【转】Encrypt ConnectionString in Web.Config 【加密ASP.NET web.config数据库链接字串】
原文链接:https://www.codeproject.com/Tips/795135/Encrypt-ConnectionString-in-Web-Config
web.config中一般会存放一些关键的信息,比如数据库链接字串,如果没有加密,就会有安全风险。
本次文章转载一个印度小哥写的教程,使用.net framwork自带的aspnet_regiis组件为web.config加密
Introduction
The tip gives you information about how to encrypt the connection string in Web.Config to increase the security and keep the connection with the database secure. There is so much other sensitive information that can be encrypted but in this tip, I'll particularly talk about encrypting the ConnectionString in Web.Config file.
Why It Is Important?
Encrypting sensitive sections of the Web.Config is important because they are just that, sensitive. Think about production Web.Config file. It may contain all information that requires running your web application. There are often passwords for SQL database connections, SMTP server, API Keys, or other critical information. In addition to this, Web.Config files are usually treated as just another source code file, that means, any developer on the team, or more accurately anyone with access to the source code, can see what information is stored in Web.Config file.
Encrypting the Connection String
In our example, we will encrypt ConnectionString in our Web.Config file.
Before Encrypting Web.Config
If you look at the below Config file, it can be easily readable. This doesn't seem to be secure if anyone has access to your Web.Config file.
<configuration>
<connectionStrings>
<add name="SqlServices" connectionString="Data Source=localhost;Integrated Security=SSPI;Initial Catalog=Northwind;" />
</connectionStrings>
</configuration>
Encrypting Web.Config
- Open Command Prompt with Administrator privileges
- At the Command Prompt, enter:
Hide Copy Code
cd C:\Windows\Microsoft.NET\Framework\v4.0.30319
- In case your web Config is located in "D:\Articles\EncryptWebConfig" directory path, then enter the following to encrypt the
ConnectionString:Hide Copy CodeASPNET_REGIIS -pef "connectionStrings" "D:\Articles\EncryptWebConfig"
Use Aspnet_regiis.exe tool with the
–pefoption and specify the application path as shown above.Note: The parameter "
connectionStrings" is case sensitive.
After Encrypting Web.Config
After encrypting your ConnectionStrings section, your ConnectionStrings will not be in a readable format.
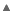 Copy Code
Copy Code<configuration>
<connectionStrings configProtectionProvider="RsaProtectedConfigurationProvider">
<EncryptedData Type="http://www.w3.org/2001/04/xmlenc#Element" xmlns="http://www.w3.org/2001/04/xmlenc#">
<EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#tripledes-cbc" />
<KeyInfo xmlns="http://www.w3.org/2000/09/xmldsig#">
<EncryptedKey xmlns="http://www.w3.org/2001/04/xmlenc#">
<EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#rsa-1_5" />
<KeyInfo xmlns="http://www.w3.org/2000/09/xmldsig#">
<KeyName>Rsa Key</KeyName>
</KeyInfo>
<CipherData>
<CipherValue>ZbDTF00MYzUUW5U3w3PU0rfiAH1UKhvuLSNWPmB/YifBKne6HAWfVc3CnKVimyP8SFyamaR5oAIAxj/xavfpox8EOYXNI+afsksiuA5huSDupCZKNuXq+VCZrdIyn6YOq+W7s3Ojlu7q9VwKcoKurl28l2hcPvWkBk11KYB7hr0=</CipherValue>
</CipherData>
</EncryptedKey>
</KeyInfo>
<CipherData>
<CipherValue>42IPPRUjJxCNDHEBLCAJI4/NyLpLueZSBzUXO69lVdZU8+nLpxO+opnbZNxqddyzNnbCO1Uk2Da3ljExkqnLIxT2zs90JAhZvJ5ljIgCipq7ZEp7zHOpvTH9fBGoZJJWhgdddOrHZsLDE9mILjlvBHDhPQrYcMHtY6oLIbxJq92it82iBJv0fS7v1S/o0p4hAtfky+6hXCZWSKUJHr88NDrKe2EEK3mazD2QD5Ozf/w=</CipherValue>
</CipherData>
</EncryptedData>
</connectionStrings>
</configuration>
Accessing Decrypted Configuration Settings
It’s very good to know that ASP.NET automatically decrypts the contents of the Web.Config file when it processes the file. Therefore, no additional steps are required to decrypt the encrypted configuration settings. You can run your existing application by encrypting your Web.Config file and it will run perfectly without any modification to your existing code. Isn't that interesting?
string ConnString = ConfigurationManager.ConnectionStrings[1].ToString();
Decrypting the Connection String
Is it possible to decrypt my Web.Config so that I can read it in original format?
Yes, it is possible.
Simply perform the following command to decrypt the connectionStrings element in the Web.config file.
ASPNET_REGIIS -pdf "connectionStrings" "D:\Articles\EncryptWebConfig"
Note: The parameter "connectionStrings" is case sensitive.
Questions and Answers
1. You might ask me a question if Web.Config file can be encrypted and decrypted using ASPNET_REGIIS then anyone who has access to Web.Config file can decrypt the content, right?
To answer this question, I would say no, if you encrypt your Config file, then your machine would store your keys and if you copy the Config file to a different system and try to decrypt it, then you might get an error.
