防火墙(入站规则)C++修改方法 以解决服务器无法连接问题
为啥要关注防火墙
今天项目中的p2p直连遇到了问题。经过排查,发现充当服务器的一端进入listen状态后,另外的客户端一端connect失败。
错误码10060(超时)。
开始时怀疑客户端connect的时候,服务器还没准备好,或者哪里的代码有问题。然后下载了一个tcp测试工具。启动后发现
测试工具也无法正常直连。
然后发现原因是网络管理(防火墙)的问题。

即机器上的入站规则没有添加,导致连接的时候被防火墙屏蔽了。把“阻止”改成“允许”就ok了。
看了下已有的入站规则
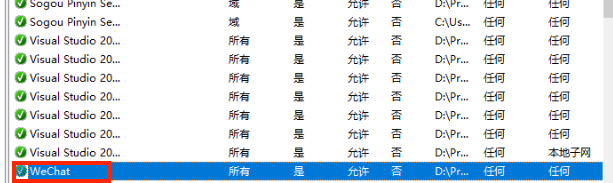
如微信是已经写入防火墙的。看来应该有程序写入防火墙的方法。
搜索了下:
防火墙相关API目录:
https://docs.microsoft.com/en-us/windows/win32/api/netfw/
网上找到的示例代码(2010年前的代码,我电脑的win10无效)
#include "stdafx.h"
#include <windows.h>
#include <crtdbg.h>
#include <netfw.h>
#include <objbase.h>
#include <oleauto.h>
#include <stdio.h> #pragma comment( lib, "ole32.lib" )
#pragma comment( lib, "oleaut32.lib" )
HRESULT WindowsFirewallInitialize(OUT INetFwProfile** fwProfile)
{
HRESULT hr = S_OK;
INetFwMgr* fwMgr = NULL;
INetFwPolicy* fwPolicy = NULL; _ASSERT(fwProfile != NULL); *fwProfile = NULL; // Create an instance of the firewall settings manager.
hr = CoCreateInstance(
__uuidof(NetFwMgr),
NULL,
CLSCTX_INPROC_SERVER,
__uuidof(INetFwMgr),
(void**)&fwMgr
);
if (FAILED(hr))
{
printf("CoCreateInstance failed: 0x%08lx\n", hr);
goto error;
} // Retrieve the local firewall policy.
hr = fwMgr->get_LocalPolicy(&fwPolicy);
if (FAILED(hr))
{
printf("get_LocalPolicy failed: 0x%08lx\n", hr);
goto error;
} // Retrieve the firewall profile currently in effect.
hr = fwPolicy->get_CurrentProfile(fwProfile);
if (FAILED(hr))
{
printf("get_CurrentProfile failed: 0x%08lx\n", hr);
goto error;
} error: // Release the local firewall policy.
if (fwPolicy != NULL)
{
fwPolicy->Release();
} // Release the firewall settings manager.
if (fwMgr != NULL)
{
fwMgr->Release();
} return hr;
} void WindowsFirewallCleanup(IN INetFwProfile* fwProfile)
{
// Release the firewall profile.
if (fwProfile != NULL)
{
fwProfile->Release();
}
} HRESULT WindowsFirewallIsOn(IN INetFwProfile* fwProfile, OUT BOOL* fwOn)
{
HRESULT hr = S_OK;
VARIANT_BOOL fwEnabled; _ASSERT(fwProfile != NULL);
_ASSERT(fwOn != NULL); *fwOn = FALSE; // Get the current state of the firewall.
hr = fwProfile->get_FirewallEnabled(&fwEnabled);
if (FAILED(hr))
{
printf("get_FirewallEnabled failed: 0x%08lx\n", hr);
goto error;
} // Check to see if the firewall is on.
if (fwEnabled != VARIANT_FALSE)
{
*fwOn = TRUE;
printf("The firewall is on.\n");
}
else
{
printf("The firewall is off.\n");
} error: return hr;
} HRESULT WindowsFirewallTurnOn(IN INetFwProfile* fwProfile)
{
HRESULT hr = S_OK;
BOOL fwOn; _ASSERT(fwProfile != NULL); // Check to see if the firewall is off.
hr = WindowsFirewallIsOn(fwProfile, &fwOn);
if (FAILED(hr))
{
printf("WindowsFirewallIsOn failed: 0x%08lx\n", hr);
goto error;
} // If it is, turn it on.
if (!fwOn)
{
// Turn the firewall on.
