German Collegiate Programming Contest 2015(第三场)
Divisions
David is a young boy and he loves numbers. Recently he learned how to divide two numbers.David divides the whole day. He is happy if the result of the division is an integer, but he is not very amused if this is not the case. After quite a while he decided to use only a single dividend each day.
The parents of David are very careful and they would like to ensure that David experiences enough happiness. Therefore they decide which number David will use as the dividend for this day.
There is still a problem: The parents are not very good at math and don’t know how to calculatethe number of positive integral divisors for a given dividend N , which lead to an integral result.Now it’s up to you to help David’s parents.
Input
The single input line contains the single integer N , where N is chosen as a dividend (1≤N≤1018)
Output
Print the number of positive integral divisors of N that lead to an integral result of the division.
sample input 1
12
sample output 1
6
sample input 2
999999999999999989
sample output 2
2
sample input 3
100000007700000049
sample output 3
4
大数素因子分解
#include <iostream>
#include <algorithm>
#include <cstring>
#include <cstdio>
#include <vector>
#include <queue>
#include <stack>
#include <cstdlib>
#include <iomanip>
#include <cmath>
#include <cassert>
#include <ctime>
#include <map>
#include <set>
using namespace std;
#pragma comment(linker, "/stck:1024000000,1024000000")
#define lowbit(x) (x&(-x))
#define max(x,y) (x>=y?x:y)
#define min(x,y) (x<=y?x:y)
#define MAX 100000000000000000
#define MOD 1000000007
#define pi acos(-1.0)
#define ei exp(1)
#define PI 3.1415926535897932384626433832
#define ios() ios::sync_with_stdio(true)
#define INF 0x3f3f3f3f
#define mem(a) (memset(a,0,sizeof(a)))
typedef long long ll;
const int s=;
char ch[];
ll mult_mod(ll a,ll b,ll c)
{
a%=c;
b%=c;
ll ret=;
ll tmp=a;
while(b)
{
if(b&){
ret+=tmp;
if(ret>c) ret-=c;
}
tmp<<=;
if(tmp>c) tmp-=c;
b>>=;
}
return ret;
}
ll pow_mod(ll a,ll n,ll mod)
{
ll ans=;
ll tmp=a%mod;
while(n)
{
if(n&) ans=mult_mod(ans,tmp,mod);
tmp=mult_mod(tmp,tmp,mod);
n>>=;
}
return ans;
}
bool check(ll a,ll n,ll x,ll t)
{
ll ret=pow_mod(a,x,n);
ll last=ret;
for(int i=;i<=t;i++)
{
ret=mult_mod(ret,ret,n);
if(ret== && last!= && last!=n-) return true;
last=ret;
}
if(ret!=) return true;
else return false;
}
bool miller_pabin(ll n)
{
if(n<) return false;
if(n==) return true;
if((n&)==) return false;
ll x=n-;
ll t=;
while((x&)==) {x>>=;t++;}
srand(time(NULL));
for(int i=;i<s;i++){
ll a=rand()%(n-)+;
if(check(a,n,x,t)) return false;
}
return true;
}
ll factor[];
int tol=;
ll gcd(ll a,ll b)
{
ll t;
while(b)
{
t=a;
a=b;
b=t%b;
}
if(a>=) return a;
else return -a;
}
ll pollard_rho(ll x,ll c)
{
ll i=,k=;
srand(time(NULL));
ll x0=rand()%(x-)+;
ll y=x0;
while()
{
i++;
x0=(mult_mod(x0,x0,x)+c)%x;
ll d=gcd(y-x0,x);
if(d!= && d!=x) return d;
if(y==x0) return x;
if(i==k){y=x0;k+=k;}
}
}
void findfac(ll n,ll k)
{
if(n==) return ;
if(miller_pabin(n))
{
factor[tol++]=n;
return ;
}
ll p=n;
ll c=k;
while(p>=n) p=pollard_rho(p,c--);
findfac(p,k);
findfac(n/p,k);
}
int main()
{
ll n;
scanf("%lld",&n);
if(miller_pabin(n)) printf("2\n");
else
{
findfac(n,);
ll ans=;
for(int i=;i<tol;i++)
{
//printf("%lld ",factor[i]);
ll pos=;
while(n> && (n%factor[i]==))
{
pos++;
n/=factor[i];
}
printf("%lld %lld\n",factor[i],pos);
if(pos) ans*=(pos+);
}
printf("%lld\n",ans);
}
return ;
}
Extreme Sort
John likes sorting algorithms very much. He has studied quick sort, merge sort, radix sort, and many more.