Pros
- Web.Config sensitive information is not in a readable condition (after encryption)
- You don't have to explicitly write code to decrypt the Web.Config file as ASP.NET automatically decrypts the configuration and processes your request
Cons
- You can't modify the encrypted content on the fly. It requires you to decrypt the content before editing.
Points of Interest
Web.Config encryption only takes a couple moments and provides much more security than a clear-text file. It may not be enough to thwart a hacker that has full access to your entire server.
I'm encrypting all my sensitive data stored in Web.Config after learning the concept of encryption. How about you?
【转】Encrypt ConnectionString in Web.Config 【加密ASP.NET web.config数据库链接字串】的更多相关文章
- ASP.NET Web API和ASP.NET Web MVC中使用Ninject
ASP.NET Web API和ASP.NET Web MVC中使用Ninject 先附上源码下载地址 一.准备工作 1.新建一个名为MvcDemo的空解决方案 2.新建一个名为MvcDemo.Web ...
- 【翻译】使用Knockout, Web API 和 ASP.Net Web Forms 进行简单数据绑定
原文地址:http://www.dotnetjalps.com/2013/05/Simple-data-binding-with-Knockout-Web-API-and-ASP-Net-Web-Fo ...
- Knockout, Web API 和 ASP.Net Web Forms 进行简单数据绑定
使用Knockout, Web API 和 ASP.Net Web Forms 进行简单数据绑定 原文地址:http://www.dotnetjalps.com/2013/05/Simple-da ...
- App.config使用ASP.NET Web Project的Transformation
1.创建对应configuration的App.config文件,比如:App.Debug.config.App.Release.config. 2.编辑项目文件,将App.*.config文件的Bu ...
- [转] JSON Web Token in ASP.NET Web API 2 using Owin
本文转自:http://bitoftech.net/2014/10/27/json-web-token-asp-net-web-api-2-jwt-owin-authorization-server/ ...
- JSON Web Token in ASP.NET Web API 2 using Owin
In the previous post Decouple OWIN Authorization Server from Resource Server we saw how we can separ ...
- 在ASP.NET Web API和ASP.NET Web MVC中使用Ninject
先附上源码下载地址 一.准备工作 1.新建一个名为MvcDemo的空解决方案 2.新建一个名为MvcDemo.WebUI的空MVC应用程序 3.使用NuGet安装Ninject库 二.在ASP.N ...
- 【Web API2】ASP.NET Web API Security
实现安全的方式既可以是host提供,也可以框架提供. 1,HTTP Module 方式,工作在IIS上,所以web api要托管在IIS上才行.其作用于HTTP管道的最前端,所以这种方式影响的是全局, ...
- Web API 2 入门——使用Web API与ASP.NET Web窗体(谷歌翻译)
在这篇文章中 概观 创建Web窗体项目 创建模型和控制器 添加路由信息 添加客户端AJAX 作者:Mike Wasson 虽然ASP.NET Web API与ASP.NET MVC打包在一起,但很容易 ...
随机推荐
- FPN(feature pyramid networks)
多数的object detection算法都是只采用顶层特征做预测,但我们知道低层的特征语义信息比较少,但是目标位置准确:高层的特征语义信息比较丰富,但是目标位置比较粗略.另外虽然也有些算法采用多尺度 ...
- 使用ActiveMQ实现简易聊天功能
一 什么是消息队列 我们可以把消息队列比作是一个存放消息的容器,当我们需要使用消息的时候可以取出消息供自己使用.消息队列是分布式系统中重要的组件,使用消息队列主要是为了通过异步处理提高系统性能和削峰. ...
- 【后缀数组之height数组】
模板奉上 int rank[maxn],height[maxn]; void calheight(int *r,int *sa,int n) { ; ;i<=n;i++) rank[sa[i]] ...
- ArchLinux借助Winetricks-zh安裝WineQQ8.1
Wine是一个在x86.x86-64上容许类Unix操作系统在X Window System下运行Microsoft Windows程序的软件.Wine有另一个非官方名称,"Windows ...
- 模块time, datetime的用法
一. time time库提供了各种操作时间的方法 1. time.asctime([tuple]):将一个时间元组转换成一个可读的24个时间字符串. >>> time.asc ...
- [转](译)KVO的内部实现
转载自:http://www.cocoachina.com/applenews/devnews/2014/0107/7667.html 09年的一篇文章,比较深入地阐述了KVO的内部实现. K ...
- mongo的持久化之Journaling
参考文章: http://database.51cto.com/art/201110/295772.htm http://blog.chinaunix.net/uid-15795819-id-3381 ...
- 【笔记】Django的视图
[笔记]Django的视图 Python Django Django的View(视图) 一个视图函数(类),简称视图,是一个简单的Python 函数(类),它接受Web请求并且返回Web响应. 响应 ...
- js高级程序设计 笔记 --- 表单
一,基础知识 在html中,表单是form元素,而在js中,表单对应的是HTMLFormElement类型,继承自HTMLElement,其独特的属性和方法有(常见): action:接收请求的URL ...
- 简易APB4 slave实践
一个简易的(不完整的)APB4 slave的可以没有PREADY和PSLVERR,这两个信号都被赋予常数,以及没有PPROT. 两种不同类型的寄存器: 图: 普通寄存器电路图 图: 带读写控制寄存器电 ...