hr = fwProfile->put_FirewallEnabled(VARIANT_TRUE);
if (FAILED(hr))
{
printf("put_FirewallEnabled failed: 0x%08lx\n", hr);
goto error;
} printf("The firewall is now on.\n");
} error: return hr;
} HRESULT WindowsFirewallTurnOff(IN INetFwProfile* fwProfile)
{
HRESULT hr = S_OK;
BOOL fwOn; _ASSERT(fwProfile != NULL); // Check to see if the firewall is on.
hr = WindowsFirewallIsOn(fwProfile, &fwOn);
if (FAILED(hr))
{
printf("WindowsFirewallIsOn failed: 0x%08lx\n", hr);
goto error;
} // If it is, turn it off.
if (fwOn)
{
// Turn the firewall off.
hr = fwProfile->put_FirewallEnabled(VARIANT_FALSE);
if (FAILED(hr))
{
printf("put_FirewallEnabled failed: 0x%08lx\n", hr);
goto error;
} printf("The firewall is now off.\n");
} error: return hr;
} HRESULT WindowsFirewallAppIsEnabled(
IN INetFwProfile* fwProfile,
IN const wchar_t* fwProcessImageFileName,
OUT BOOL* fwAppEnabled
)
{
HRESULT hr = S_OK;
BSTR fwBstrProcessImageFileName = NULL;
VARIANT_BOOL fwEnabled;
INetFwAuthorizedApplication* fwApp = NULL;
INetFwAuthorizedApplications* fwApps = NULL; _ASSERT(fwProfile != NULL);
_ASSERT(fwProcessImageFileName != NULL);
_ASSERT(fwAppEnabled != NULL); *fwAppEnabled = FALSE; // Retrieve the authorized application collection.
hr = fwProfile->get_AuthorizedApplications(&fwApps);
if (FAILED(hr))
{
printf("get_AuthorizedApplications failed: 0x%08lx\n", hr);
goto error;
} // Allocate a BSTR for the process image file name.
fwBstrProcessImageFileName = SysAllocString(fwProcessImageFileName);
if (SysStringLen(fwBstrProcessImageFileName) == )
{
hr = E_OUTOFMEMORY;
printf("SysAllocString failed: 0x%08lx\n", hr);
goto error;
} // Attempt to retrieve the authorized application.
hr = fwApps->Item(fwBstrProcessImageFileName, &fwApp);
if (SUCCEEDED(hr))
{
// Find out if the authorized application is enabled.
hr = fwApp->get_Enabled(&fwEnabled);
if (FAILED(hr))
{
printf("get_Enabled failed: 0x%08lx\n", hr);
goto error;
} if (fwEnabled != VARIANT_FALSE)
{
// The authorized application is enabled.
*fwAppEnabled = TRUE; printf(
"Authorized application %lS is enabled in the firewall.\n",
fwProcessImageFileName
);
}
else
{
printf(
"Authorized application %lS is disabled in the firewall.\n",
fwProcessImageFileName
);
}
}
else
{
// The authorized application was not in the collection.
hr = S_OK; printf(
"Authorized application %lS is disabled in the firewall.\n",
fwProcessImageFileName
);
} error: // Free the BSTR.
SysFreeString(fwBstrProcessImageFileName); // Release the authorized application instance.
if (fwApp != NULL)
{
fwApp->Release();
} // Release the authorized application collection.
if (fwApps != NULL)
{
fwApps->Release();
} return hr;
} HRESULT WindowsFirewallAddApp(
IN INetFwProfile* fwProfile,
IN const wchar_t* fwProcessImageFileName,
IN const wchar_t* fwName
)
{
HRESULT hr = S_OK;
BOOL fwAppEnabled;
BSTR fwBstrName = NULL;
BSTR fwBstrProcessImageFileName = NULL;
INetFwAuthorizedApplication* fwApp = NULL;
INetFwAuthorizedApplications* fwApps = NULL; _ASSERT(fwProfile != NULL);
_ASSERT(fwProcessImageFileName != NULL);
_ASSERT(fwName != NULL); // First check to see if the application is already authorized.
hr = WindowsFirewallAppIsEnabled(
fwProfile,
fwProcessImageFileName,
&fwAppEnabled
);
if (FAILED(hr))
{
printf("WindowsFirewallAppIsEnabled failed: 0x%08lx\n", hr);
goto error;
} // Only add the application if it isn't already authorized.
if (!fwAppEnabled)
{
// Retrieve the authorized application collection.
hr = fwProfile->get_AuthorizedApplications(&fwApps);
if (FAILED(hr))
{
printf("get_AuthorizedApplications failed: 0x%08lx\n", hr);
goto error;
} // Create an instance of an authorized application.