A
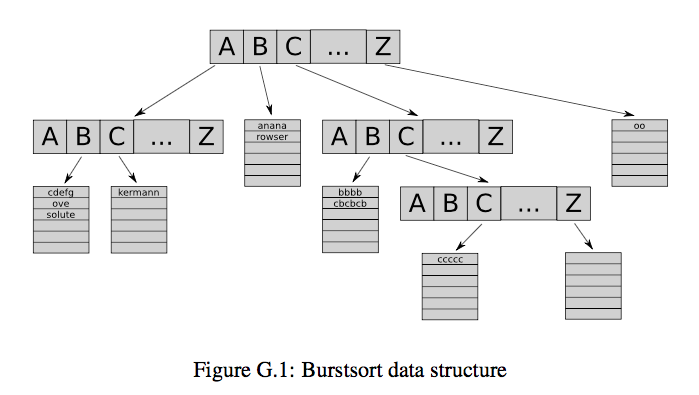
long time ago he has written a lock-free parallel string sorting
program. It was a combination of burst sort and multi-key quick sort. To
implement burst sort you need to build a tree of buckets.For each input
string you walk through the tree and insert part of the string into the
right bucket.When a bucket fills up, it "bursts" and becomes a new
subtree (with new buckets).
Well,
enough about the past. Today John is playing with sorting algorithms
again. This time it’s numbers. He has an idea for a new algorithm,
“extreme sort”. It’s extremely fast, performance levels are OVER
NINETHOUSAND. Before he tells anyone any details, he wants to make sure
that it works correctly.
Your task is to help him and verify that the so-called extreme property holds after the first phase of the algorithm. The extreme property is defined as min (xi,j ) ≥ 0, where

Input
The first line contains a single integer N (1 ≤ N ≤ 1024). The second line contains N integers a1 a2 ... aN (1≤ai ≤1024).
Output
Print one line of output containing “yes” if the extreme property holds for the given input, “no”otherwise.
样例输入1
2
1 2
样例输出1
yes
样例输入2
4
2 1 3 4
样例输出2
no
只要判断是否严格递增就可以了
#include <iostream>
using namespace std;
#include <cstdio>
typedef unsigned long long ull;
typedef long long ll;
int main()
{
int front=,last,ok=,n;
scanf("%d",&n);
for(int i=;i<=n;i++)
{
scanf("%d",&last);
if(last<front) ok=;
front=last;
}
puts(ok?"no":"yes");
return ;
}
Legacy Code
Once again you lost days refactoring code, which never runs in the first place. Enough is enough– your time is better spent writing a tool that finds unused code!
Your software is divided into packages and executables. A package is a collection of methods. Executables are packages defining among other methods exactly one method with namePROGRAM. This method is executed on the start of the corresponding executable. Ordinary packages have no method named PROGRAM.
Each method is uniquely identified by the combination of package and method names. E.g.the method with the identifier SuperGame::PROGRAM would be the main method of the executable SuperGame.
For
every method in your software you are given a list of methods directly
invoking it. Thus you can easily identify methods, that are never called
from any method. However, your task is more challenging: you have to
find unused methods. These are methods that are never reached by the
control flow of any executable in your software.
Input
The first line of the input contains an integer N, the number of methods in your software(1≤N ≤400).
Each method is described by two lines, totaling in 2 · N lines. The first line consists of the unique identifier of the method and ki, the number of methods directly invoking this one (0 ≤ ki ≤ N).The second line consists of a set of ki identifiers of these calling methods or is empty if there are no such methods, i.e. ki = 0.
Method identifiers consist of a package name followed by two colons and a method name like Packagename::Methodname. Both strings, the package and the method name, each consist of up to 20 lowercase, uppercase characters or digits (a-z, A-Z, 0-9).
There will be exactly N different method identifiers mentioned in the input.
Output
A line containing the number of unused methods in your software.
