Text Prompted Remote Speaker Authentication : Joint Speech and Speaker Recognition/Verification System :: Major Project ::: Introduction
转载自:http://ganeshtiwaridotcomdotnp.blogspot.com/2010/12/text-prompted-remote-speaker.html
Biometrics is, in the simplest definition, something you are. It is a physical characteristic unique to each individual such as fingerprint, retina, iris, speech. Biometrics has a very useful application in security; it can be used to authenticate a person’s identity and control access to a restricted area, based on the premise that the set of these physical characteristics can be used to uniquely identify individuals.
Speech signal conveys two important types of information, the primarily the speech content and on the secondary level, the speaker identity. Speech recognizers aim to extract the lexical information from the speech signal independently of the speaker by reducing the inter-speaker variability. On the other hand, speaker recognition is concerned with extracting the identity of the person speaking the utterance. So both speech recognition and speaker recognition system is possible from same voice input.
Desired Output of the Combined System
Text Prompted Remote Speaker Authentication is a voice biometric system that authenticates a user before permitting the user to log into a system on the basis of the user’s input voice. It is a web application. Voice signal acquisition and feature extraction is done on the client. Training and Authentication task based on the voice feature obtained from client side is done on Server. The authentication task is based on text-prompted version of speaker recognition, which incorporates both speaker recognition and speech recognition. This joint implementation of speech and speaker recognition includes text-independent speaker recognition and speaker-independent speech recognition. Speaker Recognition verifies whether the speaker is claimed one or not while Speech Recognition verifies whether or not spoken word matches the prompted word.
The client side is realized in Adobe Flex whereas the server side is realized in Java. The communication between these two cross-platforms is made possible with the help of Blaze DS’s RPC remote object.
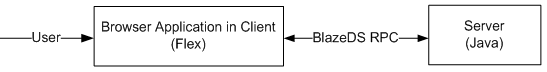
System Architecture
Mel Filter Cepstral Coefficient (MFCC) is used as feature for both speech and speaker recognition task. We also combined energy features and delta and delta-delta features of energy and MFCC. The feature extraction module is same for both speech and speaker recognition. And these recognition systems are implemented independent of each other.
For speaker recognition, GMM(Gaussian Mixture Model) parameters for registered users and a universal background model (UBM) were trained using Expectation Maximization algorithm. Log likelihood ratio between claimed speaker and UBM were compared against threshold to verify the user.
For speech recognition, Codebook is created by k-means clustering of the all feature vector from training speech data. Vector Quantization (VQ) is used to get discrete observation sequence from input feature vector by applying distance metric to Codebook. Left to Right Discrete HMM(Hidden Markov Model) for each word is trained by Baum-Welch algorithm. Viterbi decoding is used for finding best match from the HMM models.
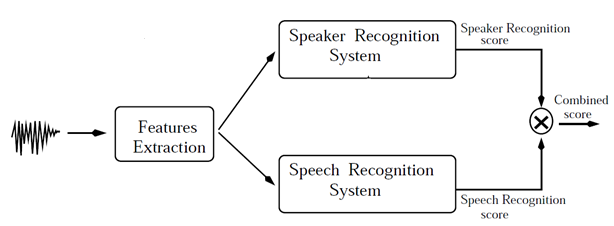
Combining speech and speaker recognition systems
Based on the speech model the system decides whether or not the uttered speech matches what was prompted to utter. Similarly, based on the speaker model, the system decides whether or not the speaker is claimed one.
Finally for verification, the score of both speaker and speech recognition is combined to get combined score, to accept or reject the user’s claim.
Text Prompted Remote Speaker Authentication : Joint Speech and Speaker Recognition/Verification System :: Major Project ::: Introduction的更多相关文章
- ACL2019: 《GraphRel: Modeling Text as Relational Graphs for Joint Entity and Relation Extraction》源码解析
论文地址:<GraphRel: Modeling Text as Relational Graphs for Joint Entity and Relation Extraction> G ...