hr = CoCreateInstance(
__uuidof(NetFwAuthorizedApplication),
NULL,
CLSCTX_INPROC_SERVER,
__uuidof(INetFwAuthorizedApplication),
(void**)&fwApp
);
if (FAILED(hr))
{
printf("CoCreateInstance failed: 0x%08lx\n", hr);
goto error;
} // Allocate a BSTR for the process image file name.
fwBstrProcessImageFileName = SysAllocString(fwProcessImageFileName);
if (SysStringLen(fwBstrProcessImageFileName) == )
{
hr = E_OUTOFMEMORY;
printf("SysAllocString failed: 0x%08lx\n", hr);
goto error;
} // Set the process image file name.
hr = fwApp->put_ProcessImageFileName(fwBstrProcessImageFileName);
if (FAILED(hr))
{
printf("put_ProcessImageFileName failed: 0x%08lx\n", hr);
goto error;
} // Allocate a BSTR for the application friendly name.
fwBstrName = SysAllocString(fwName);
if (SysStringLen(fwBstrName) == )
{
hr = E_OUTOFMEMORY;
printf("SysAllocString failed: 0x%08lx\n", hr);
goto error;
} // Set the application friendly name.
hr = fwApp->put_Name(fwBstrName);
if (FAILED(hr))
{
printf("put_Name failed: 0x%08lx\n", hr);
goto error;
} // Add the application to the collection.
hr = fwApps->Add(fwApp);
if (FAILED(hr))
{
printf("Add failed: 0x%08lx\n", hr);
goto error;
} printf(
"Authorized application %lS is now enabled in the firewall.\n",
fwProcessImageFileName
);
} error: // Free the BSTRs.
SysFreeString(fwBstrName);
SysFreeString(fwBstrProcessImageFileName); // Release the authorized application instance.
if (fwApp != NULL)
{
fwApp->Release();
} // Release the authorized application collection.
if (fwApps != NULL)
{
fwApps->Release();
} return hr;
} HRESULT WindowsFirewallPortIsEnabled(
IN INetFwProfile* fwProfile,
IN LONG portNumber,
IN NET_FW_IP_PROTOCOL ipProtocol,
OUT BOOL* fwPortEnabled
)
{
HRESULT hr = S_OK;
VARIANT_BOOL fwEnabled;
INetFwOpenPort* fwOpenPort = NULL;
INetFwOpenPorts* fwOpenPorts = NULL; _ASSERT(fwProfile != NULL);
_ASSERT(fwPortEnabled != NULL); *fwPortEnabled = FALSE; // Retrieve the globally open ports collection.
hr = fwProfile->get_GloballyOpenPorts(&fwOpenPorts);
if (FAILED(hr))
{
printf("get_GloballyOpenPorts failed: 0x%08lx\n", hr);
goto error;
} // Attempt to retrieve the globally open port.
hr = fwOpenPorts->Item(portNumber, ipProtocol, &fwOpenPort);
if (SUCCEEDED(hr))
{
// Find out if the globally open port is enabled.
hr = fwOpenPort->get_Enabled(&fwEnabled);
if (FAILED(hr))
{
printf("get_Enabled failed: 0x%08lx\n", hr);
goto error;
} if (fwEnabled != VARIANT_FALSE)
{
// The globally open port is enabled.
*fwPortEnabled = TRUE; printf("Port %ld is open in the firewall.\n", portNumber);
}
else
{
printf("Port %ld is not open in the firewall.\n", portNumber);
}
}
else
{
// The globally open port was not in the collection.
hr = S_OK; printf("Port %ld is not open in the firewall.\n", portNumber);
} error: // Release the globally open port.
if (fwOpenPort != NULL)
{
fwOpenPort->Release();
} // Release the globally open ports collection.
if (fwOpenPorts != NULL)
{
fwOpenPorts->Release();
} return hr;
} HRESULT WindowsFirewallPortAdd(
IN INetFwProfile* fwProfile,
IN LONG portNumber,
IN NET_FW_IP_PROTOCOL ipProtocol,
IN const wchar_t* name
)
{
HRESULT hr = S_OK;
BOOL fwPortEnabled;
BSTR fwBstrName = NULL;
INetFwOpenPort* fwOpenPort = NULL;
INetFwOpenPorts* fwOpenPorts = NULL; _ASSERT(fwProfile != NULL);
_ASSERT(name != NULL); // First check to see if the port is already added.