样例输入1
2
SuperGame::PROGRAM 0
HelpPackage::HelpFunction 2
HelpPackage::HelpFunction SuperGame::PROGRAM
样例输出1
0
样例输入2
2
Loop::CallA 1
Loop::CallB
Loop::CallB 1
Loop::CallA
样例输出2
2
看懂英文就可以过,可以本身救赎尚可执行文件或者间接可执行
#include <iostream>
#include <algorithm>
#include <cstring>
#include <cstdio>
#include <vector>
#include <queue>
#include <stack>
#include <cstdlib>
#include <iomanip>
#include <cmath>
#include <cassert>
#include <ctime>
#include <map>
#include <set>
using namespace std;
#pragma comment(linker, "/stck:1024000000,1024000000")
#pragma GCC diagnostic error "-std=c++11"
#define lowbit(x) (x&(-x))
#define max(x,y) (x>=y?x:y)
#define min(x,y) (x<=y?x:y)
#define MAX 100000000000000000
#define MOD 1000
#define pi acos(-1.0)
#define ei exp(1)
#define PI 3.1415926535897932384626433832
#define ios() ios::sync_with_stdio(true)
#define INF 0x3f3f3f3f
#define mem(a) (memset(a,0,sizeof(a)))
typedef unsigned long long ull;
string s,ss[];
vector<int>v[];
map<string,int>m;
int n,k,pos=,vis[];
int getname(string s)
{
if(!m[s])
{
++pos;
m[s]=pos;
if(s.find("::PROGRAM")==s.size()- && s.size()>=) vis[pos]=;
}
return m[s];
}
void dfs(int now)
{
vis[now]=;
for(auto t:v[now])
if(!vis[t]) dfs(t);
}
int main()
{
scanf("%d",&n);
for(int i=;i<n;i++)
{
cin>>ss[i]>>k;
int f=getname(ss[i]);
for(int j=;j<k;j++)
{
cin>>s;
int l=getname(s);
v[l].push_back(f);
}
}
for(int i=;i<=pos;i++)
if(vis[i]) dfs(i);
int ans=;
for(int i=;i<n;i++)
if(vis[getname(ss[i])]) ans++;
printf("%d\n",n-ans);
return ;
}
/*
5
loop::PROGRAM 3
loop::xy loop::zy loop::wz
loop::xy 2
loop::zy loop::wz
loop::zy 1
loop::yz
loop::www 1
loop::wz
loop::wz 0
4
*/
Last night, I must have dropped my alarm clock. When the alarm went off in the morning, it showed 51:80 instead of 08:15. This made me realize that if you rotate a seven segment display like it is used in digital clocks by 180 degrees, some numbers still are numbers after turning them upside down.
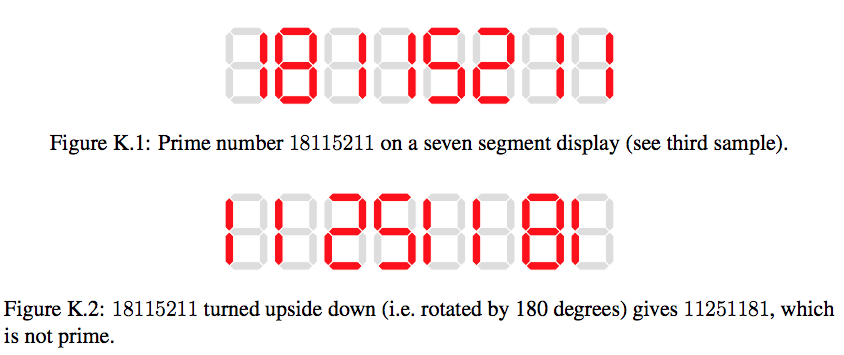
As you can see,
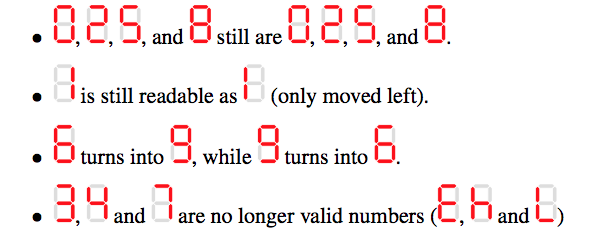
My
favourite numbers are primes, of course. Your job is to check whether a
number is a prime and still a prime when turned upside down.
Input
One line with the integer N in question (1 ≤ N ≤ 1016). N will not have leading zeros.
Output
Print one line of output containing “yes” if the number is a prime and still a prime if turned upside down, “no” otherwise.
