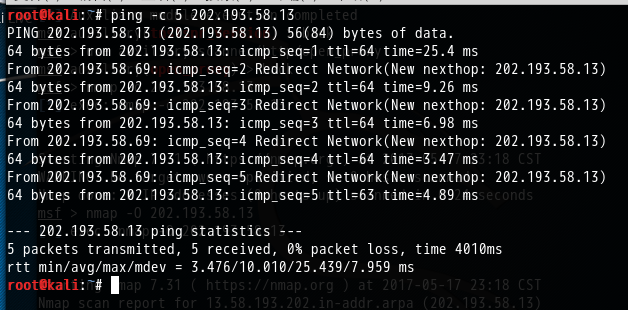
root@kali:~# ping -c 202.193.58.13
PING 202.193.58.13 (202.193.58.13) () bytes of data.
bytes from 202.193.58.13: icmp_seq= ttl= time=25.4 ms
From 202.193.58.69: icmp_seq= Redirect Network(New nexthop: 202.193.58.13)
bytes from 202.193.58.13: icmp_seq= ttl= time=9.26 ms
From 202.193.58.69: icmp_seq= Redirect Network(New nexthop: 202.193.58.13)
bytes from 202.193.58.13: icmp_seq= ttl= time=6.98 ms
From 202.193.58.69: icmp_seq= Redirect Network(New nexthop: 202.193.58.13)
bytes from 202.193.58.13: icmp_seq= ttl= time=3.47 ms
From 202.193.58.69: icmp_seq= Redirect Network(New nexthop: 202.193.58.13)
bytes from 202.193.58.13: icmp_seq= ttl= time=4.89 ms --- 202.193.58.13 ping statistics ---
packets transmitted, received, % packet loss, time 4010ms
rtt min/avg/max/mdev = 3.476/10.010/25.439/7.959 ms
root@kali:~#
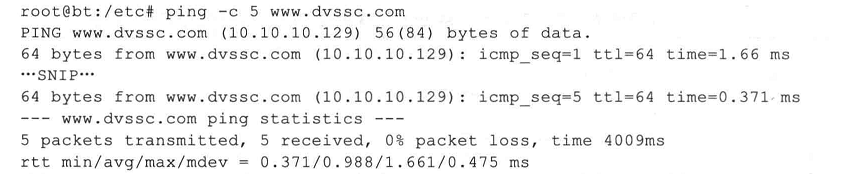
当然,你也用下面这个
2、Metasploit的主机发现模块

arp_sweep模块便是一个ARP扫描器,如下所示。
arp_sweep使用ARP请求美剧本地局域网中的所有活跃主机
udp_sweep通过发送UDP数据包探查制定主机是否活跃,兵发现主机上的UDP服务
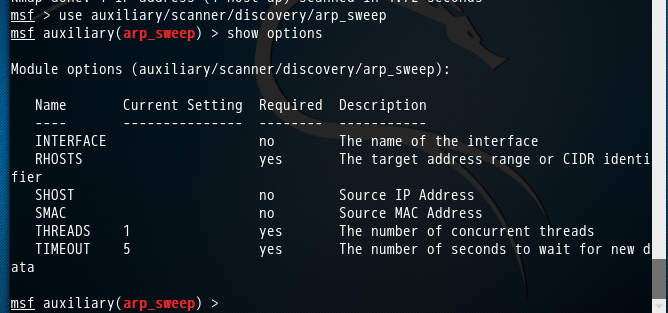
root@kali:~# msfconsole
....
msf > use auxiliary/scanner/discovery/arp_sweep
msf auxiliary(arp_sweep) > show options Module options (auxiliary/scanner/discovery/arp_sweep): Name Current Setting Required Description
---- --------------- -------- -----------
INTERFACE no The name of the interface
RHOSTS yes The target address range or CIDR identifier
SHOST no Source IP Address
SMAC no Source MAC Address
THREADS yes The number of concurrent threads
TIMEOUT yes The number of seconds to wait for new data msf auxiliary(arp_sweep) >

设置好RHOSTS和THREADS参数后,输入run命令启动扫描器,如下图所示。

msf auxiliary(arp_sweep) > set RHOSTS 202.193.58.13/
RHOSTS => 202.193.58.13/
msf auxiliary(arp_sweep) > set THREADS
THREADS =>
msf auxiliary(arp_sweep) > run [*] 202.193.58.7 appears to be up (UNKNOWN).
[*] 202.193.58.7 appears to be up (UNKNOWN).
[*] 202.193.58.9 appears to be up (UNKNOWN).
[*] 202.193.58.9 appears to be up (UNKNOWN).
[*] 202.193.58.11 appears to be up (UNKNOWN).
[*] 202.193.58.12 appears to be up (UNKNOWN).
[*] 202.193.58.13 appears to be up (UNKNOWN).