hr = WindowsFirewallPortIsEnabled(
fwProfile,
portNumber,
ipProtocol,
&fwPortEnabled
);
if (FAILED(hr))
{
printf("WindowsFirewallPortIsEnabled failed: 0x%08lx\n", hr);
goto error;
} // Only add the port if it isn't already added.
if (!fwPortEnabled)
{
// Retrieve the collection of globally open ports.
hr = fwProfile->get_GloballyOpenPorts(&fwOpenPorts);
if (FAILED(hr))
{
printf("get_GloballyOpenPorts failed: 0x%08lx\n", hr);
goto error;
} // Create an instance of an open port.
hr = CoCreateInstance(
__uuidof(NetFwOpenPort),
NULL,
CLSCTX_INPROC_SERVER,
__uuidof(INetFwOpenPort),
(void**)&fwOpenPort
);
if (FAILED(hr))
{
printf("CoCreateInstance failed: 0x%08lx\n", hr);
goto error;
} // Set the port number.
hr = fwOpenPort->put_Port(portNumber);
if (FAILED(hr))
{
printf("put_Port failed: 0x%08lx\n", hr);
goto error;
} // Set the IP protocol.
hr = fwOpenPort->put_Protocol(ipProtocol);
if (FAILED(hr))
{
printf("put_Protocol failed: 0x%08lx\n", hr);
goto error;
} // Allocate a BSTR for the friendly name of the port.
fwBstrName = SysAllocString(name);
if (SysStringLen(fwBstrName) == )
{
hr = E_OUTOFMEMORY;
printf("SysAllocString failed: 0x%08lx\n", hr);
goto error;
} // Set the friendly name of the port.
hr = fwOpenPort->put_Name(fwBstrName);
if (FAILED(hr))
{
printf("put_Name failed: 0x%08lx\n", hr);
goto error;
} // Opens the port and adds it to the collection.
hr = fwOpenPorts->Add(fwOpenPort);
if (FAILED(hr))
{
printf("Add failed: 0x%08lx\n", hr);
goto error;
} printf("Port %ld is now open in the firewall.\n", portNumber);
} error: // Free the BSTR.
SysFreeString(fwBstrName); // Release the open port instance.
if (fwOpenPort != NULL)
{
fwOpenPort->Release();
} // Release the globally open ports collection.
if (fwOpenPorts != NULL)
{
fwOpenPorts->Release();
} return hr;
} int _tmain(int argc, _TCHAR* argv[])
{
HRESULT hr = S_OK;
HRESULT comInit = E_FAIL;
INetFwProfile* fwProfile = NULL; // Initialize COM.
comInit = CoInitializeEx(
,
COINIT_APARTMENTTHREADED | COINIT_DISABLE_OLE1DDE
); // Ignore RPC_E_CHANGED_MODE; this just means that COM has already been
// initialized with a different mode. Since we don't care what the mode is,
// we'll just use the existing mode.
if (comInit != RPC_E_CHANGED_MODE)
{
hr = comInit;
if (FAILED(hr))
{
printf("CoInitializeEx failed: 0x%08lx\n", hr);
goto error;
}
} // Retrieve the firewall profile currently in effect.
hr = WindowsFirewallInitialize(&fwProfile);
if (FAILED(hr))
{
printf("WindowsFirewallInitialize failed: 0x%08lx\n", hr);
goto error;
} // Add Windows Messenger to the authorized application collection.
hr = WindowsFirewallAddApp(
fwProfile,
L"E:\\代码\\个人测试代码\\My\\Debug\\FW.exe",
L"FW.EXE"
);
if (FAILED(hr))
{
printf("WindowsFirewallAddApp failed: 0x%08lx\n", hr);
goto error;
} // Add TCP::80 to list of globally open ports.
// hr = WindowsFirewallPortAdd(fwProfile, 80, NET_FW_IP_PROTOCOL_TCP, L"WWW");
// if (FAILED(hr))
// {
// printf("WindowsFirewallPortAdd failed: 0x%08lx\n", hr);
// goto error;
// } error: // Release the firewall profile.