样例输入1
151
样例输出1
yes
样例输入2
23
样例输出2
no
样例输入3
18115211
样例输出3
no
正反都是素数,要是包含3,4,7一定不是
#include <iostream>
#include <algorithm>
#include <cstring>
#include <cstdio>
#include <vector>
#include <queue>
#include <stack>
#include <cstdlib>
#include <iomanip>
#include <cmath>
#include <cassert>
#include <ctime>
#include <map>
#include <set>
using namespace std;
#pragma comment(linker, "/stck:1024000000,1024000000")
#define lowbit(x) (x&(-x))
#define max(x,y) (x>=y?x:y)
#define min(x,y) (x<=y?x:y)
#define MAX 100000000000000000
#define MOD 1000000007
#define pi acos(-1.0)
#define ei exp(1)
#define PI 3.1415926535897932384626433832
#define ios() ios::sync_with_stdio(true)
#define INF 0x3f3f3f3f
#define mem(a) (memset(a,0,sizeof(a)))
typedef long long ll;
const int s=;
char ch[];
ll mult_mod(ll a,ll b,ll c)
{
a%=c;
b%=c;
ll ret=;
ll tmp=a;
while(b)
{
if(b&){
ret+=tmp;
if(ret>c) ret-=c;
}
tmp<<=;
if(tmp>c) tmp-=c;
b>>=;
}
return ret;
}
ll pow_mod(ll a,ll n,ll mod)
{
ll ans=;
ll tmp=a%mod;
while(n)
{
if(n&) ans=mult_mod(ans,tmp,mod);
tmp=mult_mod(tmp,tmp,mod);
n>>=;
}
return ans;
}
bool check(ll a,ll n,ll x,ll t)
{
ll ret=pow_mod(a,x,n);
ll last=ret;
for(int i=;i<=t;i++)
{
ret=mult_mod(ret,ret,n);
if(ret== && last!= && last!=n-) return true;
last=ret;
}
if(ret!=) return true;
else return false;
}
bool miller_pabin(ll n)
{
if(n<) return false;
if(n==) return true;
if((n&)==) return false;
ll x=n-;
ll t=;
while((x&)==) {x>>=;t++;}
srand(time(NULL));
for(int i=;i<s;i++){
ll a=rand()%(n-)+;
if(check(a,n,x,t)) return false;
}
return true;
}
int main()
{
ll x=,y=;
scanf("%s",&ch);
int k=strlen(ch);
for(int i=;i<k;i++)
{
if(ch[i]=='' || ch[i]=='' || ch[i]=='')
{
printf("no\n");
return ;
}
x=x*+(ch[i]-'');
}
for(int i=k-;i>=;i--)
{
if(ch[i]=='' || ch[i]=='' || ch[i]=='' || ch[i]=='' || ch[i]=='') y=y*+(ch[i]-'');
else if(ch[i]=='') y=y*+;
else if(ch[i]=='') y=y*+;
}
bool okx=miller_pabin(x);
bool oky=miller_pabin(y);
if(okx && oky) printf("yes\n");
else printf("no\n");
return ;
}
Milling machines
A fab lab is an open, small-scale workshop where you can create or fabricate almost anything you want mostly by using computer controlled tools like a laser cutter or a 3D printer. The FAU fab lab recently got a CNC milling machine. Using the milling machine you can cut or remove material with different tools from the surface of a workpiece. It is controlled via a computer program.

I
sometimes wondered what happens if multiple different shaped workpieces
are sent through the same milling program. For simplification assume
that we have only two dimensional workpieces without holes. A milling
program consists of multiple steps; each step describes where the
milling machine has to remove material (using different tools) from the
top of the surface.
Input
The first line consists of two integers W and S, where W gives the number of workpieces andS the number of steps in the milling program (1 ≤ W, S ≤ 10410^4104). The next line consists of two integers X and Y , where X gives the width and Y gives the maximal possible height of workpieces (1 ≤ X, Y ≤ 100).
Then follow W lines, each describing one workpiece. Each workpiece description consists of X non-negative integers specifying the surface height in that column.
Then follow S lines, each describing one milling step of the milling program. Each milling step description consists of X non-negative integers si (0 ≤ si ≤ Y ) specifying the amount of surface to cut off in each column (relative to the height of the milling area, i.e. Y , not relative to the top of the workpiece). See Fig. I.1 for details.
Output
For each workpiece, output one line containing X integers specifying the remaining surface heights (in the same order as in the input).
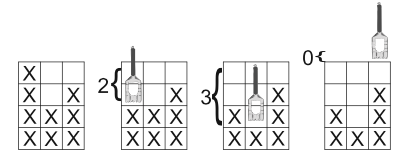
Figure
I.1: Second workpiece in first sample: initial workpiece followed by
milling in each column – the value in the milling program determines the
vertical position of the cutter head.
