Python Ethical Hacking - VULNERABILITY SCANNER(8)
Implementing Code To Discover XSS in Parameters
1. Watch the URL of the XSS reflected page carefully.
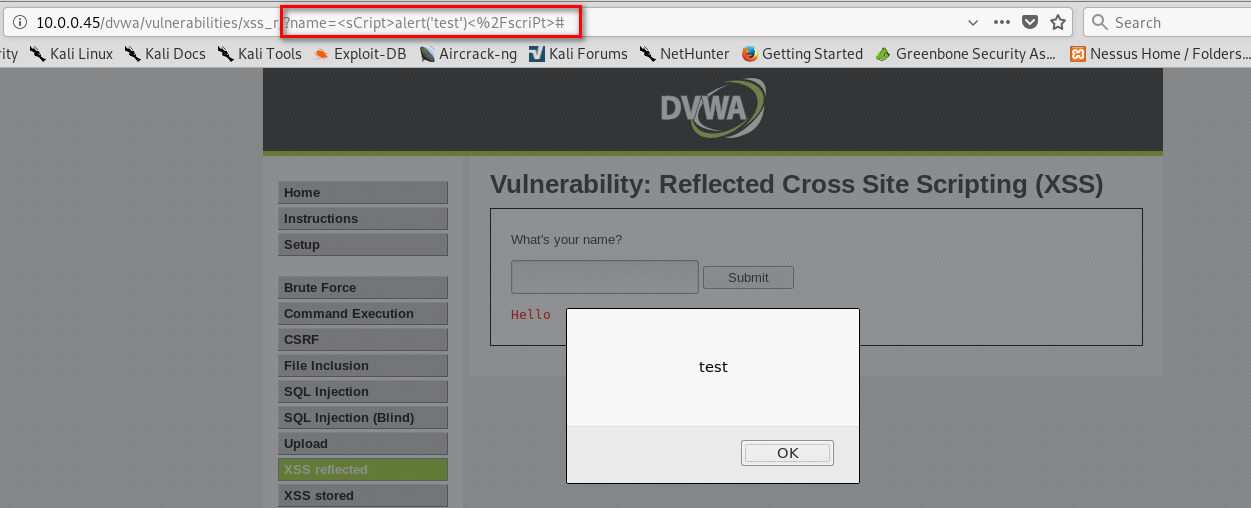
2. Add the test_xss_in_link method in the Scanner class.
#!/usr/bin/env python import requests
import re
from bs4 import BeautifulSoup
from urllib.parse import urljoin class Scanner:
def __init__(self, url, ignore_links):
self.session = requests.Session()
self.target_url = url
self.target_links = []
self.links_to_ignore = ignore_links def extract_links_from(self, url):
response = self.session.get(url)
return re.findall('(?:href=")(.*?)"', response.content.decode(errors='ignore')) def crawl(self, url=None):
if url == None:
url = self.target_url
href_links = self.extract_links_from(url)
for link in href_links:
link = urljoin(url, link) if "#" in link:
link = link.split("#")[0] if self.target_url in link and link not in self.target_links and link not in self.links_to_ignore:
self.target_links.append(link)
print(link)
self.crawl(link) def extract_forms(self, url):
response = self.session.get(url)
parsed_html = BeautifulSoup(response.content.decode(), features="lxml")
return parsed_html.findAll("form") def submit_form(self, form, value, url):
action = form.get("action")
post_url = urljoin(url, action)
method = form.get("method") inputs_list = form.findAll("input")
post_data = {}
for input in inputs_list:
input_name = input.get("name")
input_type = input.get("type")
input_value = input.get("value")
if input_type == "text":
input_value = value post_data[input_name] = input_value
if method == "post":
return requests.post(post_url, data=post_data)
return self.session.get(post_url, params=post_data) def run_scanner(self):
for link in self.target_links:
forms = self.extract_forms(link)
for form in forms:
print("[+] Testing form in " + link) if "=" in link:
print("[+] Testing " + link) def test_xss_in_link(self, url):
xss_test_script = "<sCript>alert('test')</scriPt>"
url = url.replace("=", "=" + xss_test_script)
response = self.session.get(url)
return xss_test_script in response.content.decode() def test_xss_in_form(self, form, url):
xss_test_script = "<sCript>alert('test')</scriPt>"
response = self.submit_form(form, xss_test_script, url)
return xss_test_script in response.content.decode()