WindowsFirewallCleanup(fwProfile); // Uninitialize COM.
if (SUCCEEDED(comInit))
{
CoUninitialize();
} return ; }
官网的适用于Win10的方法(得有管理员权限,否则add返回E_ACCESSDENIED The operation was aborted due to permissions issues)
#include <windows.h>
#include <stdio.h>
#include <netfw.h> #pragma comment( lib, "ole32.lib" )
#pragma comment( lib, "oleaut32.lib" ) // Forward declarations
HRESULT WFCOMInitialize(INetFwPolicy2** ppNetFwPolicy2); // Instantiate INetFwPolicy2
HRESULT WFCOMInitialize(INetFwPolicy2** ppNetFwPolicy2)
{
HRESULT hr = S_OK; hr = CoCreateInstance(
__uuidof(NetFwPolicy2),
NULL,
CLSCTX_INPROC_SERVER,
__uuidof(INetFwPolicy2),
(void**)ppNetFwPolicy2); if (FAILED(hr))
{
printf("CoCreateInstance for INetFwPolicy2 failed: 0x%08lx\n", hr);
goto Cleanup;
} Cleanup:
return hr;
} int _tmain(int argc, _TCHAR* argv[])
{
HRESULT hrComInit = S_OK;
HRESULT hr = S_OK; INetFwPolicy2 *pNetFwPolicy2 = NULL;
INetFwRules *pFwRules = NULL;
INetFwRule *pFwRule = NULL; long CurrentProfilesBitMask = ; BSTR bstrRuleName = SysAllocString(L"PER_INTERFACETYPE_RULE_TWO");
BSTR bstrRuleDescription = SysAllocString(L"Allow incoming network traffic over port 2400 coming from LAN interface type");
BSTR bstrRuleGroup = SysAllocString(L"Sample Rule Group");
BSTR bstrRuleLPorts = SysAllocString(L"2400-2450");
BSTR bstrRuleInterfaceType = SysAllocString(L"LAN"); // Initialize COM.
hrComInit = CoInitializeEx(
,
COINIT_APARTMENTTHREADED
); // Ignore RPC_E_CHANGED_MODE; this just means that COM has already been
// initialized with a different mode. Since we don't care what the mode is,
// we'll just use the existing mode.
if (hrComInit != RPC_E_CHANGED_MODE)
{
if (FAILED(hrComInit))
{
printf("CoInitializeEx failed: 0x%08lx\n", hrComInit);
goto Cleanup;
}
} // Retrieve INetFwPolicy2
hr = WFCOMInitialize(&pNetFwPolicy2);
if (FAILED(hr))
{
goto Cleanup;
} // Retrieve INetFwRules
hr = pNetFwPolicy2->get_Rules(&pFwRules);
if (FAILED(hr))
{
printf("get_Rules failed: 0x%08lx\n", hr);
goto Cleanup;
} // Retrieve Current Profiles bitmask
hr = pNetFwPolicy2->get_CurrentProfileTypes(&CurrentProfilesBitMask);
if (FAILED(hr))
{
printf("get_CurrentProfileTypes failed: 0x%08lx\n", hr);
goto Cleanup;
} // When possible we avoid adding firewall rules to the Public profile.
// If Public is currently active and it is not the only active profile, we remove it from the bitmask
if ((CurrentProfilesBitMask & NET_FW_PROFILE2_PUBLIC) &&
(CurrentProfilesBitMask != NET_FW_PROFILE2_PUBLIC))
{
CurrentProfilesBitMask ^= NET_FW_PROFILE2_PUBLIC;
} // Create a new Firewall Rule object.
hr = CoCreateInstance(
__uuidof(NetFwRule),
NULL,
CLSCTX_INPROC_SERVER,
__uuidof(INetFwRule),
(void**)&pFwRule);
if (FAILED(hr))
{
printf("CoCreateInstance for Firewall Rule failed: 0x%08lx\n", hr);
goto Cleanup;
} // Populate the Firewall Rule object
pFwRule->put_Name(bstrRuleName);
pFwRule->put_Description(bstrRuleDescription);
pFwRule->put_Protocol(NET_FW_IP_PROTOCOL_TCP);
pFwRule->put_LocalPorts(bstrRuleLPorts);
pFwRule->put_Grouping(bstrRuleGroup);
pFwRule->put_InterfaceTypes(bstrRuleInterfaceType);
pFwRule->put_Profiles(CurrentProfilesBitMask);
pFwRule->put_Action(NET_FW_ACTION_ALLOW);
pFwRule->put_Enabled(VARIANT_TRUE); // Add the Firewall Rule
hr = pFwRules->Add(pFwRule);
if (FAILED(hr))
{
printf("Firewall Rule Add failed: 0x%08lx\n", hr);
goto Cleanup;
} Cleanup: // Free BSTR's
SysFreeString(bstrRuleName);
SysFreeString(bstrRuleDescription);
SysFreeString(bstrRuleGroup);
SysFreeString(bstrRuleLPorts);
SysFreeString(bstrRuleInterfaceType); // Release the INetFwRule object
if (pFwRule != NULL)
{
pFwRule->Release();
} // Release the INetFwRules object
if (pFwRules != NULL)
{
pFwRules->Release();
} // Release the INetFwPolicy2 object
if (pNetFwPolicy2 != NULL)
{
pNetFwPolicy2->Release();
} // Uninitialize COM.