样例输入1
2 1
3 4
4 4 4
4 2 3
2 3 0
样例输出1
2 1 4
2 1 3
样例输入2
1 3
10 100
11 22 33 44 55 66 77 88 99 100
1 100 1 100 1 100 1 100 1 100
58 58 58 58 58 58 58 58 58 58
42 42 42 42 42 42 42 42 66 42
样例输出2
11 0 33 0 42 0 42 0 34 0
也是比较水的一道题
#include <iostream>
#include <cstdio>
using namespace std;
int a[][];
int b[],w,s,x,y;
typedef long long ll;
int main()
{
scanf("%d%d%d%d",&w,&s,&x,&y);
for(int i=;i<w;i++)
for(int j=;j<x;j++)
scanf("%d",&a[i][j]);
int ans;
for(int i=;i<s;i++)
for(int j=;j<x;j++)
{
scanf("%d",&ans);
b[j]=max(b[j],ans);
}
for(int i=;i<w;i++)
{
for(int j=;j<x;j++)
{
printf("%d", a[i][j]>y-b[j]?y-b[j]:a[i][j]);
if(j!=x-) printf(" ");
}
if(i!=w-) printf("\n");
}
return ;
}
Bounty Hunter II
Spike the bounty hunter is tracking another criminal through space. Luckily for him hyperspace travel has made the task of visiting several planets a lot easier. Each planet has a number of Astral Gates; each gate connects with a gate on another planet. These hyperspace connections are, for obvious safety reasons, one-way only with one gate being the entry point and the other gate being the exit point from hyperspace. Furthermore, the network of hyperspace connections must be loop-free to prevent the Astral Gates from exploding, a tragic lesson learned in the gate accident of 2022 that destroyed most of the moon.
While looking at his star map Spike wonders how many friends he needs to conduct a search on every planet. Each planet should not be visited by more than one friend otherwise the criminal might get suspicious and flee before he can be captured. While each person can start at a planet of their choosing and travel along the hyperspace connections from planet to planet they are still bound by the limitations of hyperspace travel.
Input Format
The input begins with an integer NNN specifying the number of planets (0<N≤1000). The planets are numbered from 0 to N−1. The following N lines specify the hyperspace connections.
The i-th of those lines first contains the count of connections K (0≤K≤N−1) from planet iii followed by K integers specifying the destination planets.
Output Format
Output the minimum number of persons needed to visit every planet.
样例输入1
4
1 1
1 2
0
1 1
样例输出1
2
样例输入2
6
0
1 2
2 4 5
1 2
0
0
样例输出2
4
匈牙利匹配
#include <iostream>
#include <algorithm>
#include <cstring>
#include <cstdio>
#include <vector>
#include <queue>
#include <stack>
#include <cstdlib>
#include <iomanip>
#include <cmath>
#include <cassert>
#include <ctime>
#include <map>
#include <set>
using namespace std;
#pragma comment(linker, "/stck:1024000000,1024000000")
#pragma GCC diagnostic error "-std=c++11"
#define lowbit(x) (x&(-x))
#define max(x,y) (x>=y?x:y)
#define min(x,y) (x<=y?x:y)
#define MAX 100000000000000000
#define MOD 1000
#define pi acos(-1.0)
#define ei exp(1)
#define PI 3.1415926535897932384626433832
#define ios() ios::sync_with_stdio(true)
#define INF 0x3f3f3f3f
#define mem(a) (memset(a,0,sizeof(a)))
typedef unsigned long long ull;
typedef long long ll;
int n,k,x;
int vis[],pos[];
vector<int>v[];
int dfs(int now)
{
if(vis[now]) return ;
vis[now]=;
for(auto &t:v[now])
{
if(pos[t]==- || dfs(pos[t]))
{
pos[t]=now;
return ;
}
}
return ;
}
int solve()
{
int ans=;
memset(pos,-,sizeof(pos));
for(int i=;i<n;i++)
{
memset(vis,,sizeof(vis));
ans+=dfs(i);
}
return ans;
}
int main()
{
scanf("%d",&n);
for(int i=;i<n;i++)
{
scanf("%d",&k);
for(int j=;j<k;j++)
{
scanf("%d",&x);
v[i].push_back(x+n);
}
}
printf("%d\n",n-solve());
return ;
}
/*
5
3 2 3 4
1 2
0
0
0
*/
German Collegiate Programming Contest 2015(第三场)的更多相关文章
- German Collegiate Programming Contest 2015 计蒜课
// Change of Scenery 1 #include <iostream> #include <cstdio> #include <algorithm> ...