3. Test this scanner.
#!/usr/bin/env python import scanner target_url = "http://10.0.0.45/dvwa/"
links_to_ignore = "http://10.0.0.45/dvwa/logout.php" data_dict = {"username": "admin", "password": "password", "Login": "submit"} vuln_scanner = scanner.Scanner(target_url, links_to_ignore)
vuln_scanner.session.post("http://10.0.0.45/dvwa/login.php", data=data_dict) # vuln_scanner.crawl()
forms = vuln_scanner.extract_forms("http://10.0.0.45/dvwa/vulnerabilities/xss_r/")
print(forms)
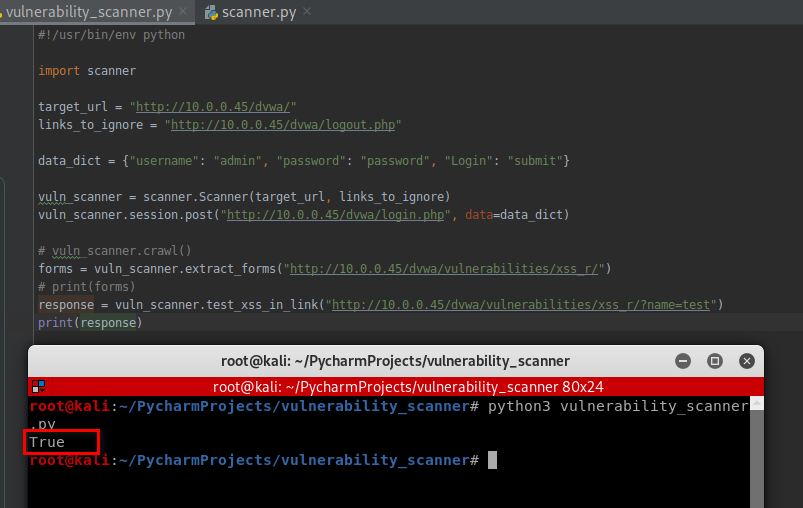
response = vuln_scanner.test_xss_in_link("http://10.0.0.45/dvwa/vulnerabilities/xss_r/?name=test")
print(response)
Test the web page - http://10.0.0.45/dvwa/vulnerabilities/xss_r/?name=test:
vuln_scanner.test_xss_in_link("http://10.0.0.45/dvwa/vulnerabilities/xss_r/?name=test")
It is vulnerable on XSS.
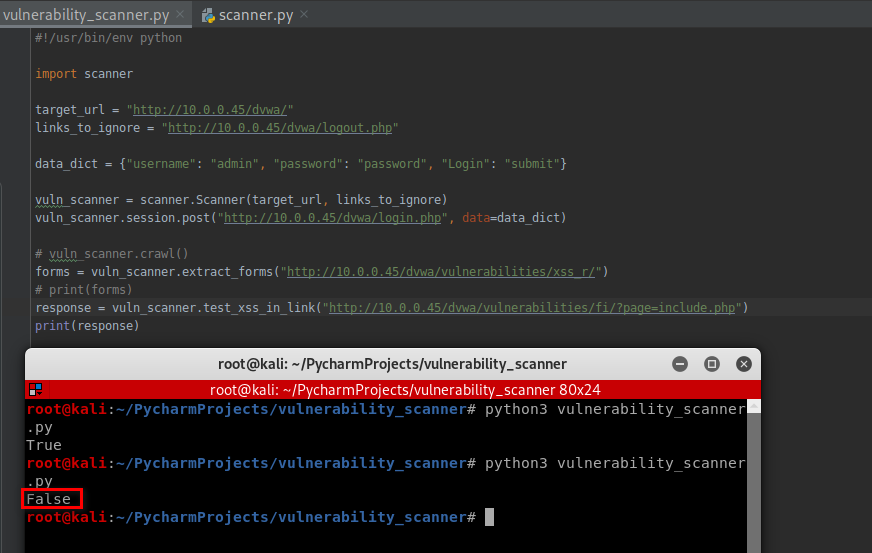
Test the web page - http://10.0.0.45/dvwa/vulnerabilities/fi/?page=include.php:
vuln_scanner.test_xss_in_link("http://10.0.0.45/dvwa/vulnerabilities/fi/?page=include.php")
It is not vulnerable on XSS.