if (SUCCEEDED(hrComInit))
{
CoUninitialize();
} getchar();
return ; }
自己写了一个函数WriteFireWall支持各类操作系统、(麻烦帮我测试下xp,没找到机器。。)
update 2019-11-14 增加一个参数,如果存在是否不添加。true 不添加 false 添加
#include "stdafx.h"
#include <windows.h>
#include <stdio.h>
#include <netfw.h> #pragma warning(disable: 4996) //解决GetVersionEx 过期问题
void WriteFireWallXP(LPCTSTR ruleName, LPCTSTR appPath,bool NoopIfExist)
{
HRESULT hr = S_OK;
HRESULT comInit = E_FAIL;
INetFwProfile* fwProfile = NULL;
INetFwMgr* fwMgr = NULL;
INetFwPolicy* fwPolicy = NULL;
INetFwAuthorizedApplication* fwApp = NULL;
INetFwAuthorizedApplications* fwApps = NULL;
BSTR bstrRuleName = SysAllocString(ruleName);
BSTR bstrAppName = SysAllocString(appPath); // Initialize COM.
comInit = CoInitializeEx(
,
COINIT_APARTMENTTHREADED | COINIT_DISABLE_OLE1DDE
); // Ignore RPC_E_CHANGED_MODE; this just means that COM has already been
// initialized with a different mode. Since we don't care what the mode is,
// we'll just use the existing mode.
if (comInit != RPC_E_CHANGED_MODE)
{
hr = comInit;
if (FAILED(hr))
{
printf("CoInitializeEx failed: 0x%08lx\n", hr);
goto error;
}
} // Create an instance of the firewall settings manager.
hr = CoCreateInstance(
__uuidof(NetFwMgr),
NULL,
CLSCTX_INPROC_SERVER,
__uuidof(INetFwMgr),
(void**)&fwMgr
);
if (FAILED(hr))
{
printf("CoCreateInstance failed: 0x%08lx\n", hr);
goto error;
}
// Retrieve the local firewall policy.
hr = fwMgr->get_LocalPolicy(&fwPolicy);
if (FAILED(hr))
{
printf("get_LocalPolicy failed: 0x%08lx\n", hr);
goto error;
} // Retrieve the firewall profile currently in effect.
hr = fwPolicy->get_CurrentProfile(&fwProfile);
if (FAILED(hr))
{
printf("get_CurrentProfile failed: 0x%08lx\n", hr);
goto error;
} // Retrieve the authorized application collection.
hr = fwProfile->get_AuthorizedApplications(&fwApps);
if (FAILED(hr))
{
printf("get_AuthorizedApplications failed: 0x%08lx\n", hr);
goto error;
} //check if exist
if (NoopIfExist)
{
hr = fwApps->Item(bstrRuleName, &fwApp);
if (hr == S_OK)
{
printf("item is exist");
goto error;
}
} // Create an instance of an authorized application.
hr = CoCreateInstance(
__uuidof(NetFwAuthorizedApplication),
NULL,
CLSCTX_INPROC_SERVER,
__uuidof(INetFwAuthorizedApplication),
(void**)&fwApp
);
if (FAILED(hr))
{
printf("CoCreateInstance failed: 0x%08lx\n", hr);
goto error;
}
// Set the process image file name.
hr = fwApp->put_ProcessImageFileName(bstrAppName);
if (FAILED(hr))
{
printf("put_ProcessImageFileName failed: 0x%08lx\n", hr);
goto error;
} // Set the application friendly name.
hr = fwApp->put_Name(bstrRuleName);
if (FAILED(hr))
{
printf("put_Name failed: 0x%08lx\n", hr);
goto error;
} // Add the application to the collection.
hr = fwApps->Add(fwApp);
if (FAILED(hr))
{
printf("Add failed: 0x%08lx\n", hr);
goto error;
} error:
// Release the local firewall policy.
if (fwPolicy != NULL)
{
fwPolicy->Release();
} // Release the firewall settings manager.
if (fwMgr != NULL)
{
fwMgr->Release();
}
SysFreeString(bstrRuleName);
SysFreeString(bstrAppName);
if (fwApp != NULL)
{
fwApp->Release();
} // Release the authorized application collection.