[*] 202.193.58.13 appears to be up (ASUSTek COMPUTER INC.).
[*] 202.193.58.14 appears to be up (UNKNOWN).
[*] 202.193.58.19 appears to be up (UNKNOWN).
[*] 202.193.58.20 appears to be up (ELITEGROUP COMPUTER SYSTEMS CO., LTD.).
[*] 202.193.58.23 appears to be up (UNKNOWN).
[*] 202.193.58.26 appears to be up (COMPAL INFORMATION(KUNSHAN)CO.,LTD).
[*] 202.193.58.33 appears to be up (UNKNOWN).
[*] 202.193.58.47 appears to be up (TP-LINK TECHNOLOGIES CO., LTD.).
[*] 202.193.58.48 appears to be up (UNKNOWN).
[*] 202.193.58.53 appears to be up (UNKNOWN).
[*] 202.193.58.55 appears to be up (UNKNOWN).
[*] 202.193.58.58 appears to be up (UNKNOWN).
[*] 202.193.58.60 appears to be up (D-Link International).
[*] 202.193.58.7 appears to be up (UNKNOWN).
[*] 202.193.58.69 appears to be up (COMPAL INFORMATION (KUNSHAN) CO., LTD).
[*] 202.193.58.73 appears to be up (ELITEGROUP COMPUTER SYSTEMS CO., LTD.).
[*] 202.193.58.76 appears to be up (UNKNOWN).
[*] 202.193.58.82 appears to be up (UNKNOWN).
[*] 202.193.58.83 appears to be up (Armorlink shanghai Co. Ltd).
[*] 202.193.58.85 appears to be up (QUANTA COMPUTER INC.).
[*] 202.193.58.7 appears to be up (UNKNOWN).
[*] 202.193.58.98 appears to be up (Advantech Technology (CHINA) Co., Ltd.).
[*] 202.193.59.254 appears to be up (FUJIAN STAR-NET COMMUNICATION CO.,LTD).
[*] 202.193.58.109 appears to be up (UNKNOWN).
[*] 202.193.58.111 appears to be up (UNKNOWN).
[*] 202.193.58.7 appears to be up (UNKNOWN).
[*] 202.193.58.148 appears to be up (UNKNOWN).
[*] 202.193.58.155 appears to be up (Jetway Information Co., Ltd.).
[*] 202.193.58.13 appears to be up (UNKNOWN).
[*] 202.193.58.162 appears to be up (UNKNOWN).
[*] 202.193.58.165 appears to be up (Tenda Technology Co., Ltd.).
[*] 202.193.58.171 appears to be up (UNKNOWN).
[*] 202.193.58.179 appears to be up (UNKNOWN).
[*] 202.193.58.180 appears to be up (Dell Inc).
[*] 202.193.58.13 appears to be up (UNKNOWN).
[*] 202.193.59.254 appears to be up (FUJIAN STAR-NET COMMUNICATION CO.,LTD).
[*] 202.193.58.197 appears to be up (UNKNOWN).
[*] 202.193.58.208 appears to be up (UNKNOWN).
[*] 202.193.58.215 appears to be up (Universal Global Scientific Industrial Co., Ltd.).
[*] 202.193.58.13 appears to be up (UNKNOWN).
[*] 202.193.58.220 appears to be up (UNKNOWN).
[*] 202.193.58.224 appears to be up (UNKNOWN).
[*] 202.193.58.230 appears to be up (ELITEGROUP COMPUTER SYSTEMS CO., LTD.).
[*] 202.193.58.231 appears to be up (UNKNOWN).
[*] 202.193.58.236 appears to be up (G-PRO COMPUTER).
[*] 202.193.58.242 appears to be up (UNKNOWN).
[*] Scanned of hosts (% complete)
[*] Auxiliary module execution completed
msf auxiliary(arp_sweep) >
当然,大家可以用下面的

Kali linux 2016.2(Rolling)中metasploit的主机探测的更多相关文章
- MetaSploit攻击实例讲解------社会工程学set攻击(kali linux 2016.2(rolling))(详细)
不多说,直接上干货! 首先,如果你是用的BT5,则set的配置文件是在 /pentest/exploits/set/set_config下. APACHE_SERVER=ONSELF_SIGNED_A ...
- MetaSploit攻击实例讲解------Metasploit自动化攻击(包括kali linux 2016.2(rolling) 和 BT5)
不多说,直接上干货! 前期博客 Kali linux 2016.2(Rolling)里Metasploit连接(包括默认和自定义)的PostgreSQL数据库 Kali linux 2016.2(Ro ...
- MetaSploit攻击实例讲解------终端下PostgreSQL数据库的使用(包括kali linux 2016.2(rolling) 和 BT5)
不多说,直接上干货! 配置msf连接postgresql数据库 我这里是使用kali linux 2016.2(rolling) 用过的博友们都知道,已经预安装好了PostgreSQL. 1. p ...