- Csharp: speech to text, text to speech in win
using System; using System.Collections.Generic; using System.ComponentModel; using System.Data; usin ...
- remote: http basic: access denied fatal: authentication failed for '‘解决办法
问题描述 由于这个项目代码使用https 进行clone,为什么?因为代码库ssh有问题!fuck! 导致在push代码的时候出现了 remote: http basic: access denied ...
- 十几个remote control software
5 alternatives to LogMeIn Free for remote PC access VNC VNC, or Virtual Network Computing, isn’t its ...
- CMUSphinx Learn - Basic concepts of speech
Basic concepts of speech Speech is a complex phenomenon. People rarely understand how is it produced ...
- C#中的System.Speech命名空间初探
本程序是口算两位数乘法,随机生成两个两位数,用语音读出来.然后开启语音识别,接受用户输入,知道答案正确关闭语音识别.用户说答案时,可以说“再说一遍”重复题目. 关键是GrammarBuilder和Ch ...
- Using JAAS Authentication in Java Clients---weblogic document
The following topics are covered in this section: JAAS and WebLogic Server JAAS Authentication Devel ...
- Install TightVNC Server in RHEL/CentOS and Fedora to Access Remote Desktops
Virtual Networking Computing (VNC) is a Kind of remote sharing system that makes it possible to take ...
- Asp.Net Core Authentication Middleware And Generate Token
.mytitle { background: #2B6695; color: white; font-family: "微软雅黑", "宋体", "黑 ...
随机推荐
- Tomcat8服务
Windows部署Tomcat8服务在windows上部署Tomcat服务后,可以将Tomcat设为开机启动,即开机后Tomcat就会自动运行.这样就不用每次进到Tomcat的bin目录双击start ...
- 微信支付(APP支付)-服务端开发(二 )
如果你已经可以微信支付成功,那么你已经成功90%,剩下的就是订单确认问题了. 接上一篇文章,今天我们来谈一谈,订单查询与确认: APP端支付成功之后,会再次向服务端发起请求,确认付款订单时候成功,同时 ...
- dedecms搜索下拉
今天公司用dedecms做一个音乐站,要用到下拉标题搜索,我在本地做的一个测试结果 以下是代码部分(ps:二级栏目不用的可以删除代码,如果只调用某一个栏目或者2个栏目可以用typeid='1,2'):
- bash: cd: too many arguments 报错
路径名或者变量有空格时候,会造成参数太多的错误提示 解决方法:把空格的地方用引号包括起来
- LibreOJ #524. 「LibreOJ β Round #4」游戏
二次联通门 : LibreOJ #524. 「LibreOJ β Round #4」游戏 /* LibreOJ #524. 「LibreOJ β Round #4」游戏 找找规律就会发现.. 当有X的 ...
- C++中unique函数的用法总结
个人感觉,unique是STL中很实用的函数之一,需要#include,下面来简单介绍一下它的作用. unique的作用是"去掉"容器中相邻元素的重复元素,这里去掉要加一个引号,为 ...
- 【概率论】6-3:中心极限定理(The Central Limit Theorem)
title: [概率论]6-3:中心极限定理(The Central Limit Theorem) categories: - Mathematic - Probability keywords: - ...
- C 库函数 - strstr()
定义 char *strstr(const char *haystack, const char *needle) 参数 haystack -- 要被检索的 C 字符串. needle -- 在 ha ...
- [WEB安全]PHP伪协议总结
0x01 简介 首先来看一下有哪些文件包含函数: include.require.include_once.require_once.highlight_file show_source .readf ...
- LCT 总结
刚开始学lct花了一晚上研究模板,调出来就感觉不怎么难打了. 对板子的浅显理解: lct维护树形联通块,通过splay维护实链,可以把需要的路径变换到一颗splay上维护. splay中的关系只依赖实 ...