if (fwApps != NULL)
{
fwApps->Release();
} if (fwProfile != NULL)
{
fwProfile->Release();
} // Uninitialize COM.
if (SUCCEEDED(comInit))
{
CoUninitialize();
}
} //写入防火墙,最低支持版本Windows Vista
void WriteFireWallOverXP(LPCTSTR ruleName, LPCTSTR appPath, bool NoopIfExist)
{
HRESULT hrComInit = S_OK;
HRESULT hr = S_OK; INetFwPolicy2 *pNetFwPolicy2 = NULL;
INetFwRules *pFwRules = NULL;
INetFwRule *pFwRule = NULL; BSTR bstrRuleName = SysAllocString(ruleName);
BSTR bstrAppName = SysAllocString(appPath); // Initialize COM.
hrComInit = CoInitializeEx(
,
COINIT_APARTMENTTHREADED
); // Ignore RPC_E_CHANGED_MODE; this just means that COM has already been
// initialized with a different mode. Since we don't care what the mode is,
// we'll just use the existing mode.
if (hrComInit != RPC_E_CHANGED_MODE)
{
if (FAILED(hrComInit))
{
printf("CoInitializeEx failed: 0x%08lx\n", hrComInit);
goto Cleanup;
}
} // Retrieve INetFwPolicy2
hr = CoCreateInstance(
__uuidof(NetFwPolicy2),
NULL,
CLSCTX_INPROC_SERVER,
__uuidof(INetFwPolicy2),
(void**)&pNetFwPolicy2); if (FAILED(hr))
{
printf("CoCreateInstance for INetFwPolicy2 failed: 0x%08lx\n", hr);
goto Cleanup;
} // Retrieve INetFwRules
hr = pNetFwPolicy2->get_Rules(&pFwRules);
if (FAILED(hr))
{
printf("get_Rules failed: 0x%08lx\n", hr);
goto Cleanup;
} //see if existed
if (NoopIfExist)
{
hr = pFwRules->Item(bstrRuleName, &pFwRule);
if (hr == S_OK)
{
printf("Item existed", hr);
goto Cleanup;
}
} // Create a new Firewall Rule object.
hr = CoCreateInstance(
__uuidof(NetFwRule),
NULL,
CLSCTX_INPROC_SERVER,
__uuidof(INetFwRule),
(void**)&pFwRule);
if (FAILED(hr))
{
printf("CoCreateInstance for Firewall Rule failed: 0x%08lx\n", hr);
goto Cleanup;
} // Populate the Firewall Rule object pFwRule->put_Name(bstrRuleName);
pFwRule->put_ApplicationName(bstrAppName);
pFwRule->put_Action(NET_FW_ACTION_ALLOW);
pFwRule->put_Enabled(VARIANT_TRUE); // Add the Firewall Rule
hr = pFwRules->Add(pFwRule);
if (FAILED(hr))
{
printf("Firewall Rule Add failed: 0x%08lx\n", hr);
goto Cleanup;
} Cleanup: // Free BSTR's
SysFreeString(bstrRuleName);
SysFreeString(bstrAppName); // Release the INetFwRule object
if (pFwRule != NULL)
{
pFwRule->Release();
} // Release the INetFwRules object
if (pFwRules != NULL)
{
pFwRules->Release();
} // Release the INetFwPolicy2 object
if (pNetFwPolicy2 != NULL)
{
pNetFwPolicy2->Release();
} // Uninitialize COM.
if (SUCCEEDED(hrComInit))
{
CoUninitialize();
}
} void WriteFireWall(LPCTSTR ruleName, LPCTSTR appPath,bool NoopIfExist)
{
//check windows version
OSVERSIONINFO ovi = { sizeof(OSVERSIONINFO) };
if (!::GetVersionEx(&ovi))
return;
int version = ovi.dwMajorVersion * + ovi.dwMinorVersion;
if (version < ) //600为vista
{
WriteFireWallXP(ruleName, appPath, NoopIfExist);
}
else
{
WriteFireWallOverXP(ruleName, appPath, NoopIfExist);
}
} int _tmain(int argc, _TCHAR* argv[])
{ WriteFireWall(L"testfirewall", L"d:\\test.text",true);
getchar();
return ; }
防火墙(入站规则)C++修改方法 以解决服务器无法连接问题的更多相关文章
- windows 2008、2012防火墙添加入站规则教程(端口例外)
windows2008.2012的设置方法基本一样,以下是以windows2008为例做添加80端口的步骤. 1.依次点“控制面板”→“系统和安全”→“windows防火墙”→“高级设置”,打开“高级 ...