- MetaSploit攻击实例讲解------工具Meterpreter常用功能介绍(kali linux 2016.2(rolling))(详细)
不多说,直接上干货! 说在前面的话 注意啦:Meterpreter的命令非常之多,本篇博客下面给出了所有,大家可以去看看.给出了详细的中文 由于篇幅原因,我只使用如下较常用的命令. 这篇博客,利用下面 ...
- MetaSploit攻击实例讲解------攻击445端口漏洞(kali linux 2016.2(rolling))(详细)
不多说,直接上干货! 大家,相信最近的这个事件,对于445端口已经是非常的小心了.勒索病毒 445端口是一个毁誉参半的端口,有了它我们可以在局域网中轻松访问各种共享文件夹或共享打印机,但也正是因为有了 ...
- Kali linux 2016.2 的 plyload模块之meterpreter plyload详解
不多说,直接上干货! 前期博客 Kali linux 2016.2(Rolling)中的payloads模块详解 当利用成功后尝试运行一个进程,它将在系统进程列表里显示,即使在木马中尝试执行系统命令, ...
- Kali linux 2016.2(Rolling)中的Metasploit如何更新与目录结构初步认识
如何更新MSF 1.Windows平台 方法1: 运行msfupdate.bat 在msfconsole里执行命令svn update 或者 方法2: 2.unix/linux平台 方法1: 运行m ...
- Kali linux 2016.2(Rolling)中的payloads模块详解
不多说,直接上干货! 前期博客 Kali linux 2016.2(Rolling)中的Exploits模块详解 payloads模块,也就是shellcode,就是在漏洞利用成功后所要做的事情.在M ...
- Kali linux 2016.2(Rolling)里Metasploit连接(包括默认和自定义)的PostgreSQL数据库之后的切换到指定的工作空间
不多说,直接上干货! 为什么要这么做? 答: 方便我们将扫描不同的目标或目标的不同段,进行归类.为了更好的后续工作! 前期博客 Kali linux 2016.2(Rolling)里Metasploi ...
随机推荐
- java语言中的多态概述
多态:一个对象相应着不同类型 多态在代码中的体现:父类或接口的引用指向其子类对象. 多态的优点: 提高了代码的扩展性,前期定义的代码能够使用后期的内容. 多态的弊端: 前期定义的内容不能使用后期子类中 ...
- JavaScript 没有函数重载&Arguments对象
对于学过Java的人来说.函数重载并非一个陌生的概念,可是javaScript中有函数重载么...接下来我们就进行測试 <script type="text/javascript&qu ...
- node16---cookie session
03.js var express = require("express"); var app = express(); var db = require("./mode ...
- 为什么不建议用table进行布局
本文部分内容转载自:http://www.html5tricks.com/why-not-table-layout.html 刚刚接触html的时候,利用table进行页面布局是比较容易的.但是,在实 ...
- Swift 4.0:访问级别(访问控制)
基础篇 注: 下文中所提及的类和类型为Class, Enum和Struct Swift中的访问级别有以下五种: open: 公开权限, 最高的权限, 可以被其他模块访问, 继承及复写. public: ...
- 优动漫PAINT绘制紫阳花教程
紫阳花是插画.漫画很常见的绘画画材.这个教程非常好懂.而且很方便就能绘制出漂亮的效果.因为这种花一个月内能变化三种颜色,故而人们赋予它的花语是善变.背叛. 教程是简单,呃.... 没有优动漫PAINT ...
- 一个简单的MyBatis项目(应用)
### 1. MYBATIS简介 MYBATIS是持久层框架,大大的简化了持久层开发. 当使用MYBATIS框架时,开发人员不必再编写繁琐的JDBC代码,只需要定义好每个功能对应的抽象方法与需要执 ...
- [USACO17DEC]Milk Measurement(平衡树)
题意 最初,农夫约翰的每头奶牛每天生产G加仑的牛奶 (1≤G≤109)(1≤G≤10^9)(1≤G≤109) .由于随着时间的推移,奶牛的产奶量可能会发生变化,农夫约翰决定定期对奶牛的产奶量进行测量, ...
- [HNOI2004]打砖块(敲砖块)
题目:codevs1257.洛谷P1437 题目大意:有一些砖块呈倒三角形状,每块砖敲掉后有一个分数.除第一行外,敲掉一块砖必须先把上面两块砖敲掉.现在你能敲m块砖,求能得到的最大分数. 解题思路:此 ...
- 紫书 习题 11-10 UVa 12264 (二分答案+最大流)
书上写的是UVa 12011, 实际上是 12264 参考了https://blog.csdn.net/xl2015190026/article/details/51902823 这道题就是求出一种最 ...