- 计蒜客 18492.Upside down primes-米勒拉宾判大素数 (German Collegiate Programming Contest 2015 ACM-ICPC Asia Training League 暑假第一阶段第三场 K)
K. Upside down primes 传送门 这个题就是把大数按字符串输进去,判断一下是不是素数,然后反转180度,先判断反转之后的东西是不是一个数,如果是的话,再把这个数判一下是不是素数,如果 ...
- 计蒜客 18487.Divisions-大数的所有因子个数-Miller_Rabin+Pollard_rho-超快的(大数质因解+因子个数求解公式) (German Collegiate Programming Contest 2015 ACM-ICPC Asia Training League 暑假第一阶段第三场 F)
这一场两个和大数有关的题目,都用到了米勒拉宾算法,有点东西,备忘一下. 题目传送门 F. Divisions 传送门 这个题是求一个数的所有因子个数,但是数据比较大,1e18,所以是大数的题目,正常的 ...
- 计蒜客 18488.Extreme Sort (German Collegiate Programming Contest 2015 ACM-ICPC Asia Training League 暑假第一阶段第三场 E)
E.Extreme Sort 传送门 代码: #include<iostream> #include<cstdio> #include<cstring> #incl ...
- German Collegiate Programming Contest 2015
// Legacy Code #include <iostream> #include <cstdio> #include <cstring> #include & ...
- Nordic Collegiate Programming Contest 2015(第七场)
A:Adjoin the Networks One day your boss explains to you that he has a bunch of computer networks tha ...
- 2015 German Collegiate Programming Contest (GCPC 15) + POI 10-T3(12/13)
$$2015\ German\ Collegiate\ Programming\ Contest\ (GCPC 15) + POI 10-T3$$ \(A.\ Journey\ to\ Greece\ ...
- (寒假GYM开黑)2018 German Collegiate Programming Contest (GCPC 18)
layout: post title: 2018 German Collegiate Programming Contest (GCPC 18) author: "luowentaoaa&q ...
- 2018 German Collegiate Programming Contest (GCPC 18)
2018 German Collegiate Programming Contest (GCPC 18) Attack on Alpha-Zet 建树,求lca 代码: #include <al ...
随机推荐
- C#帮助控件HelpProvider的使用
using System; using System.Collections.Generic; using System.ComponentModel; using System.Data; usin ...
- silverlight wpf Command提交时输入验证
silverlight 或WPF在MVVM模式中使用INotifyDataErrorInfo接口对输入进行验证时 控件lostFocus时会触发验证,但在提交动作(例如button的Command)时 ...
- iOS 系统地图实现及定位
1:加入库CoreLocation.framework,MApKit.framework; 2:@property (nonatomic, strong) CLLocationManager *loc ...
- bzoj5204: [CodePlus 2018 3 月赛]投票统计(离散化+暴力)
5204: [CodePlus 2018 3 月赛]投票统计 题目:传送门 题解: 谢谢niang老师的一道sui题 离散化之后直接搞啊(打完之后还错了...) 代码: #include<cst ...
- mysql裸文件备份XtraBackup (innobackupex)
结构如下: 热备分为逻辑备份和裸文件备份. 裸文件备份比逻辑备份在速度上更快一些,因为它在底层复制数据文件.世界上唯一一款开源的,能够对INNODB和XtrDB数据库进行热备的开源工具. 他的优点是备 ...
- 继续ubuntu和遇到的easybcd的坑
找了很多教程,反复斟酌https://www.zhihu.com/question/34611974 个人感觉前方还有大坑无数.unbuntu四个分区系列——65%根目录,25%home目录,交换分区 ...
- 51nod 1632 B君的连通
题目: 这题看起来难,其实这么多概率啥的都是唬人的.甚至连快速幂都不用就可以解. 解法: n个节点,n-1条边,期望会有一半的边被炸毁(因为总体概率就是50%). 即(n-1)/2条边被炸毁,这 ...
- CSS3———linear-gradient() 线性渐变
线性渐变linear-gradient() 遇到了这样的css样式 body { height: 100%; background-color: #ffffff; background-image: ...
- swift where 的作用
条件限定: 类型限定: 结构化查询模式. 用于结构体.记录字段.
- gcd的queue与group
queue相当于事件处理机制里的事件池:只是任务池: 线程作为事件处理的实施者,由线程池从任务池中获取任务进行调度派发: group相当与工作组,按照任务的相关性对任务进行组织.