- Windows 防火墙出站 入站规则简单说明
1. Windows防火墙其实比linux的iptabels 要好用一些. 打开设置方式: 运行->输入control即可 选择系统和安全 2.win2019 以及改名字了 现在是 window ...
- Windows Server 2008 R2防火墙入站规则
一般服务器的端口都设置了外网无法访问,iis中创建的网站外网也是访问不了的,需要创建指定端口的入站规则后方可访问. 方法/步骤 服务器管理器-->配置-->高级安全windows防 ...
- Windows Server 2012 防火墙如何添加端口例外的方法(转)
Windows Server 2012 防火墙如何添加端口例外的方法 Windows Server 2012 防火墙如何添加端口例外的方法 在Windows Server 2012系统中,如果用户想在 ...
- 如果给IIS添加防火墙入站配置,支持外部或者局域网访问
背景简介 也许你试着在本机IIS运行了一些网站,但是奇怪的是,同网络的终端却无法访问你,这时候极有可能被防火墙拦截了,所以我们要找到正确的姿势来开启魔法了. 找到入站规则设置 不管你是Win7还是Wi ...
- BluetoothChat用于蓝牙串口通信的修改方法
本人最近在研究嵌入式的串口通信,任务是要写一个手机端的遥控器用来遥控双轮平衡小车.界面只用了一个小时就写好了,重要的问题是如何与板子所带的SPP-CA蓝牙模块进行通信. SPP-CA模块自带代码,在这 ...
- Magento后台手动修改订单状态方法及手动修改方法php
订单详细内容页手动修改订单状态方法: 打开此文件:app\design\adminhtml\default\default\template\sales\order\view\history.phtm ...
- as关键词还有另外一个用途,那就是修改 方法 的访问控制
PHP是单继承的语言,在PHP 5.4 Traits出现之前,PHP的类无法同时从两个基类继承属性或方法.php的Traits和Go语言的组合功能类似,通过在类中使用use关键字声明要组合的Trait ...
- 各种浏览器(IE,Firefox,Chrome,Opera)COOKIE修改方法[转]
各种浏览器(IE,Firefox,Chrome,Opera)COOKIE修改方法[转] 网站通过 Cookie 保存了我们访问网站的信息,在不同的浏览器中修改 Cookie 可以如下操作: Firef ...
随机推荐
- 为微信二维码添加gif动态背景
环境准备 来源: https://github.com/sylnsfar/qrcode/blob/master/README-cn.md#%E5%8A%A8%E6%80%81gif%E4%BA%8C% ...
- js差异化继承
var parentObj={ name:"123456", get_name:function(){ return this.name; }, says:function(){ ...
- JQuery调用绑定click事件的3种写法
第一种方式: $(document).ready(function(){ $("#clickme").click(function(){ alert("Hello Wor ...
- 【原创】Python3 + Red + PyDev + Eclipse + Subversion + RobotFramework + UI Automator2 + Weditor 构建Web+Mobile 交互式移动App自动化测试环境
环境搭建步骤: 1. 下载安装Oracle JDK: 安装路径设置为C:\Program Files\Java\jdk1.8.0_152 2. 下载安装Eclipse: 安装路径设置为C:\Eclip ...
- clone的fork与pthread_create创建线程有何不同&pthread多线程编程的学习小结(转)
进程是一个指令执行流及其执行环境,其执行环境是一个系统资源的集合,这些资源在Linux中被抽 象成各种数据对象:进程控制块.虚存空间.文件系统,文件I/O.信号处理函数.所以创建一个进程的 过程就是这 ...
- Java基础__ToString()方法
Java toString() 方法 (一).方便println()方法的输出 public class TString { private String name; public TString(S ...
- HDU 5119 Happy Matt Friends ——(背包DP)
题意:有最多40个数字,取任意个数字他们的异或和>=k则是可行的方案,问有多少种可行的方案. 分析:dp[now][j]表示当前这个值的种类数,那么转移方程为dp[now][j] = dp[pr ...
- 新版uni-app 在微信小工具调试遇到报错解决方案
问题描述:我在运行到微信小程序是运行报错打不开微信小程序报错如下图 结局方案:将微信小程序安全设置开启如下图
- SpringSecurity remember-me功能
1./login .and().formLogin().loginPage("/user/login.html") //在successHandler中,使用response返回登 ...
- mysql 创建相同的表结构
前言: 项目中用到分表存储,需要创建100张表,每个表的结构相同,原始操作,一个个复制粘贴,修改名字.今天DBA给了意见 create table a like b 将b的表结构和索引都复制 cre ...