Python Ethical Hacking - VULNERABILITY SCANNER(8)的更多相关文章
- Python Ethical Hacking - VULNERABILITY SCANNER(9)
Automatically Discovering Vulnerabilities Using the Vulnerability Scanner 1. Modify the run_scanner ...
- Python Ethical Hacking - VULNERABILITY SCANNER(7)
VULNERABILITY_SCANNER How to discover a vulnerability in a web application? 1. Go into every possibl ...
- Python Ethical Hacking - VULNERABILITY SCANNER(4)
Extracting & Submitting Forms Automatically Target website:http://10.0.0.45/dvwa/vulnerabilities ...
- Python Ethical Hacking - VULNERABILITY SCANNER(2)
VULNERABILITY_SCANNER How to discover a vulnerability in a web application? 1. Go into every possibl ...
- Python Ethical Hacking - VULNERABILITY SCANNER(3)
Polish the Python code using sending requests in a session Class Scanner. #!/usr/bin/env python impo ...
- Python Ethical Hacking - VULNERABILITY SCANNER(1)
HTTP REQUESTS BASIC INFORMATION FLOW The user clicks on a link. HTML website generates a request(cli ...
- Python Ethical Hacking - VULNERABILITY SCANNER(6)
EXPLOITATION - XSS VULNS EXPLOITING XSS Run any javascript code. Beef framework can be used to hook ...
- Python Ethical Hacking - VULNERABILITY SCANNER(5)
EXPLOITATION - XSS VULNS XSS - CROSS SITE SCRIPTING VULNS Allow an attacker to inject javascript cod ...
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
随机推荐
- Java 内存溢出(java.lang.OutOfMemoryError)的常见情况和处理方式
导致OutOfMemoryError异常的常见原因有以下几种: 内存中加载的数据量过于庞大,如一次从数据库取出过多数据: 集合类中有对对象的引用,使用完后未清空,使得JVM不能回收: 代码中存在死循环 ...
- fatal error C1083: Cannot open include file: '_defs.h': No such file or directory
b-PAC SDK: https://www.baidu.com/link?url=p6FcG0fvFl6XJf9QdSFLBP16eaS03jOQsdr0zd8cYprHWwqVy5t53bzMrA ...
- C语言宏技巧 X宏
前言 本文介绍下X宏的使用 首先简单介绍下宏的几种用法 #define STRCAT(X,Y) X##Y #define _STR(X) #@X #define STR(X) #X #define L ...
- C/C++以及Linux文件操作备忘录
目录 C文件操作 文件开关 文件读写 C++文件操作 Linux文件操作 打开 C文件操作 #include<stdio.h> stdin, stdout, stderr 文件开关 /* ...
- redis基础二----操作hash
上面usr就是hash的名字,usr这个hash中存储了key 为id.name和age的值 一个hash相当于一个数据对象,里面可以存储key为id name age的值 2.批量插入一个hash数 ...
- Idea集成git常用命令
git status --查看文件状态 untracked: 未跟踪 一般为新增文件 git add 状态改为staged git add +文件 git add -A +路径 修改过的未被跟 ...
- Java 线程基础,从这篇开始
线程作为操作系统中最少调度单位,在当前系统的运行环境中,一般都拥有多核处理器,为了更好的充分利用 CPU,掌握其正确使用方式,能更高效的使程序运行.同时,在 Java 面试中,也是极其重要的一个模块. ...
- 浅谈dfs
搜索(dfs) 搜索分为bfs与dfs 他们的算法思路都是相同的--穷举 可以说,搜索是万能的,但是复杂度往往是指数级的,往往是穷途末路才用的最后方案 dfs dfs核心操作:回溯+前进 想想你第一次 ...
- 第二部分用户交互程序开发,通过paramiko记录ssh会话记录
需求及任务:实现一个给用户登录的界面(通过ssh登到堡垒机上,然后给它展现一个命令行的页面,然后他选择登哪台机器,一选择就连上去且把日志也记录下来). 先在admin创建几条组数据并与用户关联如下图: ...
- linux系统,没有安装任何编辑器的情况,如何操作文件
[清空文件] echo " " > filename [添加内容] echo "123" >> filename
